Introduction
There are plenty of really good books recently released right now covering Microsoft Intune, and this one is no exception. This book is called Microsoft Intune Cookbook and it’s from fellow Microsoft MVP, Andrew Taylor. The book is designed to help you learn how to get the most out of Microsoft Intune and provides a wealth of knowledge from a very clever dude.
In this review I won’t cover every chapter in the book, if you want those details (and you do!) then go buy it, it’s well worth it. I will however run through my thoughts of the content and give you a glimpse of the first few chapters.
So let’s take a look at the book. The Preface explains who the book is for, do read it. I was lucky enough to get a physical copy from <packt> publishers and it’s a substantial book weighing in at approx 550 pages. Packt offers a nice feature in that if you buy the physical book, they include a QR code that you can scan to get a PDF version of the book for free also, just include your proof of purchase, I like this idea.
Chapter 1 covers Getting started with Microsoft Intune including topics like creating a tenant, creating users, assigning Entra Id roles and the difference between creating static and dynamic Entra Id groups. In addition to that it covers licensing to use Intune, which is explained very nicely and is expanded upon in Chapter 14 covering all of the additional add-ons in the Intune Suite.
What I particularly like about this book is that in addition to showing you how to do these things manually there’s a section in each topic (where applicable) called Automating it. That automation comes from PowerShell scripts. The scripts used in the book are available for download from https://github.com/PacktPublishing/Microsoft-Intune-Cookbook
