Introduction
Microsoft recently released Configuration Manager Technical Preview version 1909 which contained updates to the integrated MBAM functionality within Configuration Manager and I blogged about that here, those updates included Self Service and Help Desk abilities as well as updates to Reporting.
In a previous blog post you looked at the Self Service feature for end users and then you looked at the Help Desk feature. But what happens on the client and in the database once the recovery key has been disclosed (via the Help Desk)?
The Recovery Key and Recovery Key ID will rotate.
Note: Disclosing the Recovery Key using Self Service does not cause the key to rotate.
What is Key Rotation
Key rotation allows admins to use a single-use key (via the Help Desk) for unlocking a BitLocker encrypted device. Once this key is used, a new key will be generated for the device and stored securely on-premises in the ConfigMgr Database.
Source – https://techcommunity.microsoft.com/t5/Enterprise-Mobility-Security/Microsoft-expands-BitLocker-management-capabilities-for-the/ba-p/544329
Note: Additions from me in Italics.
This helps to prevent a rogue Help Desk user from trying to decrypt contents of a BitLockered computer without permission, because once the Recovery Key is given to the user via the Help Desk, it is then rotated on the Client and the new Recovery Key and Recovery Key ID are transferred to the Server, and therefore the old Recovery key becomes useless.
A deeper look at Key Rotation
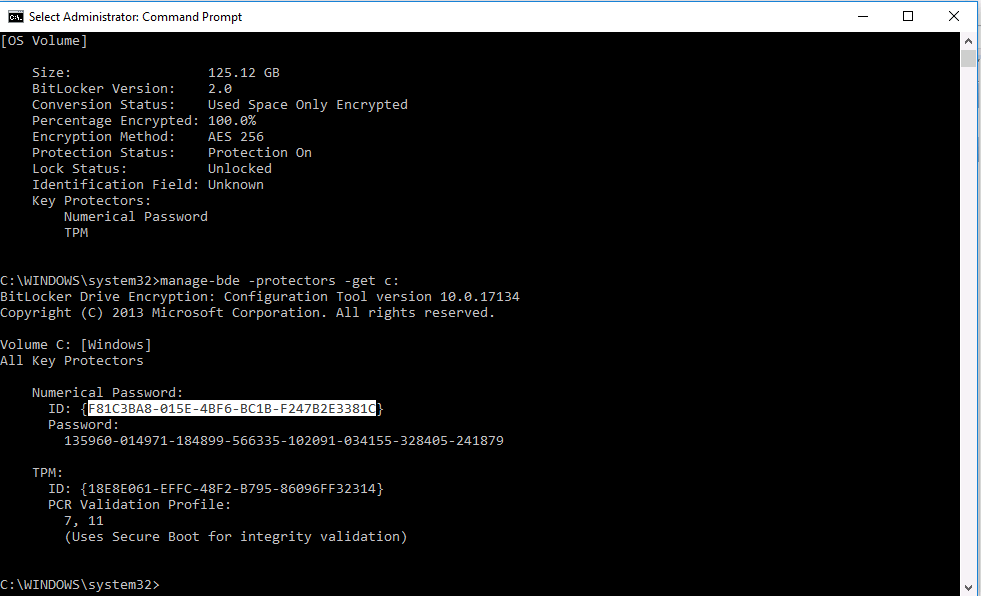
Before a Recovery Key is rotated, you can find out what values you have on a client by issuing the following command in an Administrative command prompt.
Manage-bde -protectors -get c:
The first 8 characters of the Numerical Password listed below (Numerical Password is essentially the Recovery Key ID in SQL) are used to unlock drives that are in BitLocker Recovery mode via the Help Desk feature (or Self Service).
