Introduction
You’d have to be living under a rock to not have noticed the blog posts and tweets from many different people (including myself) in relation to patching your Windows 7 computers (and others… including eeek… Windows XP) against the BlueKeep vulnerability.
I originally blogged about the problem on May 14th, the day Microsoft released their first information about the problem, and I added an update on May 31st and I’ll include that update here again for your benefit.
BlueKeep is a term for a security vulnerability (CVE–2019-0708) (noted as “critical” by Microsoft)[1][2] affecting computers using older versions (Windows 8 and Windows 10 are not affected) of the Microsoft Windows operating system.[3][4][5][6][7][8][9][10][11][12]
As of May 2019, nearly one million computers may be at risk for the “wormable” BlueKeep Remote Desktop Services (RDS) Remote Code Execution (RCE) Remote Desktop Protocol (RDP) vulnerability.[9][11] Microsoft considers the flaw “critical”, and recommends installing available update patches as soon as possible to affected systems to mitigate the vulnerability, as well as disabling Remote Desktop Services if they are not required.[3][4]
Now NSA are involved
So now the U.S. National Security Agency (NSA) have added an advisory about this so maybe they know some insider info about what’s about to come, either way here’s a snippet from their advisory.
NSA urges everyone to invest the time and resources to know your network and run supported operating systems with the latest patches. Please refer to our advisory for additional information. This is critical not just for NSA’s protection of National Security Systems but for all networks. In order to increase resilience against this threat while large networks patch and upgrade, there are additional measures that can be taken:
- Block TCP Port 3389 at your firewalls, especially any perimeter firewalls exposed to the internet. This port is used in RDP protocol and will block attempts to establish a connection.
- Enable Network Level Authentication. This security improvement requires attackers to have valid credentials to perform remote code authentication.
- Disable remote Desktop Services if they are not required. Disabling unused and unneeded services helps reduce exposure to security vulnerabilities overall and is a best practice even without the BlueKeep threat.
Good advice. Patch and if you have still not yet completed with that process due to various reasons, then at least make sure to take the additional measures mentioned.
Update: 2019/6/18 – A section of the US Government (The United States Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA)) has now released advise to users asking them to patch, unreal isn’t it ! https://www.forbes.com/sites/daveywinder/2019/06/18/u-s-government-announces-critical-warning-for-microsoft-windows-users/amp/
Laying a trap
But what if you actually wanted to have a system in this state, sort of like a HoneyPot. You might want to have one in this state so that you can observe what happens when the worms *or whatever they are* start doing what they do so that you can analyze the results of the attack and the aftermath, and then replay it over and over to gather the data you need.
I first thought about doing this after reading a tweet from https://twitter.com/GossiTheDog where he was talking about creating his own HoneyPot.
Create your own HoneyPot
Note: Do NOT do this in Production. Only consider doing this in a Lab or locked down virtual environment. Do not subject any Production network to this gaping hole. This is purely for our own amusement and research.
To do this in a lab I did the following…
- Created a network switch with separate network
- Created a Windows 7 virtual machine
- Patched it against WannaCry and everything except BlueKeep
- Disabled Windows Update
- Created a user with a strong password (also see: https://pixelprivacy.com/resources/reusing-passwords/ )
- Enabled Remote Desktop, without using NLA
- Take a virtual machine snapshot (checkpoint)
- Port forwarded 3389 in the Linux router to this machines local IP
- Verified the computer was vulnerable to BlueKeep
- Verified the computer had RDP open to the ‘internet’.
and in a little but more detail…
In a nutshell, I created a separate network in Hyper v (create new Hyper v Virtual Switch) and this switch is directly connected to my Linux based router and therefore gets a 192.168.5.x ip address.