One thing to note is that on page 5 of Chapter 1 it tells you how to get connected to Microsoft Graph in order to use the sample scripts most effectively while reading the book. Make sure you start here otherwise you’ll most likely see errors when trying to run the scripts otherwise. So before doing any of the automation, run this script.
Note: You may need to adjust it somewhat to add additional permissions based on what you are trying to do.
For example when creating dynamic groups using the scripts provided I got a permission related error shown below.
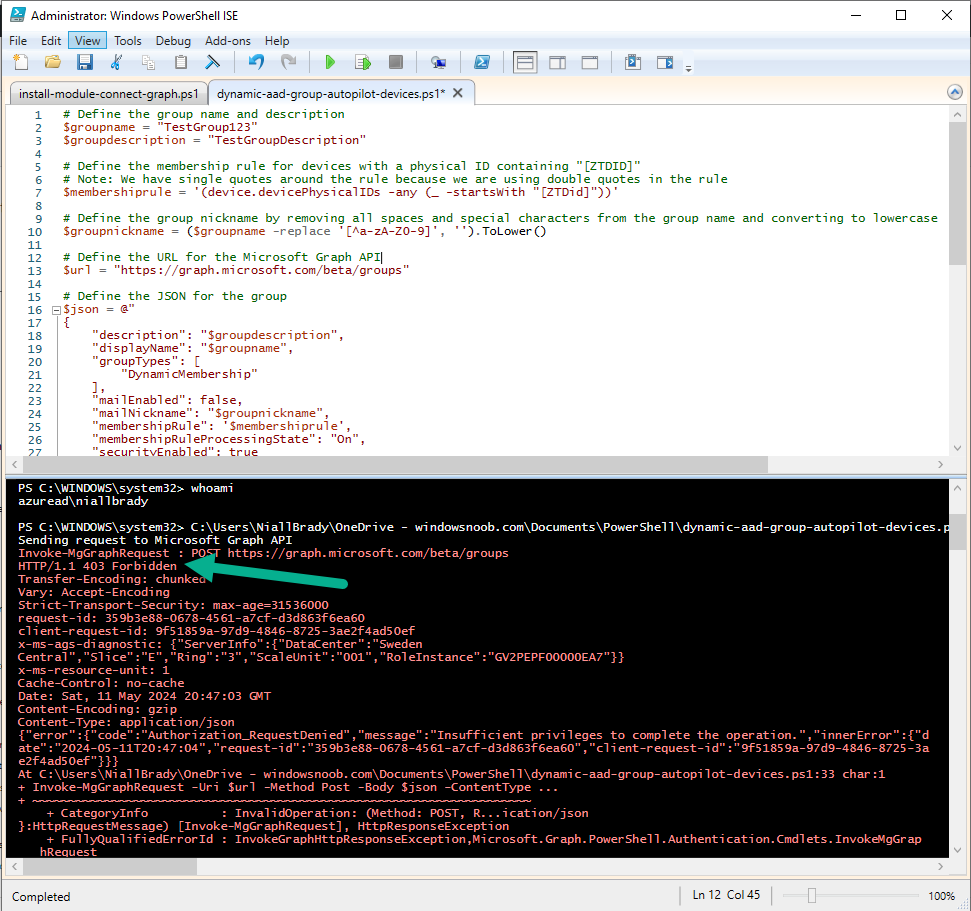
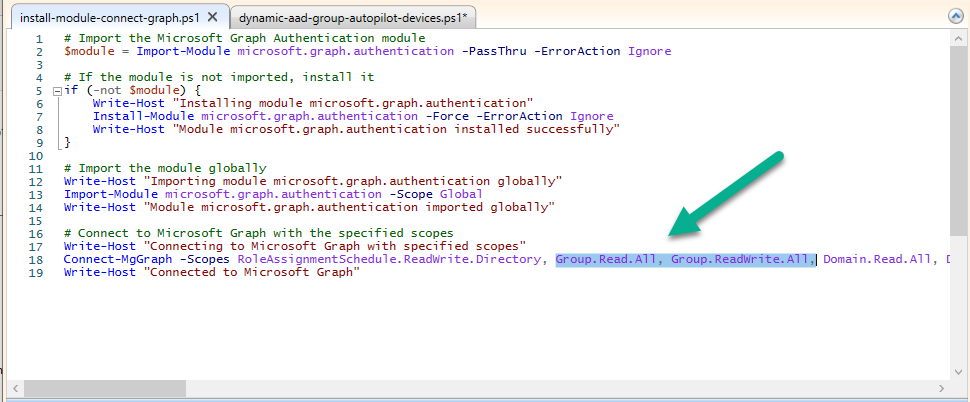
Adding these additional scopes (Group.Read.All, Group.ReadWrite.All) highlighted below solved it. This may not be immediately obvious to those who are not proficient with PowerShell and/or Microsoft Graph, so perhaps a bit more discussion about these scopes in the Chapter would have been helpful.
After adding the missing scopes and rerunning the dynamic-aad- group-autopilot-devices.ps1 script, it created the dynamic group without any error this time, fantastic.
Update: I spoke with Andrew and he’s now update the Github scripts with these permissions, thanks Andrew !
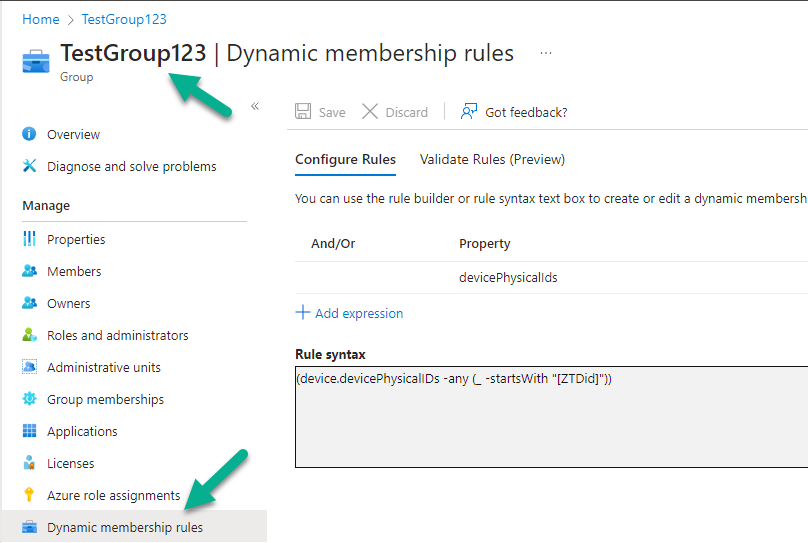
As these scripts are available on GitHub I hope they’ll get updated with additional scopes needed to complete the exercises shown in the book otherwise some readers may struggle.
