Introduction
At Microsoft Ignite this week in Florida, there were many new announcements of new capabilities in products such as Microsoft Intune. With so many new announcements it’s hard to keep up, but if you want to find out more, read on or select the part that interests you below.
- Part 1 – Introduction and news
- Part 2 – iOS – what’s new
- Part 3 – Android – what’s new
- Part 4 – macOS – what’s new
- Part 5 – Windows – highlights
This content is based on an excellent session entitled “BRK3036 – Managing devices with Microsoft Intune: What’s new and what’s next” and you can review it yourself here.
In this post we’ll look at some of the highlights for Windows 10 management with Intune.
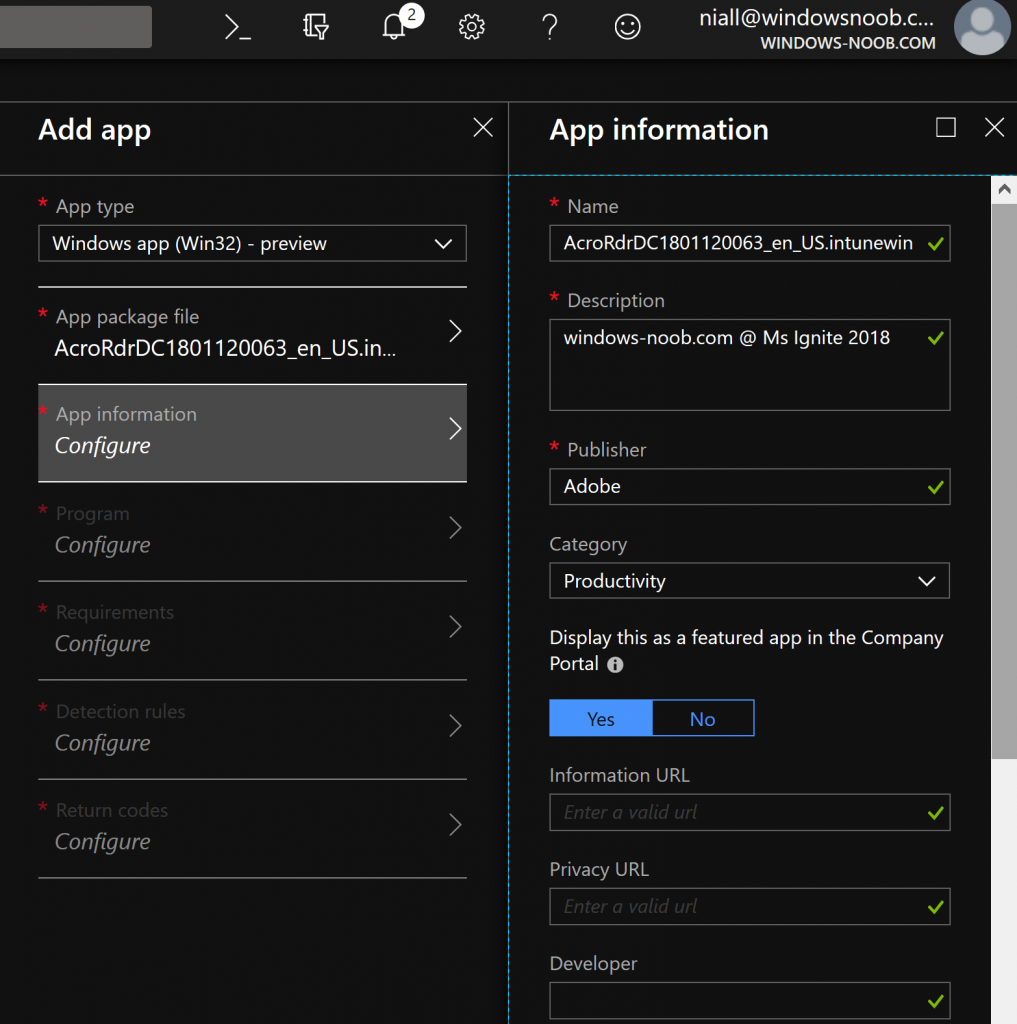
Win32 App Management feature
Now when you try out this feature in Intune, you’d think you can just point to a recently downloaded EXE, or MSI file, but no, you cannot.
