Introduction
I previously posted a blog post showing you how your users can decommission their old domain joined PC using the Retire My PC app. I showed you how to create the app and deploy it via Software Center to your users’ old computer. The reason why this app exists is to allow users to decommission their old PC when it suits them and not have to rely on onsite support staff or a third party service to secure company data stored on the old PC before it gets returned to the vendor or seller. This is achieved by ensuring the device is protected by Bitlocker and then deleting the Bitlocker protector from the TPM prior to shutting down the device. There is much more going on in the app, please see the list of original features below.
- stops the ConfigMgr client agent service (if one is running)
- stops the MBAM agent service (if one is running)
- rotates the BitLocker key (optional)
- WIPEs the BCD registry entries (optional)
- joins a workgroup
- clears the Bitlocker TPM protector
- adds a record of all this to Azure Tables
- emails the log to a support inbox
In this blog post I’ll show you how to deploy a newer, more secure version of the app via the Company Portal in Microsoft Endpoint Manager (Microsoft Intune) which can be used on Intune managed, Azure AD joined computers.
This version of the app has some new abilities which are highlighted below.
- Available in Company Portal
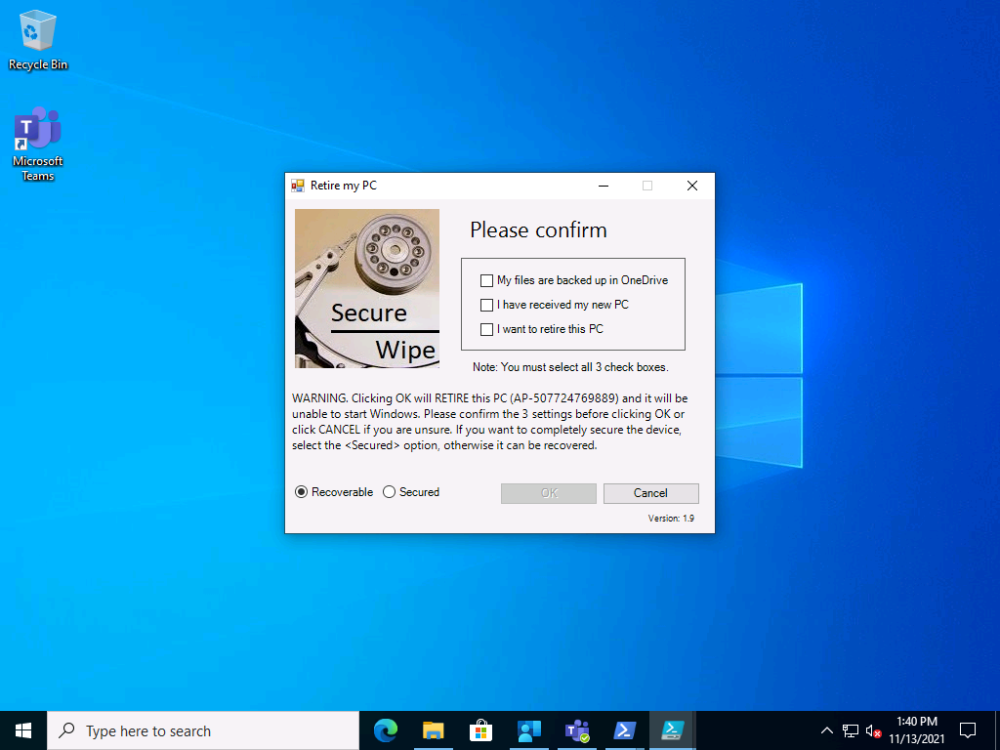
- Allows the user to select the type of decommission (Recoverable or Secured)
- If the Recoverable option is selected, the Bitlocker protector is removed from the TPM. If a support technician or the end user has access to the recovery password info, they can enter it at the boot screen and therefore can boot back into Windows.
- If the Secured option is selected, not only is the Bitlocker protector removed from the TPM but the Bitlocker key is rotated and the new key is not uploaded to Azure AD, or ConfigMgr or MBAM. Therefore the admin and the end user will not have the recovery info needed to boot the computer. In addition, the BDE registry keys are completely wiped out, so even if they manage to get the rotated key (from the email sent to the configured support inbox, read the NOTE below) this would only allow file access, Windows will not boot.