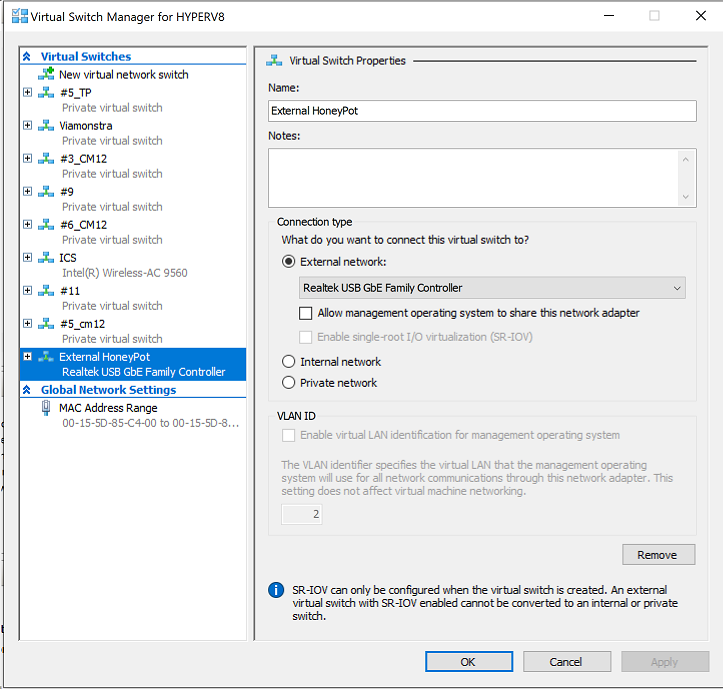 Once I had the Network Switch created, I then created a new Windows 7 Professional, Service Pack 1 virtual machine, and manually updated it with all applicable Windows Updates so that it wouldn’t get hit by say a WannaCry worm, except I did not patch it against BlueKeep.
Once I had the Network Switch created, I then created a new Windows 7 Professional, Service Pack 1 virtual machine, and manually updated it with all applicable Windows Updates so that it wouldn’t get hit by say a WannaCry worm, except I did not patch it against BlueKeep.
In other words I did not patch this virtual machine (deliberately) with the security updates pointed out below.
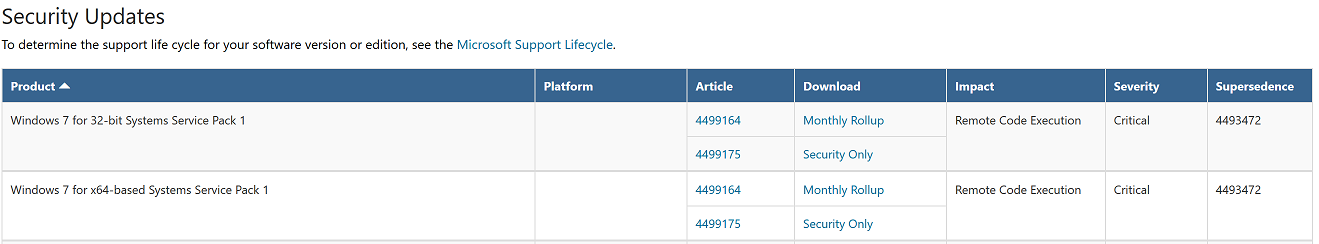 Next, I disabled the Windows Update service, this will ensure it doesn’t automatically update itself. Again, in case you missed my notes above, do NOT do this in Production, this is simply a HoneyPot that we are creating in a locked down lab.
Next, I disabled the Windows Update service, this will ensure it doesn’t automatically update itself. Again, in case you missed my notes above, do NOT do this in Production, this is simply a HoneyPot that we are creating in a locked down lab.
After I verified the computer was ready for BlueKeep, I created a user, with a strong password (that the BruteForce crackers would have a very hard time cracking) and enabled RDP without NLA.
Verifying BlueKeep vulnerability
Now that everything is in place I headed over to here to get the Windows version of a command line verification tool. You can compile it yourself or download the pre-compiled version for Windows here.
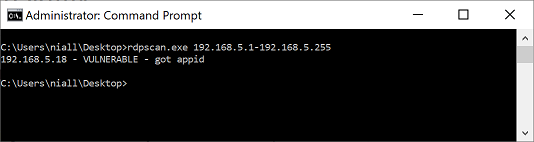 In the screenshot above I’ve scanned the entire network for that vulnerability and only got one result back, that is expected, it’s our un-patched virtual machine.
