Introduction
If you’ve been looking at my guides, you’ll know that I’ve used httptriggers in functionapps to add functionality to Windows Autopilot, below are some examples of that.
- Adding devices to an Azure AD group after Windows Autopilot is complete – part 1
- Adding devices to an Azure AD group after Windows Autopilot is complete – part 2
- Gathering logs and sending an email when resetting Windows Autopilot – part 1
- Gathering logs and sending an email when you need to reset Windows Autopilot – part 2
- Gathering logs and sending an email when you need to reset Windows Autopilot – part 3
- Adding devices or users to an Azure AD group after Windows Autopilot is complete but only when the device is marked as Compliant
- Using the updated & secure Retire My PC app via Company Portal
These work great, but for security reasons the secret attached to the function app itself will expire (after 6 months by default) and should be renewed before that time. Trust me, I learned the hard way.
Discovering the problem
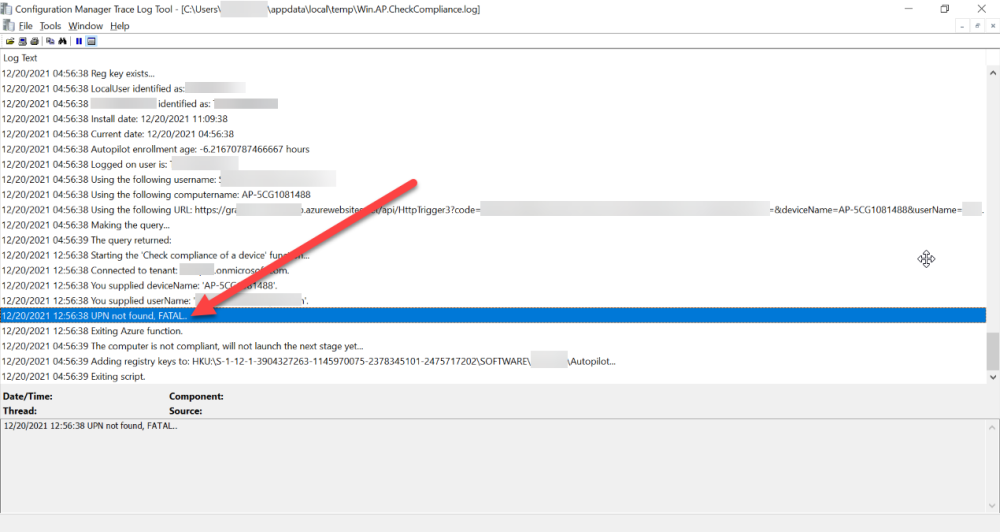
You might forget to renew the secret and that’s when you’ll notice things not behaving the way they should. I first became aware of the problem before Christmas, I came into work on the Monday, and kicked off some Windows Autopilot installs but they didn’t work correctly. I noticed that the triggers responsible for adding devices to Azure AD groups after Windows Autopilot is complete, but only when the device is marked as compliant were no longer working. I started my investigation on a client with the issue, and the following was reported in the log file. One line jumped out at me, UPN not found, FATAL.
Yeah, that doesn’t sound good.
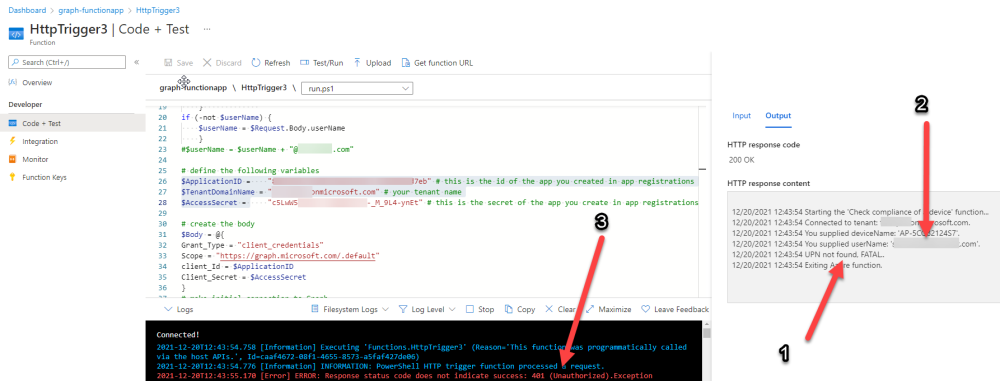
I then logged into Azure and found the trigger responsible. I fed it with some known good values and looked at the output. The first thing to note is it output the same error (1), even though I supplied a known good UPN (2). Therefore, I knew the error UPN not found, FATAL was a red-herring. I also noticed that there were error code 401 (unauthorized) in the console output (3). That was my first clue !