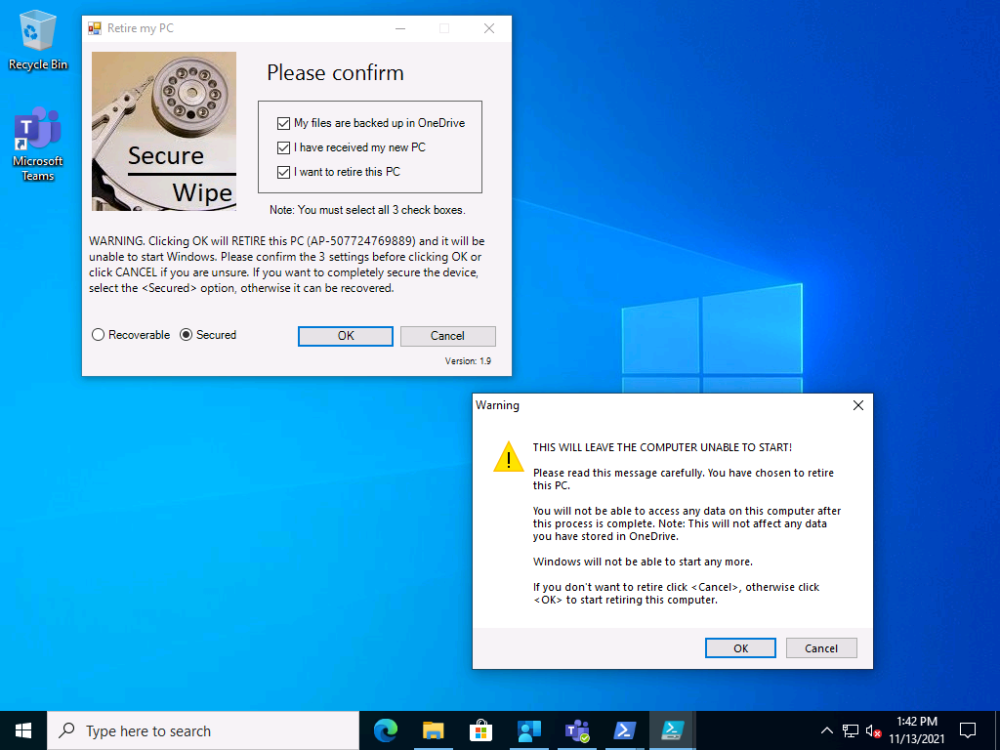
- Regardless of which option the user chooses, the device will NOT boot into Windows after it’s retired as it cannot due to the missing Bitlocker protector in the TPM, and this secures the PC from unwanted access.
- However, if the user selects cancel in the main UI, the detection method file is removed so they can reinstall the app on-demand via Company Portal.
NOTE: You can also modify the script to not include the rotated recovery key information in the email making the device very secure indeed. If you do this, the device (and the data on it) can never be recovered as the rotated Bitlocker key is not stored anywhere. As this is so drastic, I’ve left this recovery info in the email. This email will never be seen by the end user and is sent to a shared help desk inbox. Once you are happy with the way things are going, you can optionally remove this info from the log to ensure company data is 100% secured on decommissioned devices.
Before starting, please read the original Retire My PC blog post to get an understanding of how to set this all up. You can skip the creation of the app in ConfiMgr if you are using this in cloud only environments.
Step 1. Get the scripts
Note: You can only download these files when logged on to https://www.windows-noob.com
Download, unzip and extract the files.
Step 2. Get ServiceUI.exe from MDT
You’ll need the ServiceUI.exe executable file to display user interfaces (UI) to end users when operating in SYSTEM context. To get the file, download and install MDT somewhere and navigate to C:\Program Files\Microsoft Deployment Toolkit\Templates\Distribution\Tools\x64. To download MDT click here.
