If you upgrade to the latest technical preview release of Configuration Manager 2002, you’ll see some new Bitlocker Management features are revealed in the console.
When you create a new Bitlocker Management policy, the first obvious change is shown below.
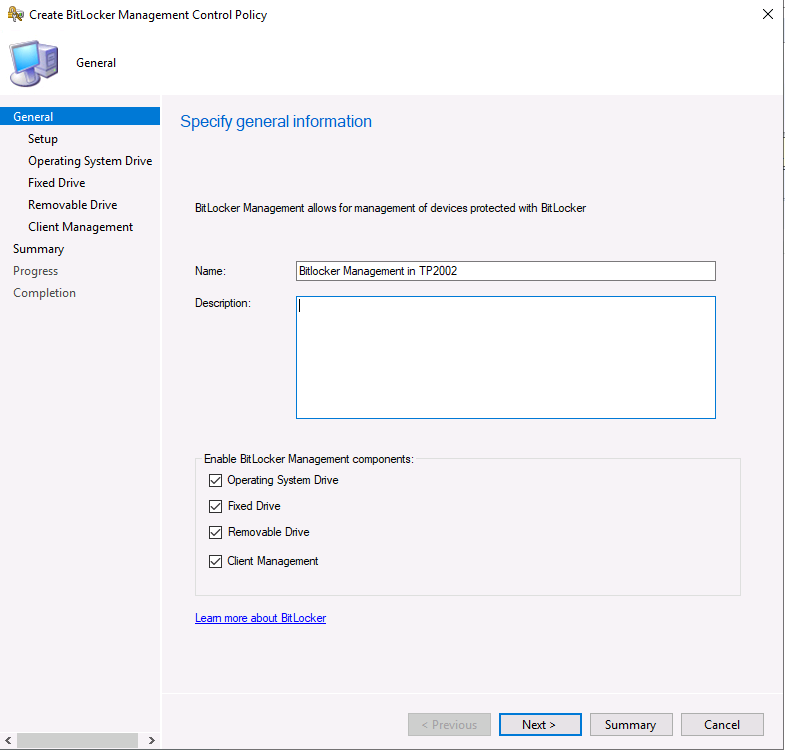 clicking next you’ll see the UI has changed even more, and now the following options are available on the specify Setup screen:
clicking next you’ll see the UI has changed even more, and now the following options are available on the specify Setup screen:
- Prevent memory overwrite on restart
- Validate smart card certificate usage rule compliance
those options are explained in the following Docs
| Prevent memory overwrite on restart | Suggested Configuration: Not Configured
Configure this policy to improve restart performance without overwriting BitLocker secrets in memory on restart. When this policy is not configured, BitLocker secrets are removed from memory when the computer restarts. |
| Validate smart card certificate usage rule | Suggested Configuration: Not Configured
Configure this policy to use smartcard certificate-based BitLocker protection. When this policy is not configured, a default object identifier 1.3.6.1.4.1.311.67.1.1 is used to specify a certificate. |
On the Operating System Drive screen, you can see new options such as:
- Allow enhanced PINs for startup
- Operating system drive password policy
- Reset platform validation data after Bitlocker recovery
- Pre-boot recovery message and URL
- Encryption Policy Enforcement settings
explained below (via link)
Allow enhanced PINs for startup, enables you to configure whether enhanced startup PINs are used with BitLocker. Enhanced startup PINs permit users to enter any keys on a full keyboard, including uppercase and lowercase letters, symbols, numbers, and spaces. If you enable this policy setting, all new BitLocker startup PINs that are set will be enhanced PINs. If you disable or do not configure this policy setting, enhanced PINs cannot be used.
Not all computers support the entry of enhanced PINs in the Pre-Boot Execution Environment (PXE). Before you enable this Group Policy setting for your organization, run a system check during the BitLocker setup process to ensure that the computer’s BIOS supports the use of the full keyboard in PXE. For more information, see Planning for MBAM 2.5 Group Policy Requirements.