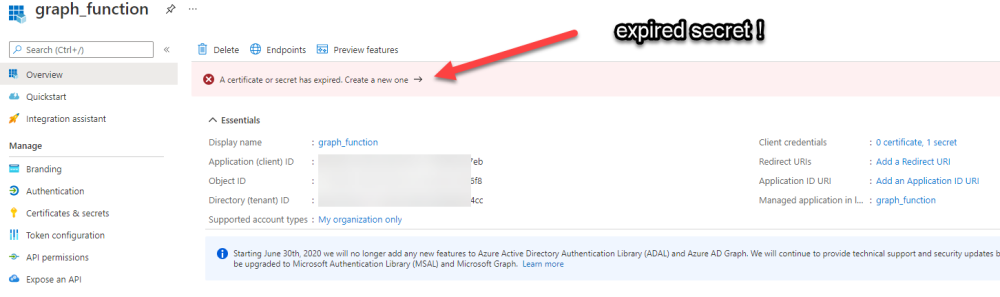
Next, I select App Registrations in Azure Active Directory, selected the Graph_function app and was greeted with a red error on top showing me that a certificate or secret had expired.
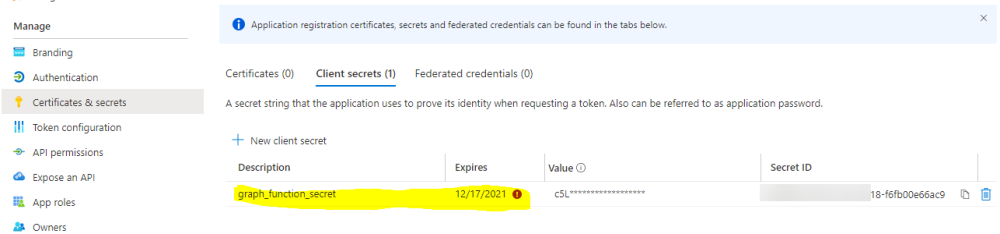
Clicking on Certificates and secrets, showed the expired secret.
Fixing expired secrets
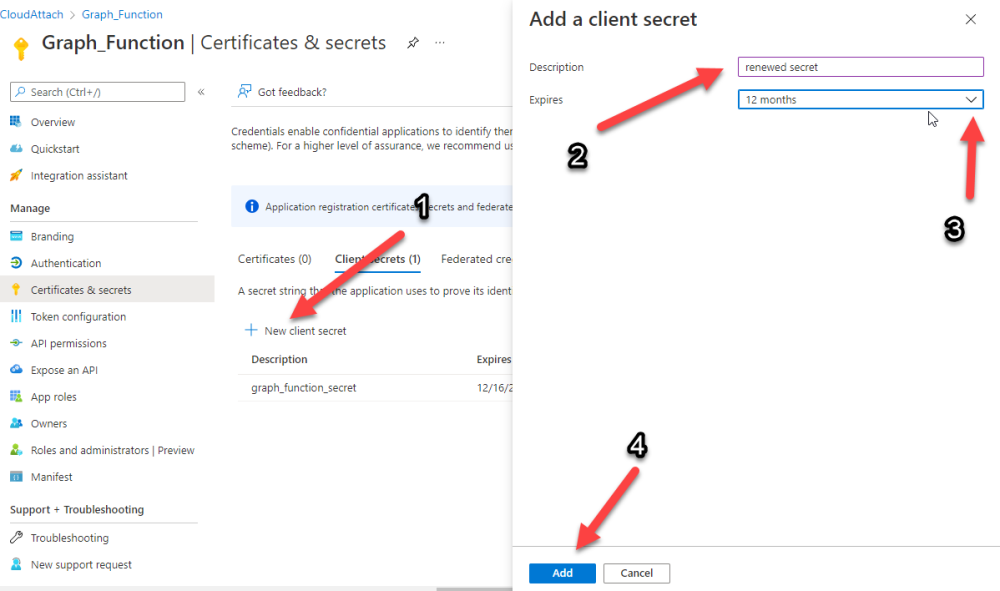
Now that I identified the problem, it was time to fix it. In the Certificates & secrets section, click on + New client secret (1), give it a suitable name (2), select when it expires from the drop down menu (3) and finally Add it (4).