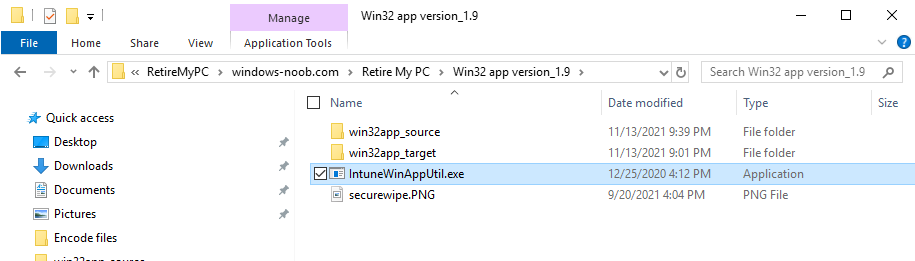
Copy the 64 bit version of ServiceUI.exe file to your extracted win32app_source folder so it looks like this.
Step 3. Get the Win32 content prep tool
Download the Win32 content prep tool from here.
Copy the IntuneWinAppUtil.exe file to your Retire My PC source folder, it should look like this.
Step 4. Modify the script
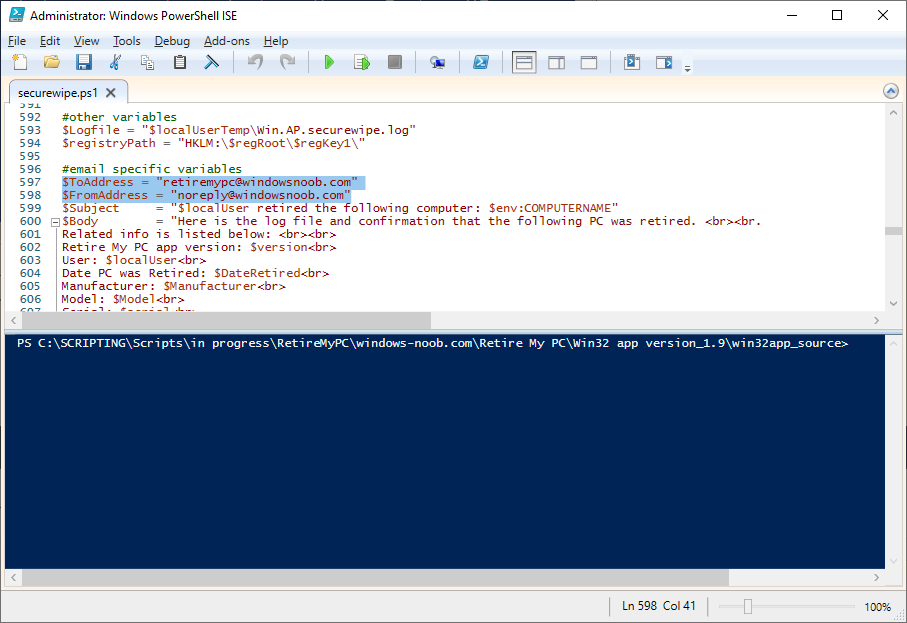
Open the securewipe.ps1 script. Configure the $ToAddress and $FromAddress variables.
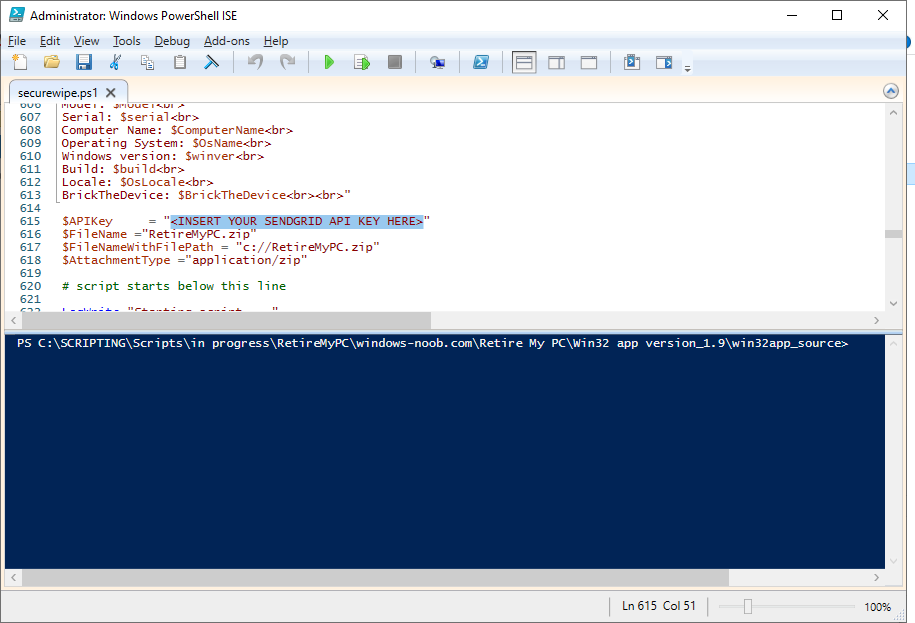
Using your Sendgrid API key, paste your API key value (line 615 below).