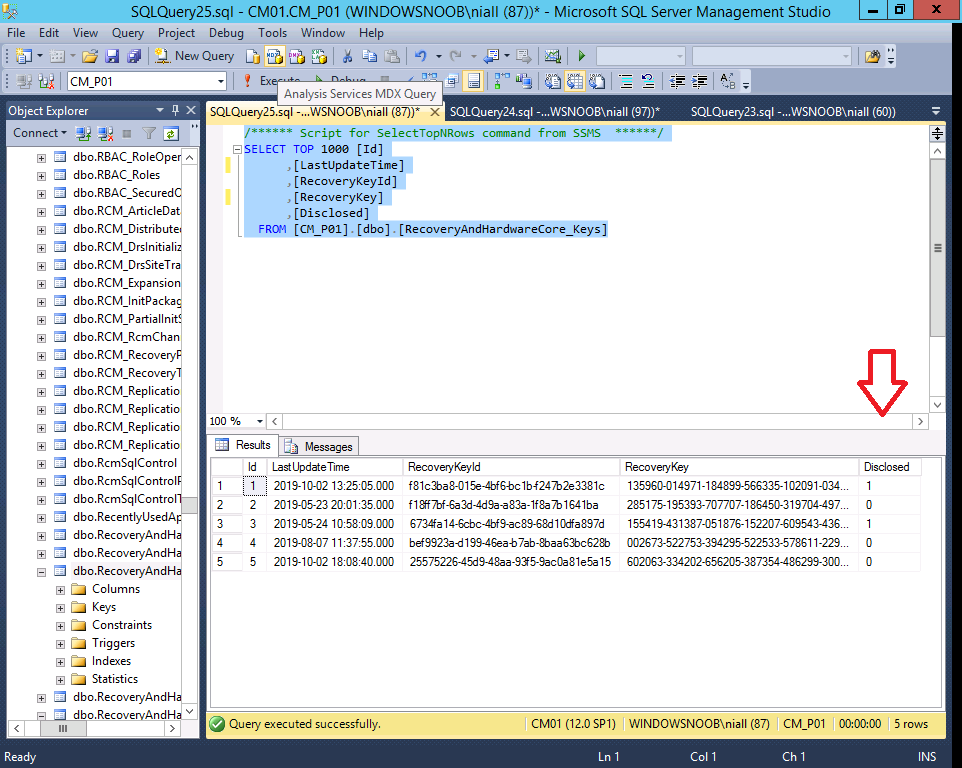
If you then look in SQL Server on the computer hosting the ConfigMgr database, you can view recently used Recovery Key ID’s and associated Recovery Key’s and whether they were disclosed or not via the Disclosed column.
/****** Script for SelectTopNRows command from SSMS ******/ SELECT TOP 1000 [Id] ,[LastUpdateTime] ,[RecoveryKeyId] ,[RecoveryKey] ,[Disclosed] FROM [CM_P01].[dbo].[RecoveryAndHardwareCore_Keys]
Note: Change the CM_P01 to match your own ConfigMgr database name. If a Recovery Key has been disclosed (by a Help Desk user) it will have a value of 1.
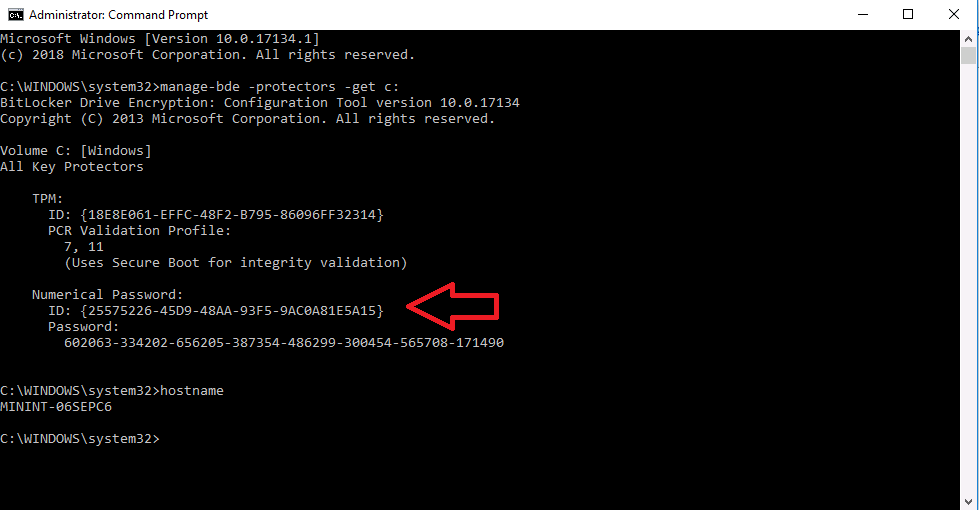
 Once a Recovery Key has been disclosed using the Help Desk feature, the MBAM agent on the client computer will force it to rotate, and below you can see the new recovery id and recovery password on the host below.
Once a Recovery Key has been disclosed using the Help Desk feature, the MBAM agent on the client computer will force it to rotate, and below you can see the new recovery id and recovery password on the host below.
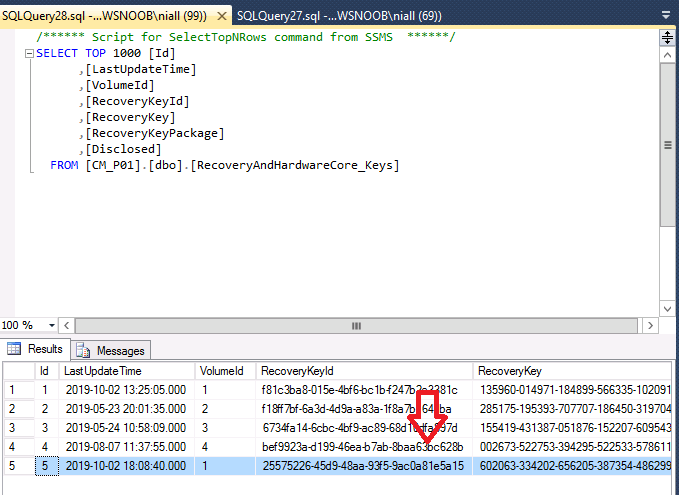
 And those new values are transferred (escrowed) to the ConfigMgr database in SQL.