In the screenshot above I’ve scanned the entire network for that vulnerability and only got one result back, that is expected, it’s our un-patched virtual machine.
Lastly, I verified that the RDP port was open to the internet using canyouseeme.org, I’ve obscured the Internet facing IP address for obvious reasons.
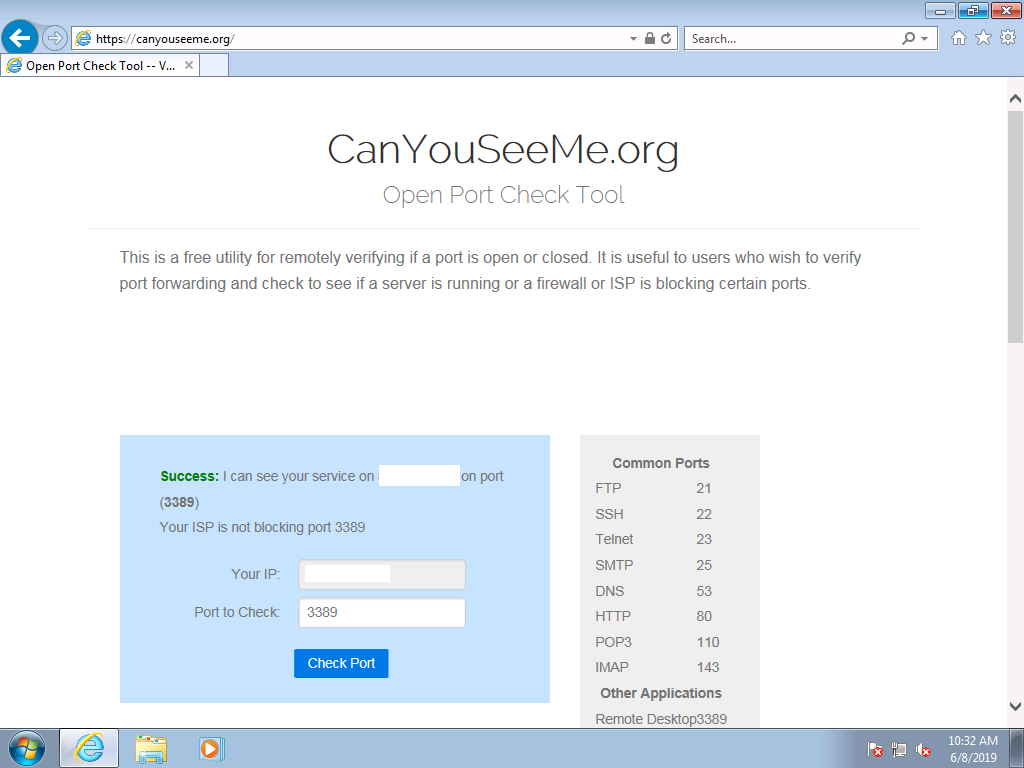 That’s it, time will tell pretty soon what happens next, and i’ll update here when I see some action.
That’s it, time will tell pretty soon what happens next, and i’ll update here when I see some action.
More HoneyPots
Recommended reading
- https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2019-0708
- https://www.nsa.gov/News-Features/News-Stories/Article-View/Article/1865726/nsa-cybersecurity-advisory-patch-remote-desktop-services-on-legacy-versions-of/
- https://www.forbes.com/sites/daveywinder/2019/06/07/nsa-warns-microsoft-windows-users-update-now-or-face-devastating-damage/#3131da743aa0
- https://github.com/robertdavidgraham/rdpscan
- https://www.avantia.dk/blog/2019/6/5/find-remote-desktop-hosts-vulnerable-to-bluekeep-before-someone-else-does
- https://pixelprivacy.com/resources/reusing-passwords/



Pingback: New RDP vulnerabilities – so how can we secure RDP? | Marius Sandbu
Pingback: Why is my bluekeep honeypot blue screening ? | just another windows noob ?
Pingback: Why does my bluekeep honeypot blue screening ? | just another windows noob ?