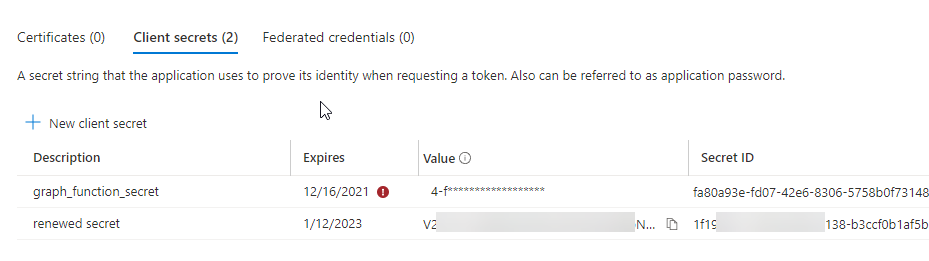
The new secret will appear. Notice the expiry date.
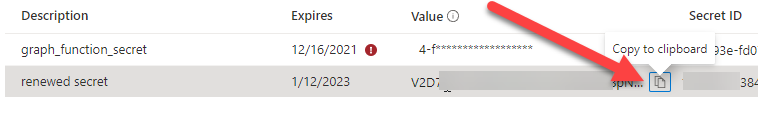
Now, copy the new secret value.
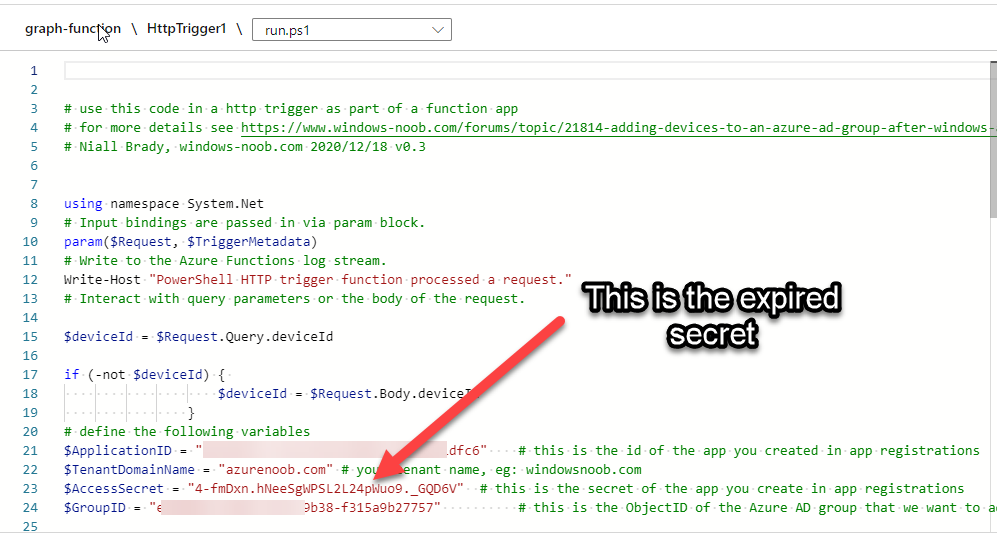
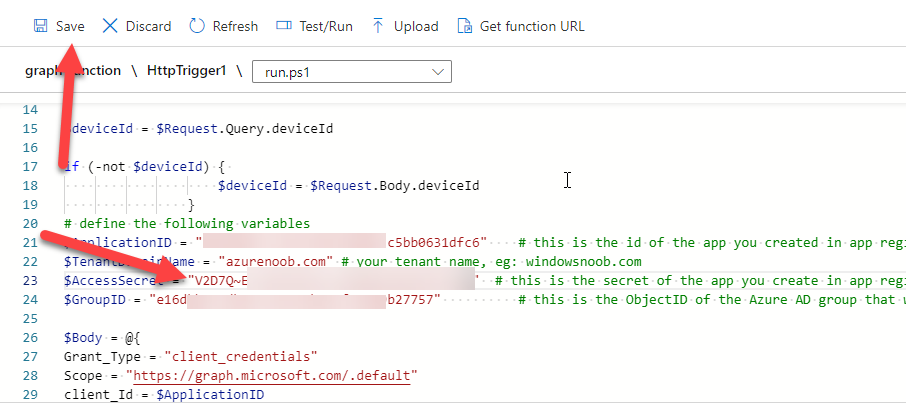
Next, locate the trigger(s) that use the previous secret. It’s stored as $AccessSecret in my httptrigger examples.
Replace that expired value with the value you copied from the newly created secret and then save your changes.
Job done !
Repeat the above exercise for each trigger that uses the expired secret.
Conclusion
Nothing lasts forever, especially secrets. Now that you know how to renew your expired secrets, maybe it’s a good idea to look at your app registrations and take note of when they expire, and pro-actively renew them before they expire next time ! If you’d like to automate that take a look at Peter Klapwijk’s post here.