Require ASCII-only PINs check box
The Allow enhanced PINs for startup Group Policy setting also contains a Require ASCII-only PINs check box. If the computers in your organization do not support the use of the full keyboard in PXE, you can enable the Allow enhanced PINs for startup Group Policy setting, and then select the Require ASCII-only PINs check box to require that enhanced PINs use only printable ASCII characters.
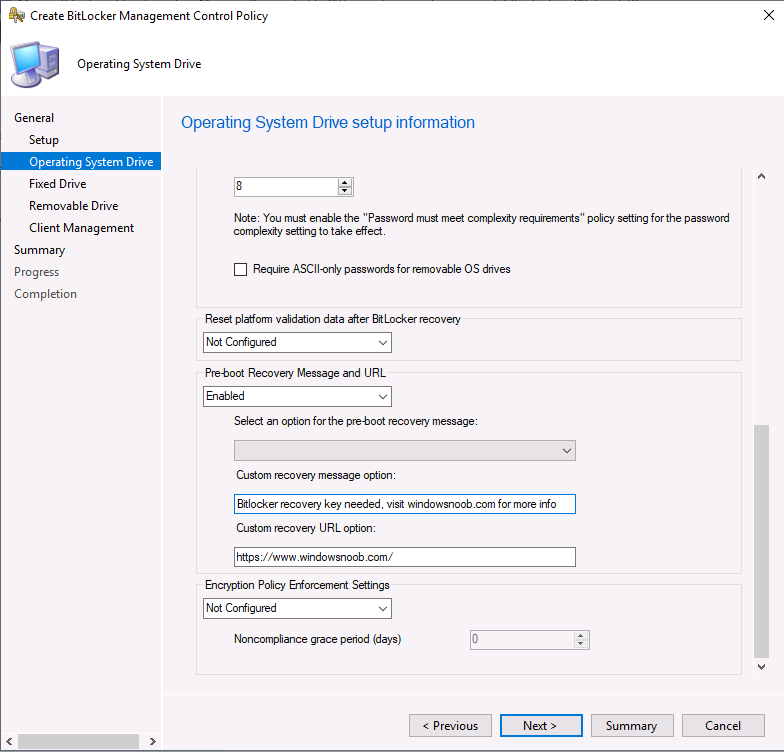
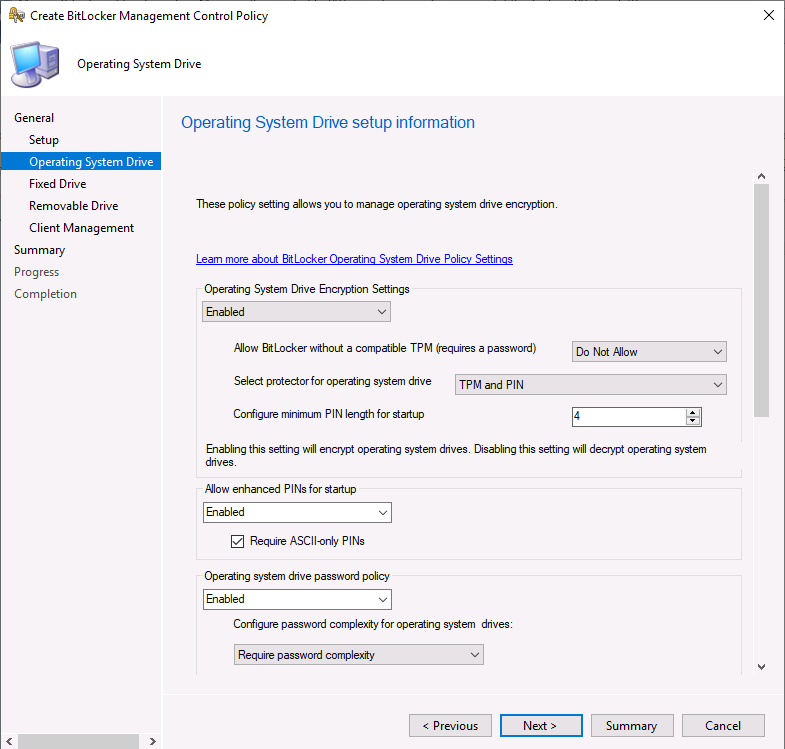 You need to scroll down to see all the new settings in Operating System Drive
You need to scroll down to see all the new settings in Operating System Drive
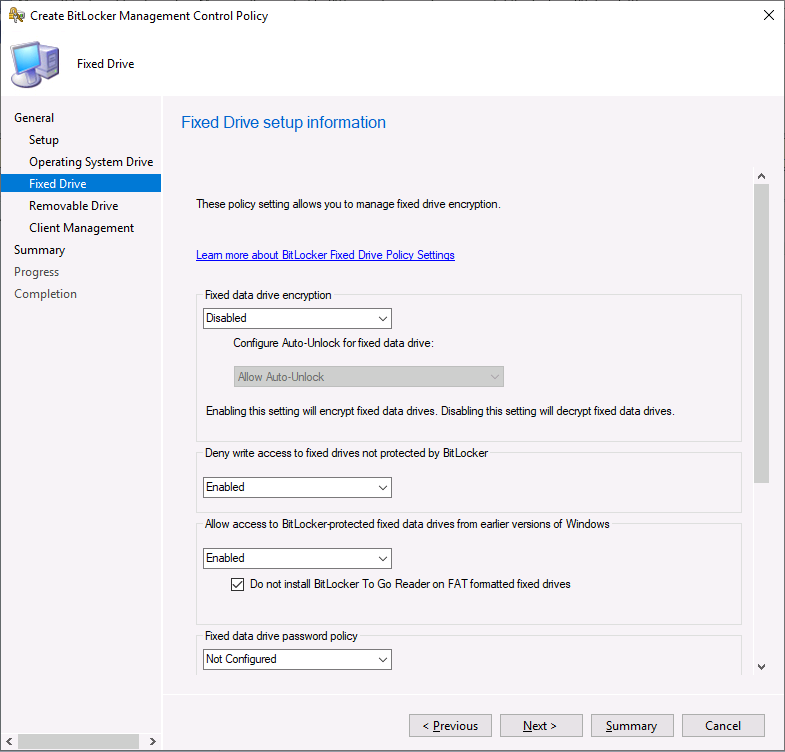
 The fixed drive screen has many additional options shown below (you need to scroll down to see all of the options).
The fixed drive screen has many additional options shown below (you need to scroll down to see all of the options).
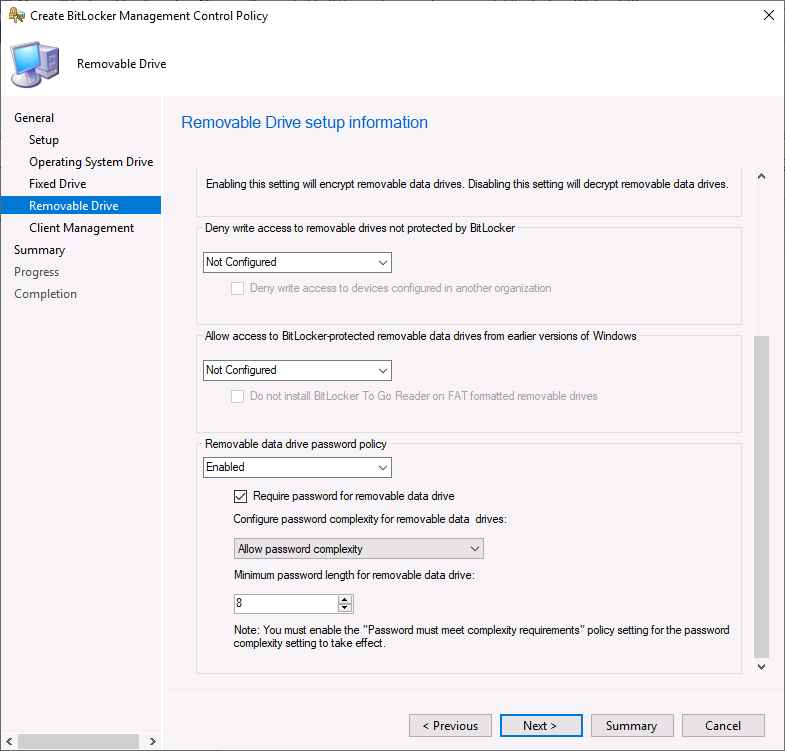