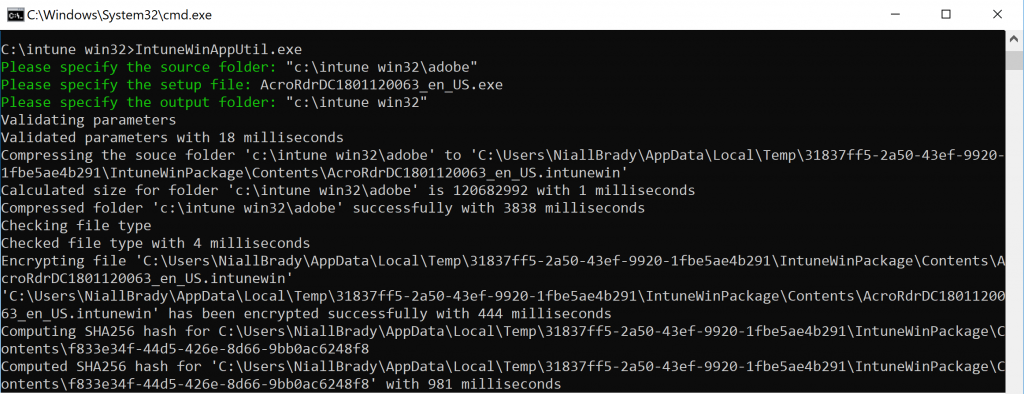
You can only use files that have been converted into the .intunewin extension. How do you get that extension ? using this tool.
Once downloaded, run the EXE and point it to the source folder that you have the MSI or EXE downloaded to that you want to convert, and then, spell out the file name, and finally select the output folder, it will then convert it to the *.intunewin extension as you see below.
which will allow you to upload it into Intune.
This new feature supports multi file installation, exe, msi, cab files.\ and you can even configure cmd line switches just like you do in Configuration Manager
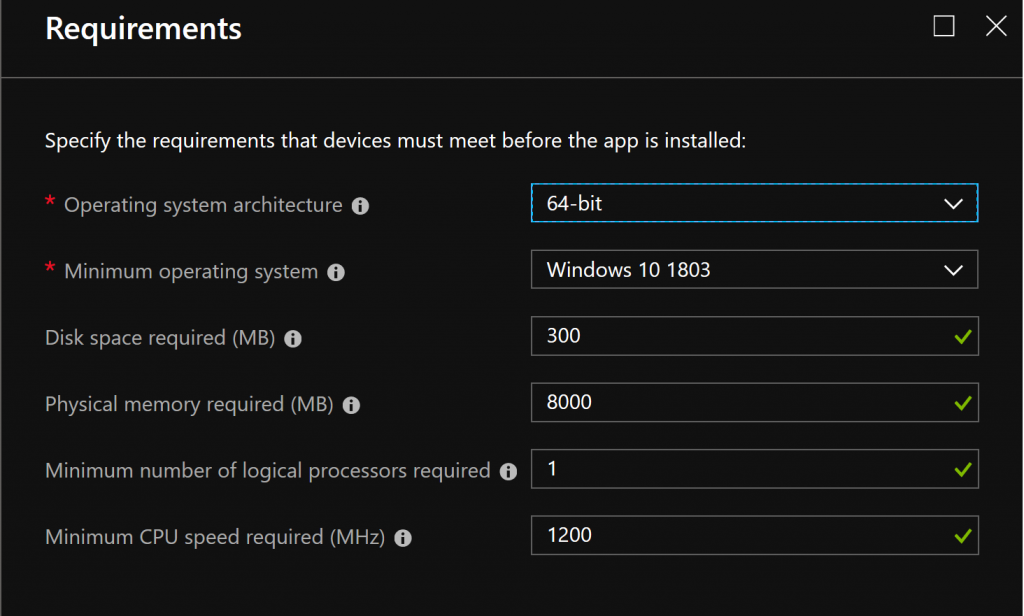
You can configure the requirements
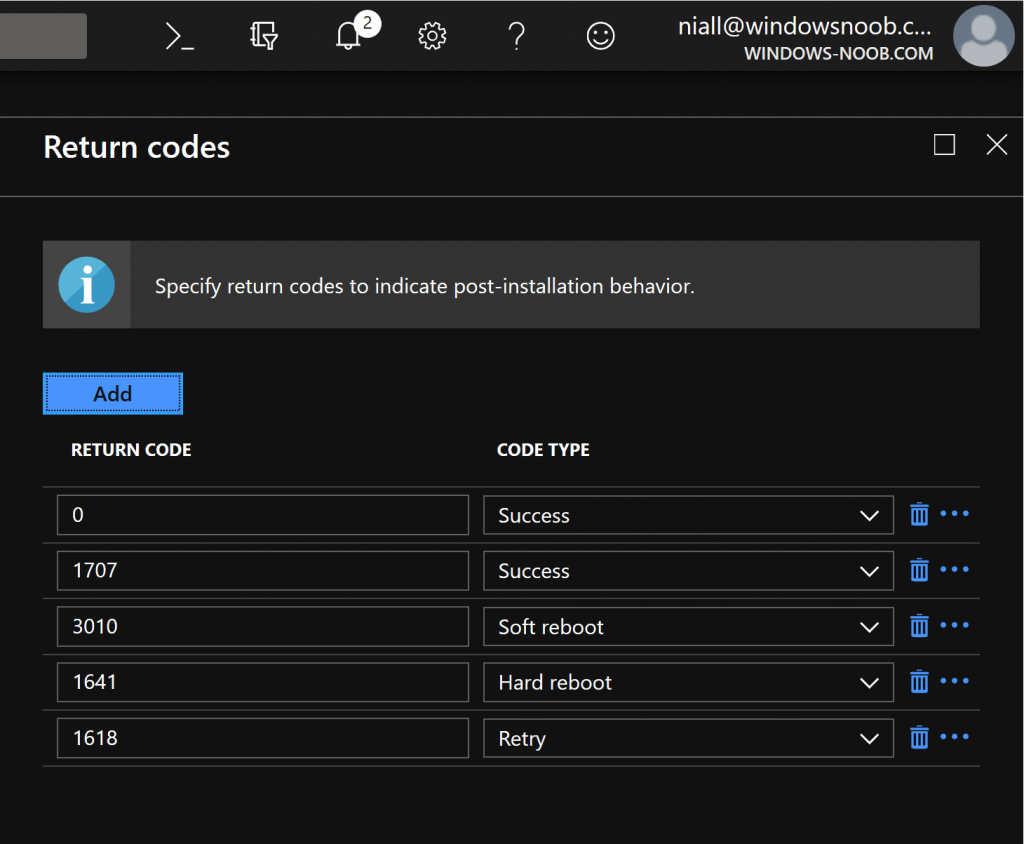
And you can even configure detection rules and return codes, so that you know if the app installed successfully or failed.