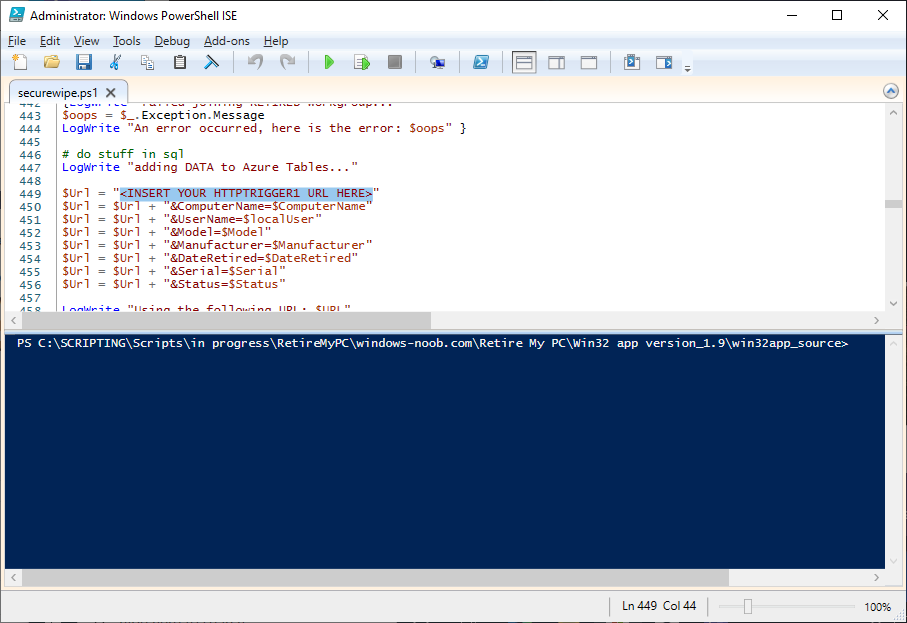
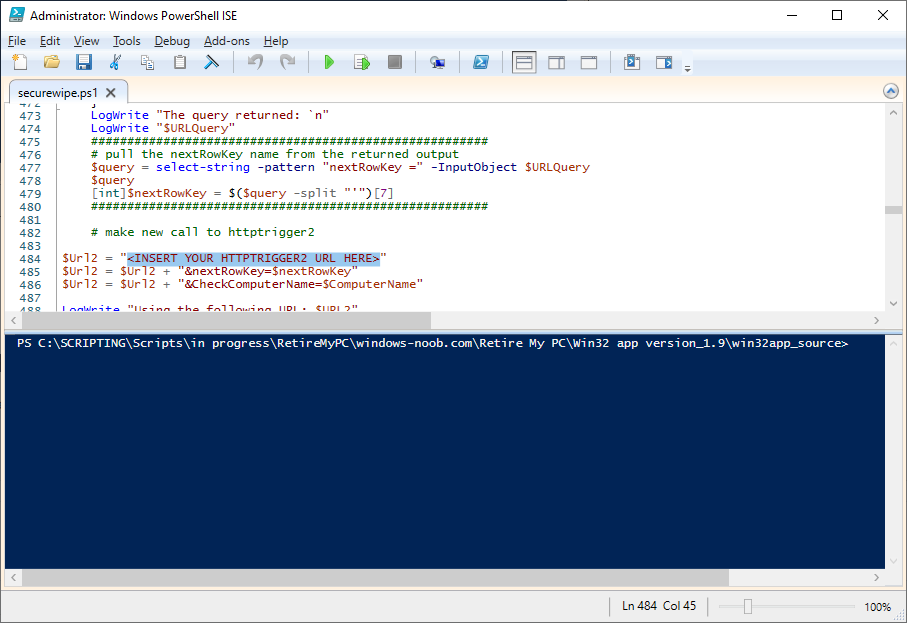
add your httptrigger2 url here
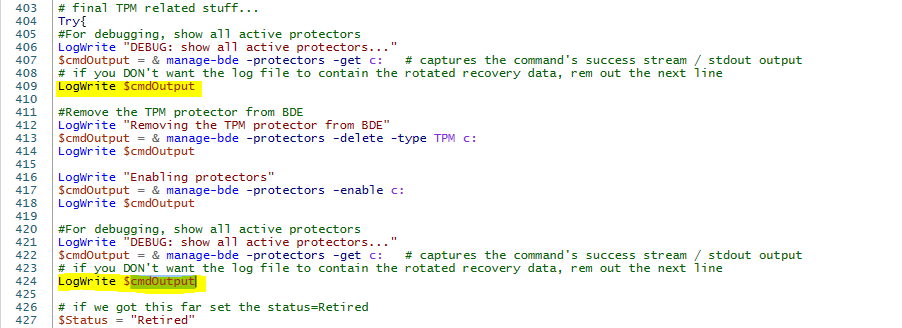
If you want to completely remove the rotated key from the email, rem out the following lines marked in yellow
Save the changes to the script.
Step 5. Create the Intunewin package
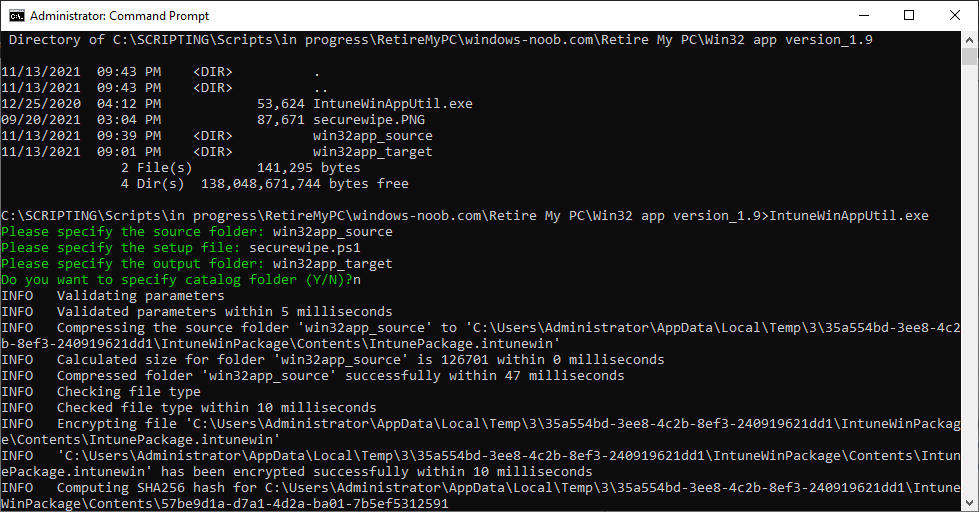
Open a command prompt and browse to the reset-windows folder structure. Launch the IntuneWinAppUtil.exe file and answer the following.
- Please specify the source folder: win32app_source
- Please specify the setup file: securewipe.ps1
- Please specify the output folder: win32app_target
- Do you want to specify catalog folder (Y/N)? n
as shown here.
After doing that you’ll have the securewipe.intunewin file in the win32app_target folder.
Step 6. Create the Win32 app in Endpoint Manager
Log into https://endpoint.microsoft.com and add a new Win32 App. Below are some screenshots showing how I’ve configured the app.