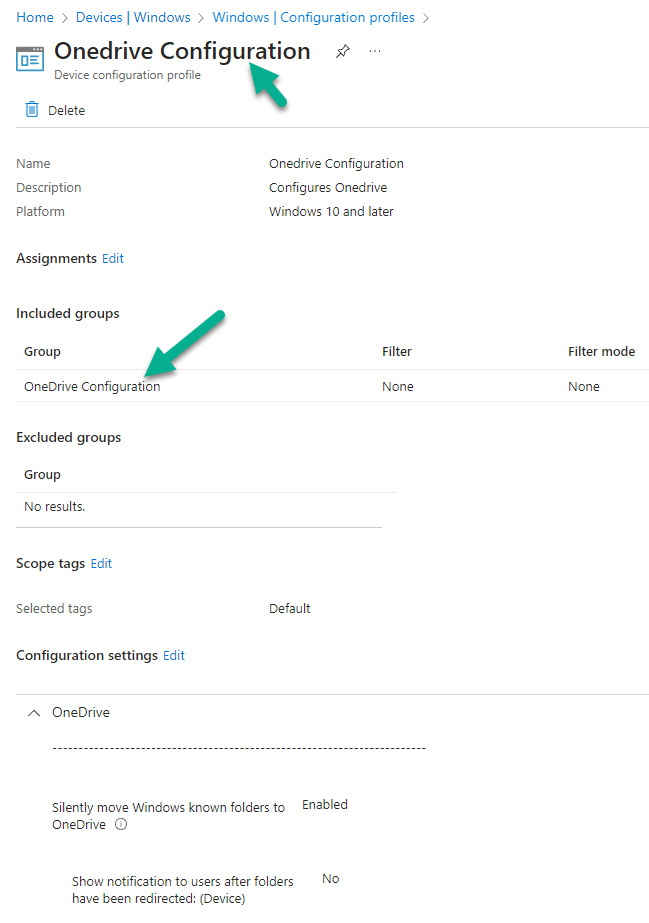
Chapter 2 covers Configuring your new tenant for Windows devices and once again follows the same pattern of showing you how to manually do things before showing you how to automate it. I like that he has a Chapter materials section explaining concepts used in the chapter, it really helps. I looked at the sample Onedrive configuration script, and added the missing details (tenant ID, aad group Id) and gave it a whirl.
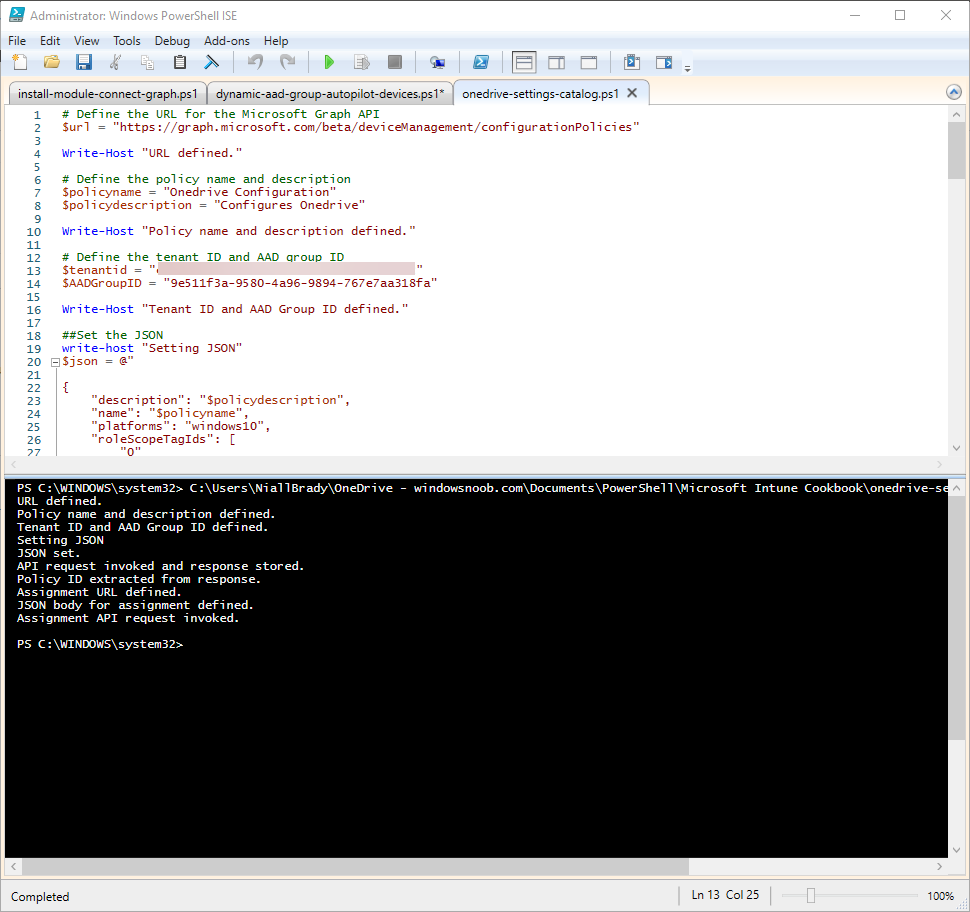