Once added, you can assign this to groups of users, as required (mandatory) or optional (via the company portal), and keep in mind that for Office ProPlus with Intune all you need to know is that you can utilize what’s available within Intune to deploy that, I blogged it earlier here.
What about Configuration Management ?
A few of the concerns from customers to Microsoft was that using the MDM stack in Windows for configuring Windows was that it had a lot of important settings, but not enough for what was needed to be configured in the environment.
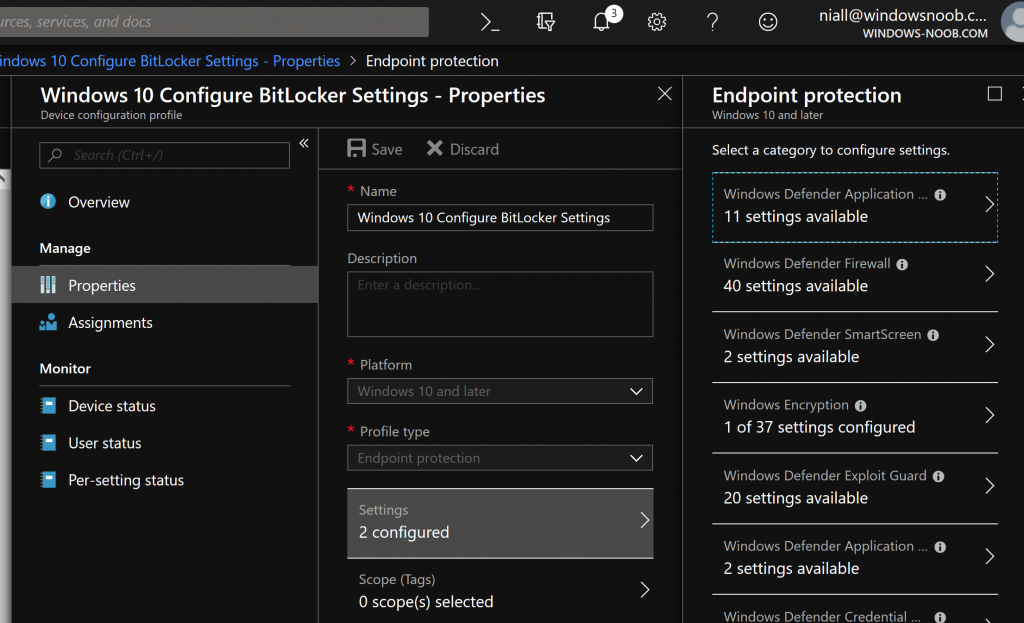
So now within (for example) Endpoint Protection in Intune, you can configure dozens of settings, that were previously available via Group Policy, things like firewall rules or Bitlocker.