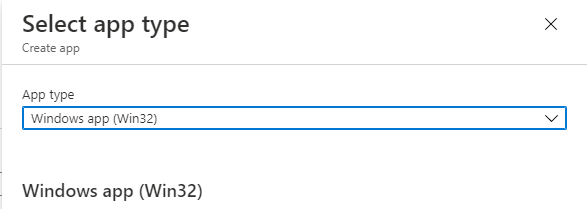
For Select app type, select Windows app (Win32) from the drop down menu
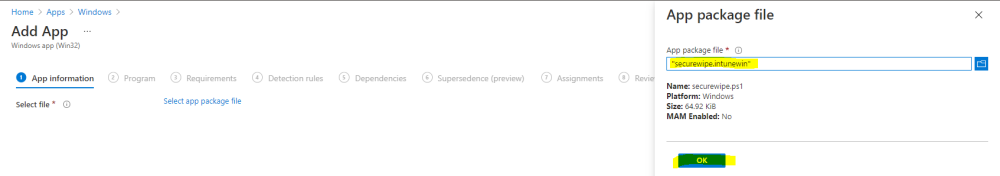
Click on Select app package file and point it to the securewipe.intunewin file in the win32app_target folder.
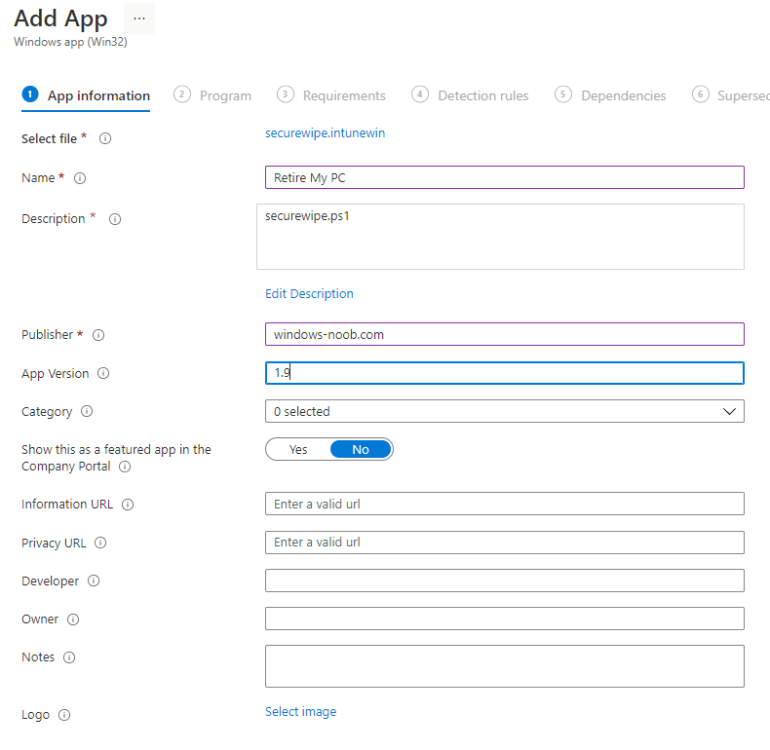
fill in some info about the app
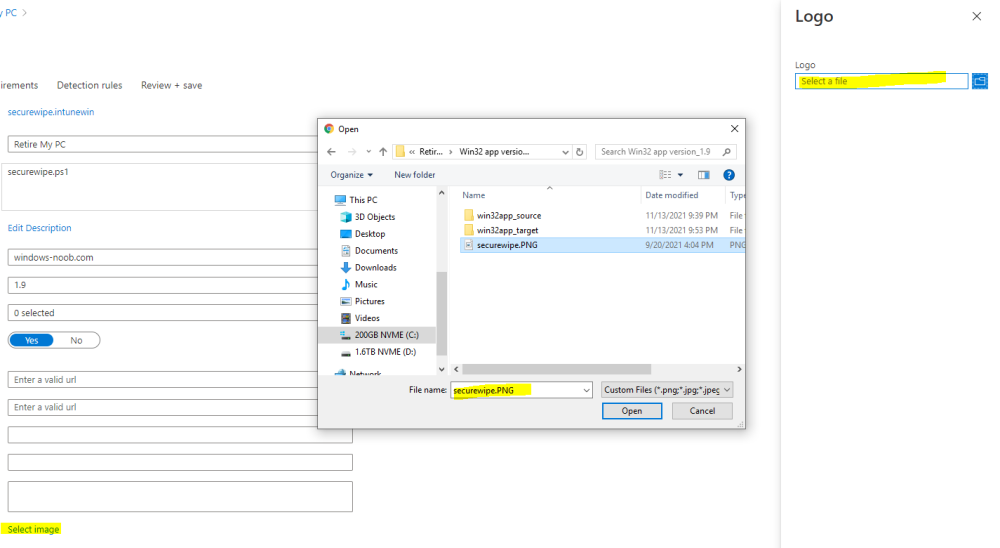