And those new values are transferred (escrowed) to the ConfigMgr database in SQL.
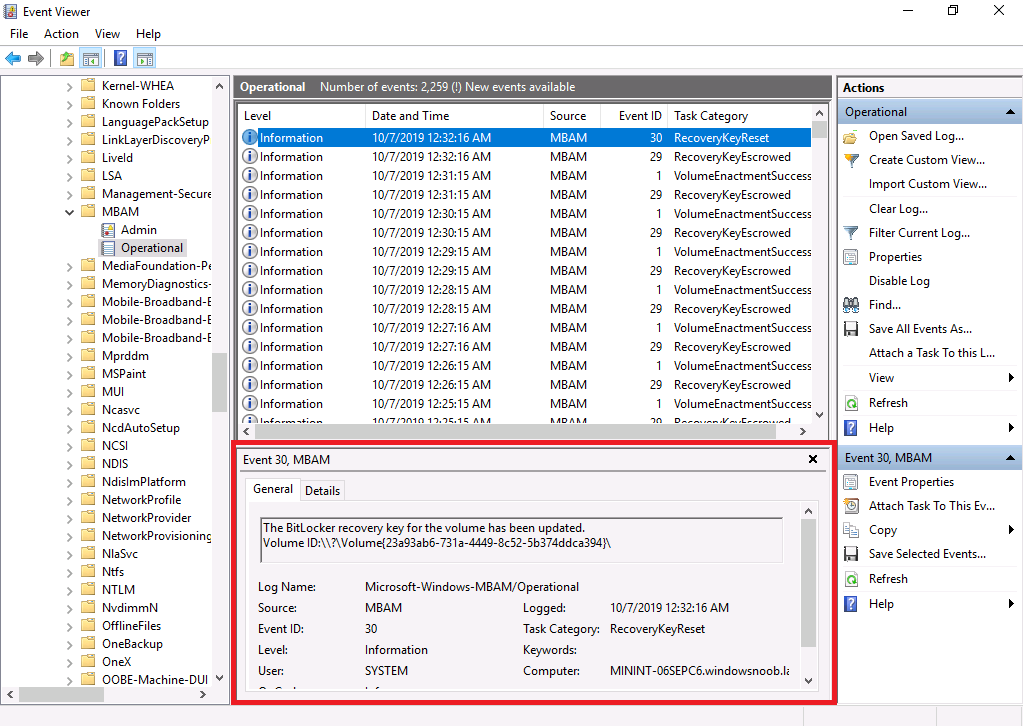
 And you can reveal that change on the client itself via Event Viewer, in the MBAM Operational logs, look for event ID 30.
And you can reveal that change on the client itself via Event Viewer, in the MBAM Operational logs, look for event ID 30.
Related reading
- https://www.niallbrady.com/2019/10/06/how-can-you-use-the-help-desk-feature-when-mbam-is-integrated-within-sccm/
- https://docs.microsoft.com/en-us/microsoft-desktop-optimization-pack/mbam-v2/how-to-recover-a-corrupted-drive-mbam-2
- https://docs.microsoft.com/en-us/microsoft-desktop-optimization-pack/mbam-v25/how-to-use-the-self-service-portal-to-regain-access-to-a-computer-mbam-25
- On-premises BitLocker management using System Center Configuration Manager
- How can I get BitLocker Recovery Keys from the ConfigMgr database
- How to fix: “Unable to find suitable Recovery Service MP. Marking policy non-compliant”
- https://techcommunity.microsoft.com/t5/Enterprise-Mobility-Security/Microsoft-expands-BitLocker-management-capabilities-for-the/ba-p/544329



Pingback: How can you use the Help Desk feature when MBAM is integrated within SCCM | just another windows noob ?
Pingback: How can you use the Self Service feature when MBAM is integrated within SCCM? | just another windows noob ?
Pingback: A quick look at reporting in MBAM integrated within Microsoft Endpoint Manager Configuration Manager | just another windows noob ?
Hello Brad,
I’m working on MBAM integration in MECM 2002, do you know if the key rotation in Self-Service portal still doesn’t work in latest version ?
Because Microsoft Docs bring me the doubt with following description of Self Service portal :
User self-service portal
Let users help themselves with a single-use key for unlocking a BitLocker encrypted device. Once this key is used, it generates a new key for the device.
https://docs.microsoft.com/en-us/mem/configmgr/protect/plan-design/bitlocker-management#user-self-service-portal
Thank you