And it ran successfully, next I browsed Intune and sure enough, there was the newly created OneDrive Configuration policy, very nice!
Chapter 3 moves on to Securing your Windows devices with Security Policies, and covers many things including setting up a security baseline, configuring antivirus policy, configuring Windows Security experience, BitLocker policy, Windows Firewall and deploying ASR rules.
I decided to test the windows-laps-EnableLocalAccount.ps1 script. It just worked.
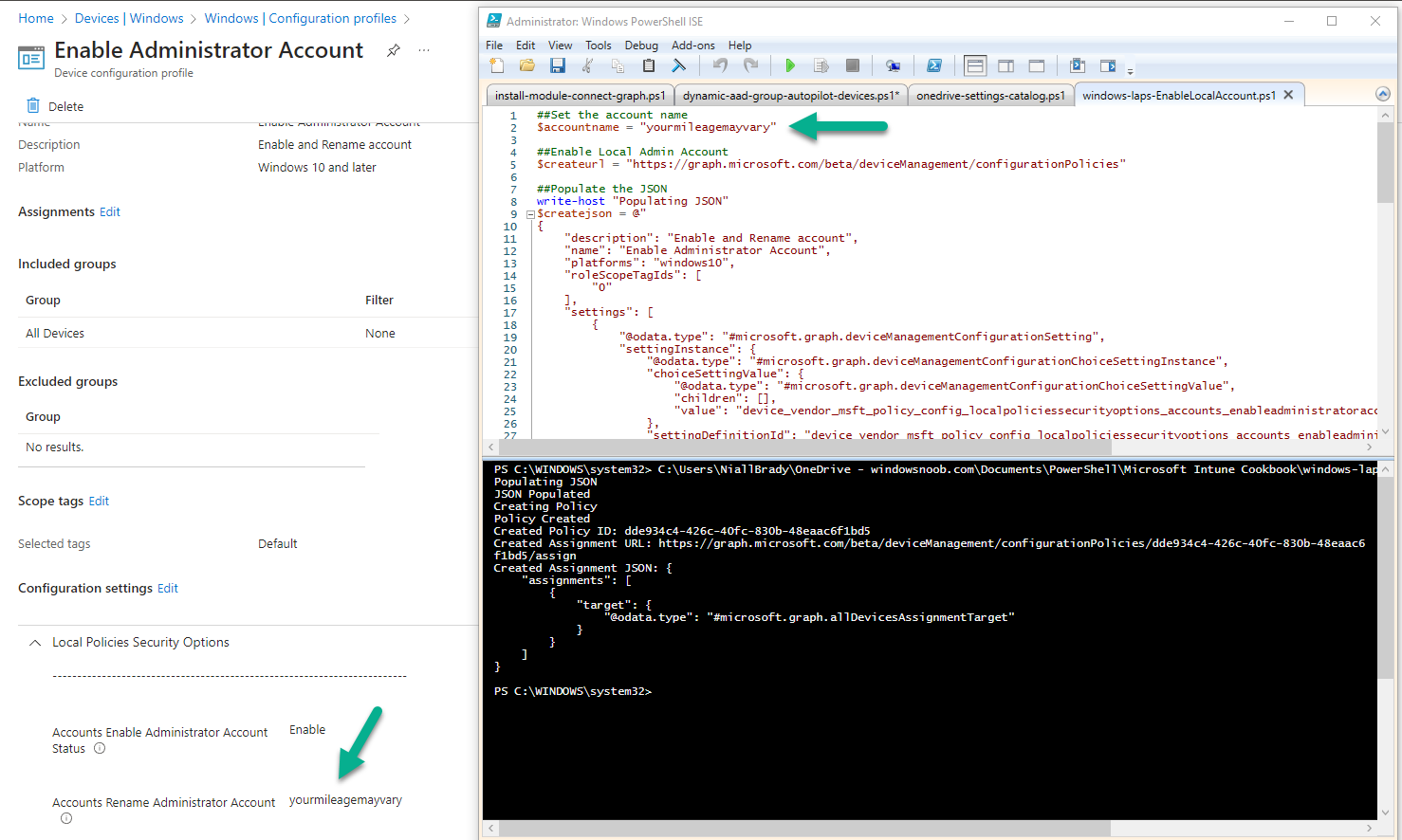