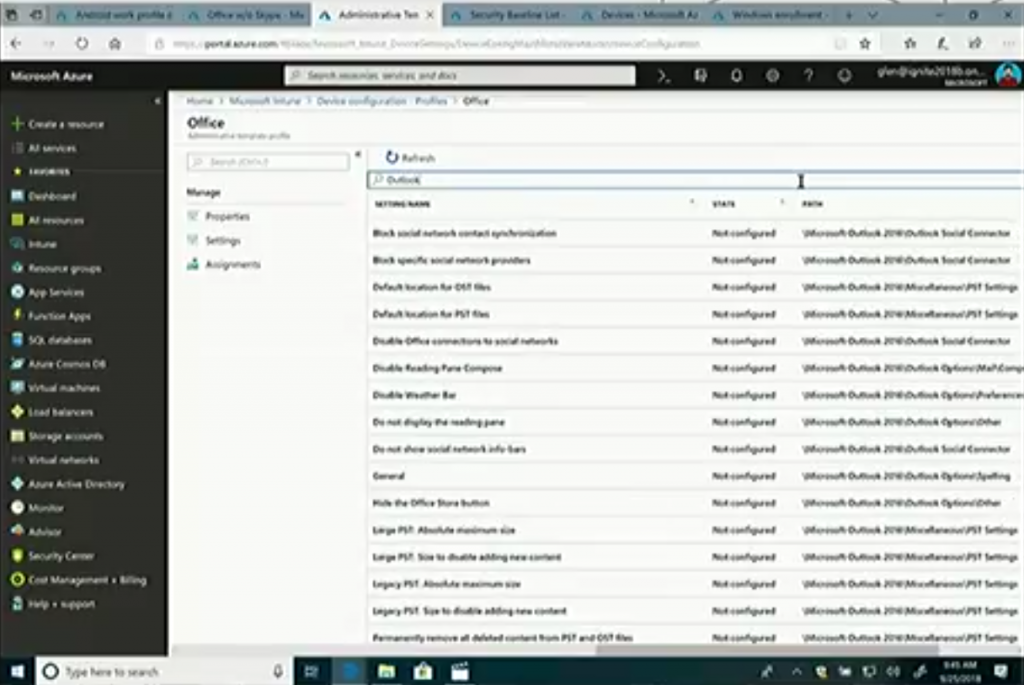
But if you select, Windows 10 or later, then select the new feature Administrative Templates you have thousands of settings to choose from (searchable too), that can configure things for applications like Office Desktop.
This takes the ADMX infrastructure from Group Policy and makes it possible to deploy via MDM.
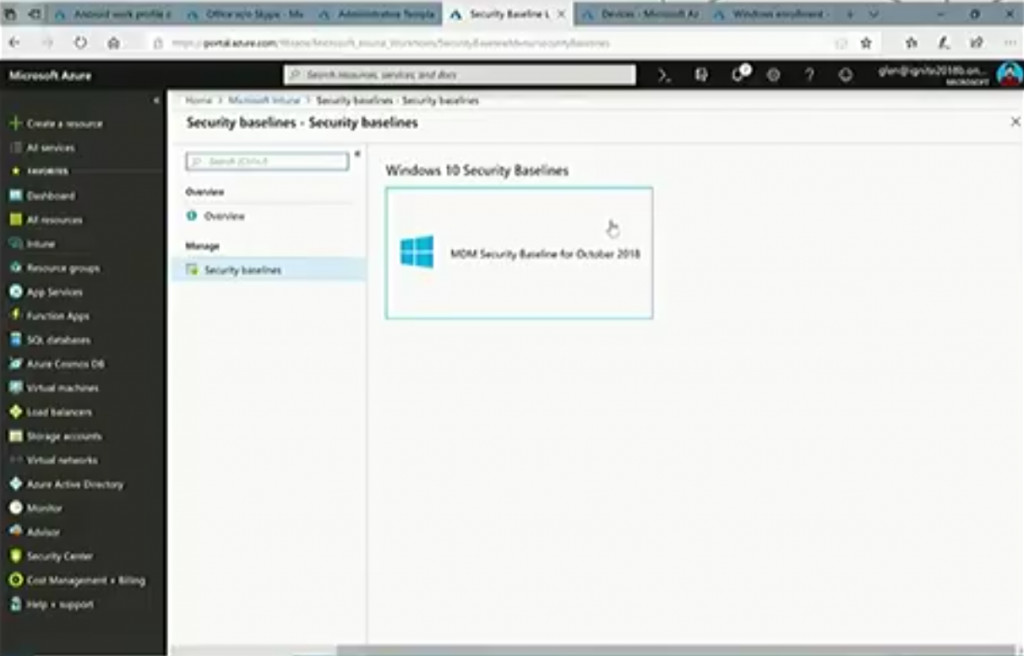
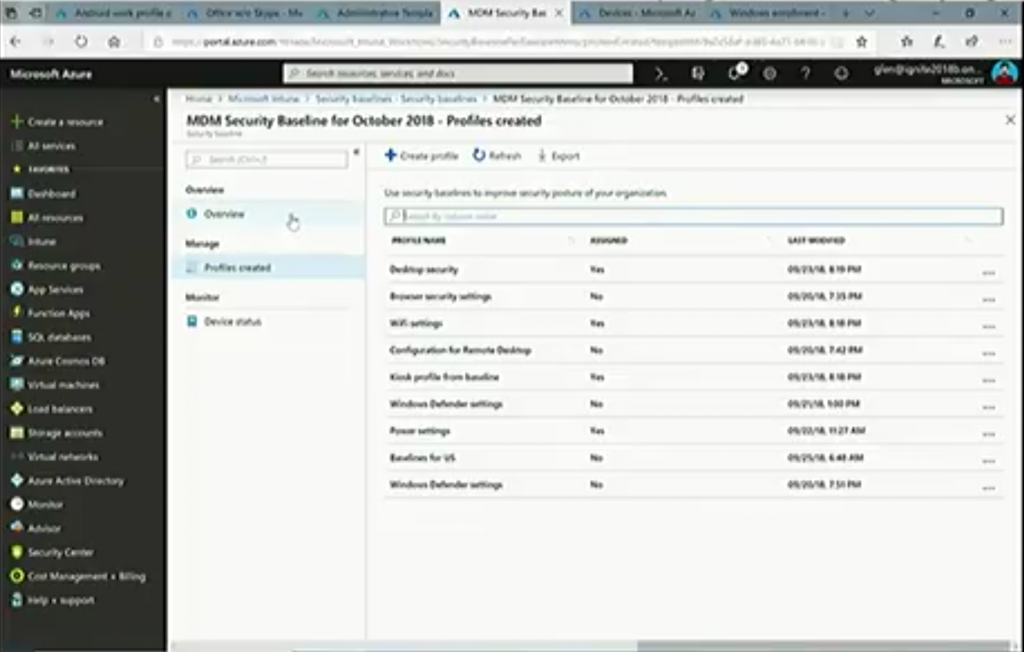
MDM Security baselines
But wait, there’s more, you can now also configure MDM security baselines.
And the idea behind these baselines is Microsoft has recommendations for what those settings should be. And with these options, you can select what should be good to select for your enterprise to have a secure compliant deployment of Windows.
The recommendations are available dynamically in the console on an ongoing basis.
What about Devices ?
If we go to the device enrollment, windows enrollment tab you can select windows enrollment and look at the new Windows Autopilot options, as shown below.
Note: The below info was taken from another related session, see my notes on that here
Windows Autopilot
Announced at Microsoft Ignite last year (2017), helps customers moving to modern management.
Windows AutoPilot Scenarios.

Hyrbid azure ad join, starting in 1809, can be hybrid azure ad joined (enrolled into Intune and device joined to on premise AD).
Also announced Windows Autopilot for existing devices…
Use Intune to create dynamic groups for those autopilot devices.