for the logo, click on Select image and point it here…
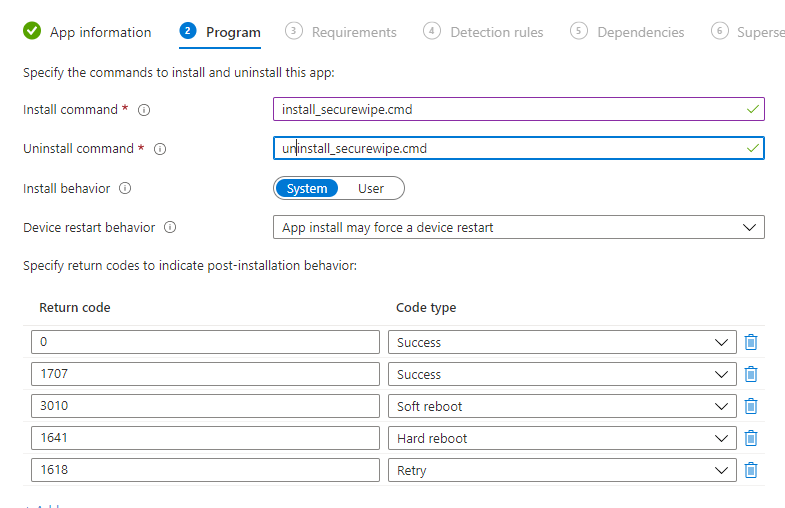
fill in the install commands
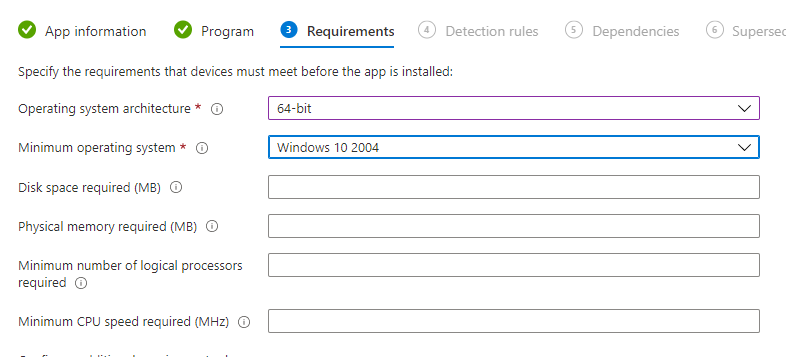
fill in the requirements
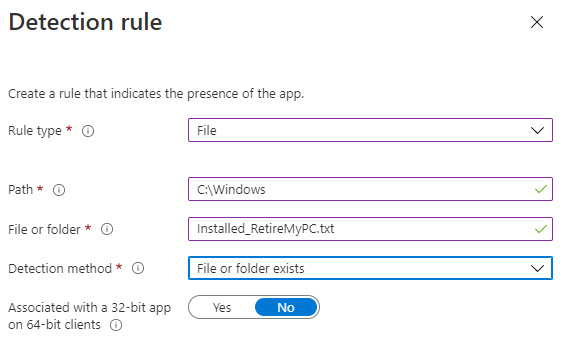
and the detection rules..
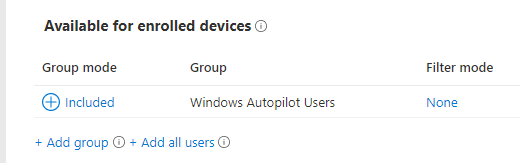
finally deploy it to your users that should be retiring old pc’s…
and save the app.