Of course there are more sample scripts for Windows LAPS included in this chapter, but it’s great to see new stuff being covered and sample scripts to create them.
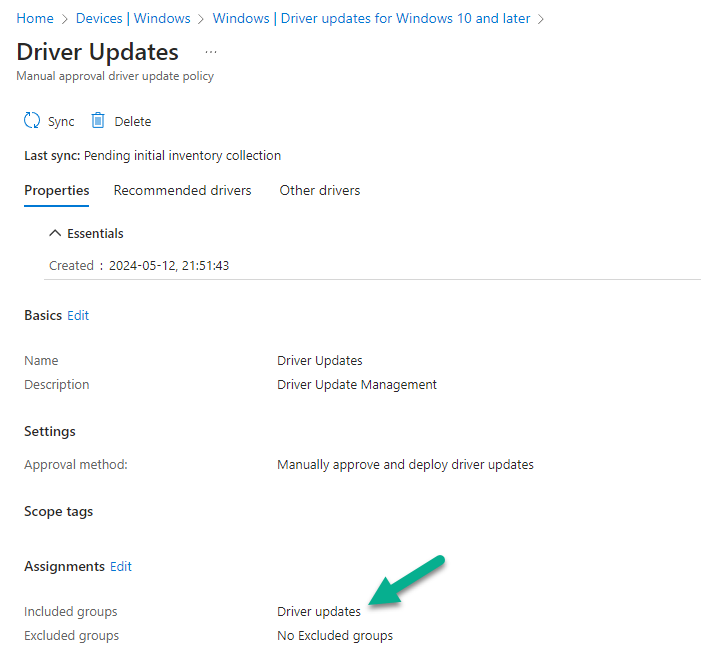
Chapter 4 covers setting up enrollment and updates for Windows and this deals with building update rings including feature and quality updates, configuring driver updates, enrolling and using Windows Autopatch, Windows Hello for Business and more.
I decided to test creating a driver profile using the create-driver-profile.ps1 script. It produced and error shown below and that’s because by default it has a non-valid group Id.