Can pre-assign users to devices, in the Intune console you find the device (in Windows Enrollment, Windows AutoPilot devices), click assign user,
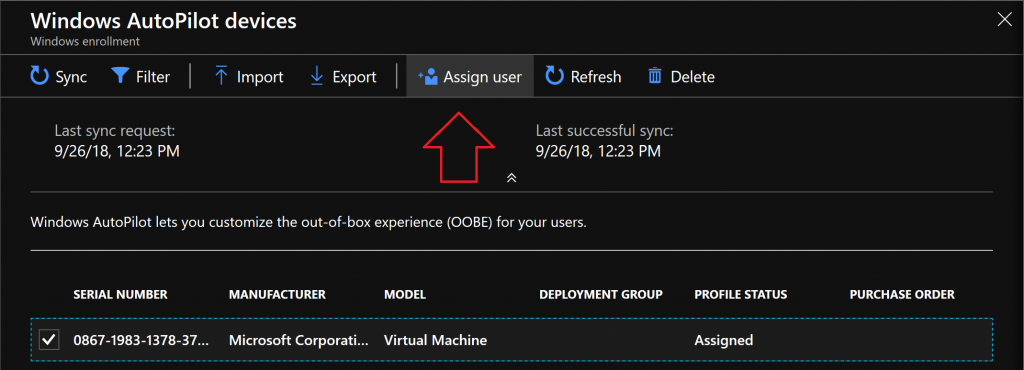 When they go through autopilot they wont be prompted for the email address, instead they’ll get a custom welcome and a more personalized login.
When they go through autopilot they wont be prompted for the email address, instead they’ll get a custom welcome and a more personalized login.
Windows Autopilot and ConfigMgr
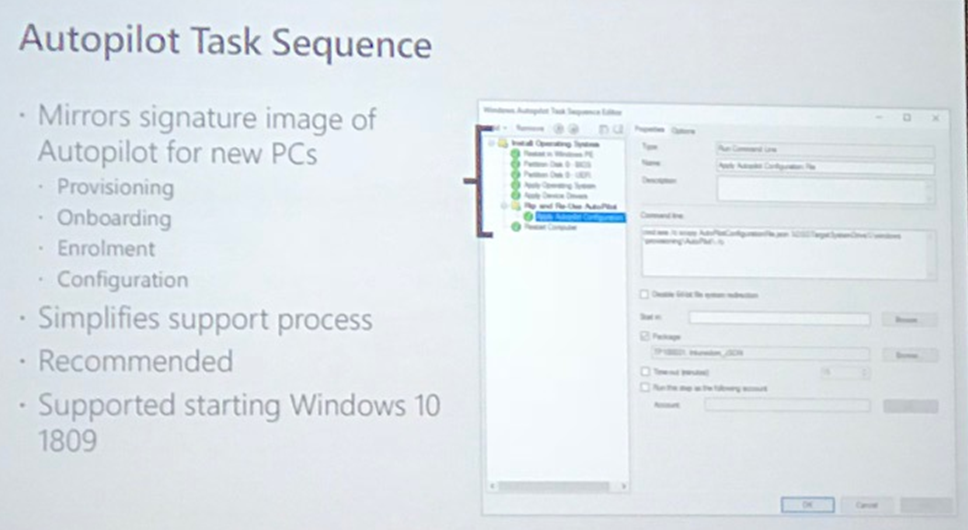
Autopilot task sequence, supported starting with windows 10 1809
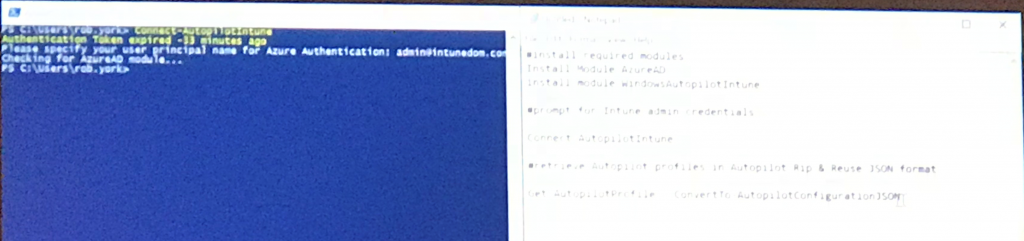
Create a package with the JSON file which was created using the Powershell cmdlets
 Then create the autopilot task sequence, add the package, provisioning the device using the task sequence
Then create the autopilot task sequence, add the package, provisioning the device using the task sequence
that’s it for this series, I hope you enjoyed it,
cheers
niall (at Microsoft Ignite in Orlando, Florida).




Pingback: Managing devices with Microsoft Intune: What’s new and what’s next – my notes (Part 4 – macOS) | just another windows noob ?
Pingback: Managing devices with Microsoft Intune: What’s new and what’s next – my notes (Part 1 – new features) | just another windows noob ?
Hi
Where do you find all the new option (security baselines, administrative and so on,…)
I don’t have any on my intune….!
just wait, it will show up