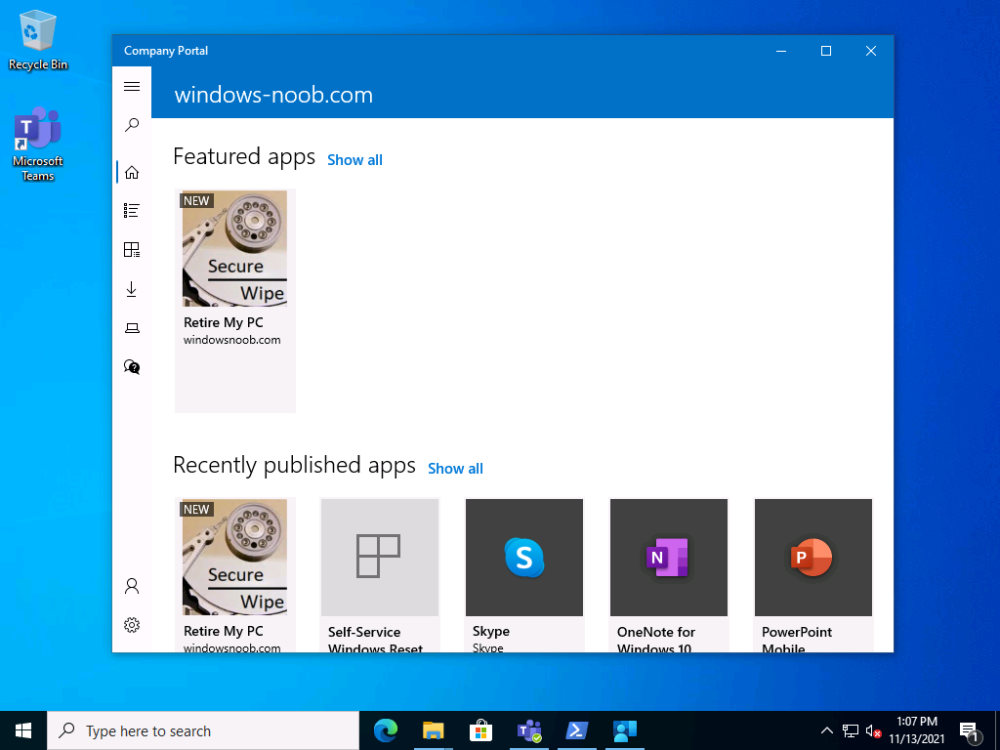
This is what the end user will see after launching the app from the Company Portal
once they make their selections and clicking OK
clicking OK to this warning will start the process and some seconds later the device will no longer be able to boot.
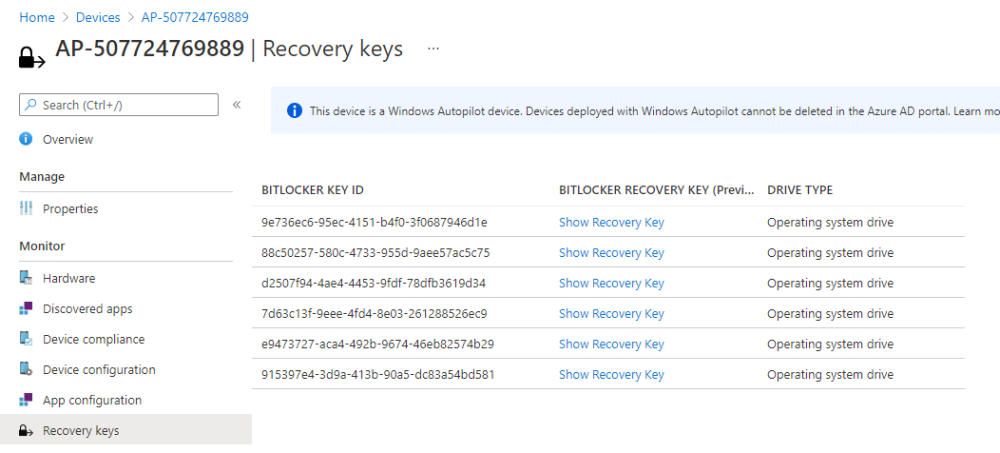
The recovery key data stored in Microsoft Endpoint Manager will not contain the latest rotated key from the device if the user selected the <Secured> option.
The only place you’ll find the recovery key data, is in the email sent to the shared help desk inbox if you optionally decided to include that info.
The app logs to C:\Users\<USERNAME>\AppData\Local\Temp\win.ap.securewipe.log and this log file is emailed to your shared help desk email inbox.
Job done !