 Removable drive also has new abilities added
Removable drive also has new abilities added
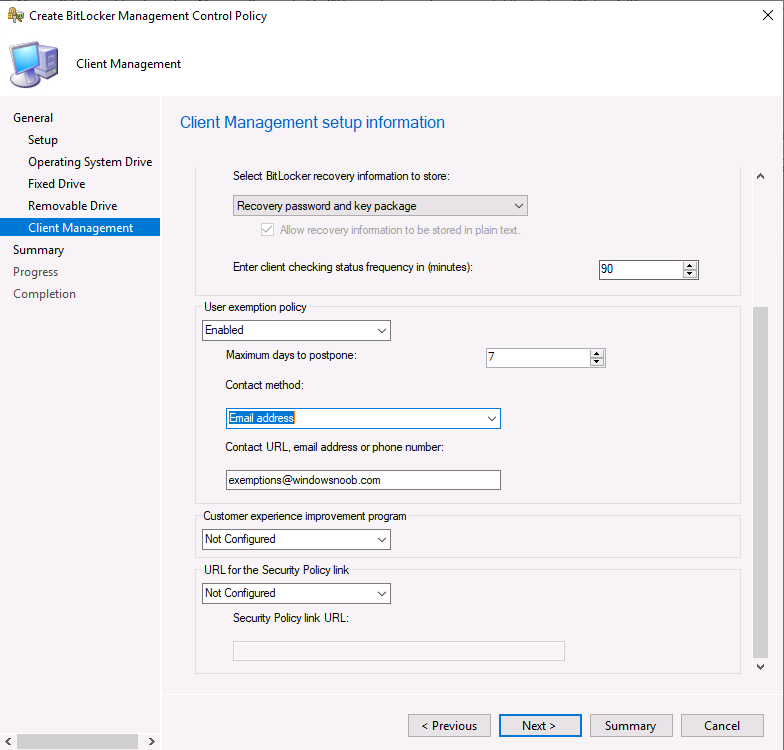
 And you can now configure User exemption Policy on the Client Management screen !
And you can now configure User exemption Policy on the Client Management screen !
- When end users sign in to a computer that is required to be encrypted, they receive a notification that their computer is going to be encrypted. They can select Request Exemption and postpone the encryption by selecting Postpone, or they can select Start Encryption to accept the BitLocker encryption.Note
Selecting Request Exemption postpones the BitLocker protection until the maximum time that is set in the User Exemption Policy. - If end users select Request Exemption, they receive a notification telling them to contact the organization’s BitLocker administration group. Depending on how the Configure User Exemption Policy is configured, users are provided with one or more of the following contact methods:
- Phone number
- Webpage URL
- Mailing address
- After the exemption request is received, the MBAM administrator decides whether to add the user to the BitLocker Exemption Active Directory Domain Services (AD DS) group.
- After an end user submits an exemption request, the MBAM Client reports the user as “Temporarily exempt.” The Client then waits a specified number of days, which IT administrators configure, before it checks the computer’s compliance again. If the MBAM administrator rejects the exemption request, the exemption request option is deactivated, which prevents the user from requesting the exemption again.
 That’s a huge amount of changes added to Bitlocker Management and I hope to test them before they show up in the (next ?) release of Configuration Manager Current Branch.
That’s a huge amount of changes added to Bitlocker Management and I hope to test them before they show up in the (next ?) release of Configuration Manager Current Branch.