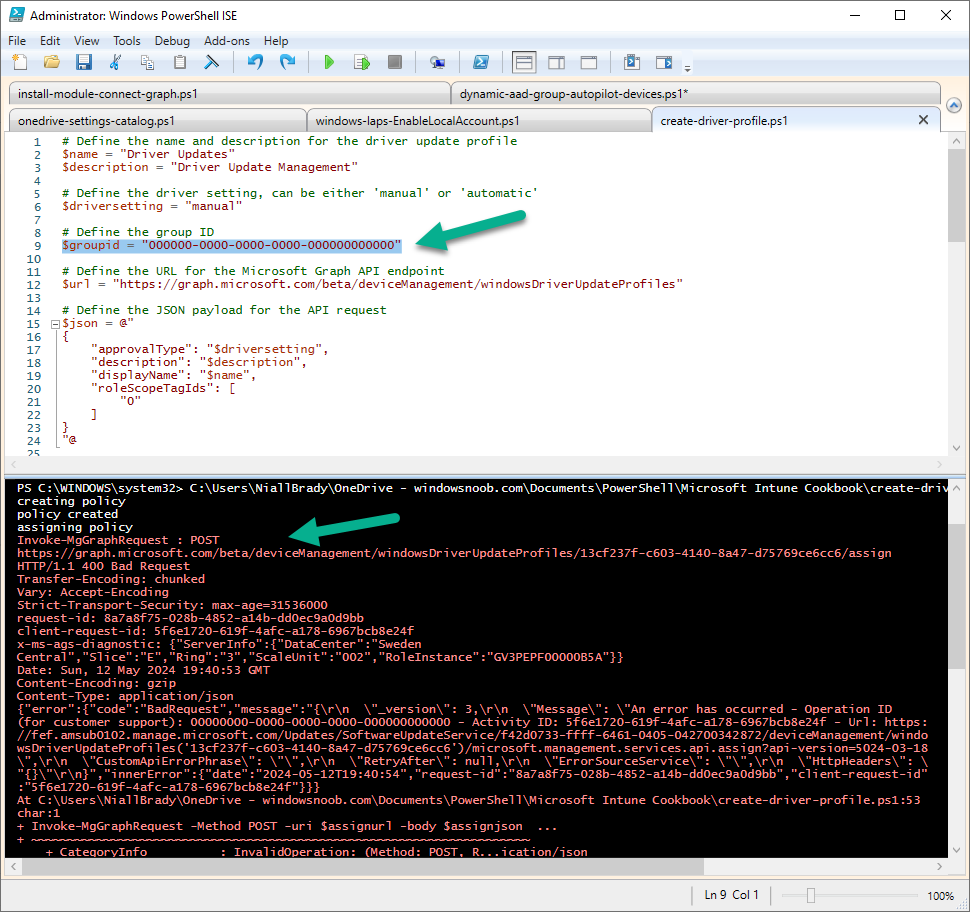
In previous scripts, where you needed to change a variable, the script had a “Enter your Group ID here” in place of the value, and this should also be the case here. Changing it to an actual valid Group Id solved it.
This might not be a problem for someone who works and deals with PowerShell/Intune every day as they’d figure it out quickly based on the error and the id used in the script, but for new comers it might stop them in their tracks. The book text (page 115) also didn’t mention to change the Group Id to one that is a valid Group Id.
Anyway, once I used a valid Group Id, all was good and the policy was created!
Related reading
- Graph Permissions – https://learn.microsoft.com/en-us/graph/permissions-reference
- Microsoft Intune Cookbook (GitHub) – https://github.com/PacktPublishing/Microsoft-Intune-Cookbook/tree/main
Summary
This book is great, and I highly recommend it! it covers far more than I’ve revealed above including Android, iOS and MacOS management. I really like the style of Andrew’s writing and the way he clearly shows users how to configure things manually before showing them how to automate it. Speaking of automating, I love that all the scripts used in the book are available for download on Github. That’s awesome. Automating things is clearly the future and any Intune admin wanting to learn more needs a copy of this book. Well done Andrew !


