Introduction
In Part 1 of this mini series we integrated Windows Intune with System Center 2012 R2 Configuration Manager. In Part 2 we added Support for iOS devices (Iphone, iPad). In Part 3 we learned the difference between App Package for iOS (*.ipa file) and applications from the Apple App Store. We learned how to deploy them to iOS devices and edited our deployment types to set requirements so that the applications were made available to the user based on the iPhone or Ipad operating system version, in addition we also checked device Ownership information and deployed the application based on those requirements.
System Center 2012 R2 Configuration Manager with Windows Intune integration provides new abilities (double the default settings groups that were offered in Configuration Manager 2012 Service Pack 1) for configuring settings for mobile device management. In this part we will learn how to use and configure compliance settings in order to enable or disable certain configurable features on iOS devices. We will enforce a Password requirement and make it a minimum password length, this is a common requirement for organizations.
The following lists the default settings groups (or headings) of the mobile device settings which are now available, each default settings group contains many configurable settings:
- Password
- Device
- Email Management
- Store
- Browser
- Internet Explorer
- Content Rating
- Cloud
- Security
- Peak synchronization
- Roaming
- Encryption
- Wireless communications
- Certificates
- System Security
- Windows Server Work folders
Note: In addition to the above, you can configure additional settings that are not listed by clicking on configure additional settings that are not listed in the default settings groups when creating your configuration item. There are many additional settings available so do take a look at them.
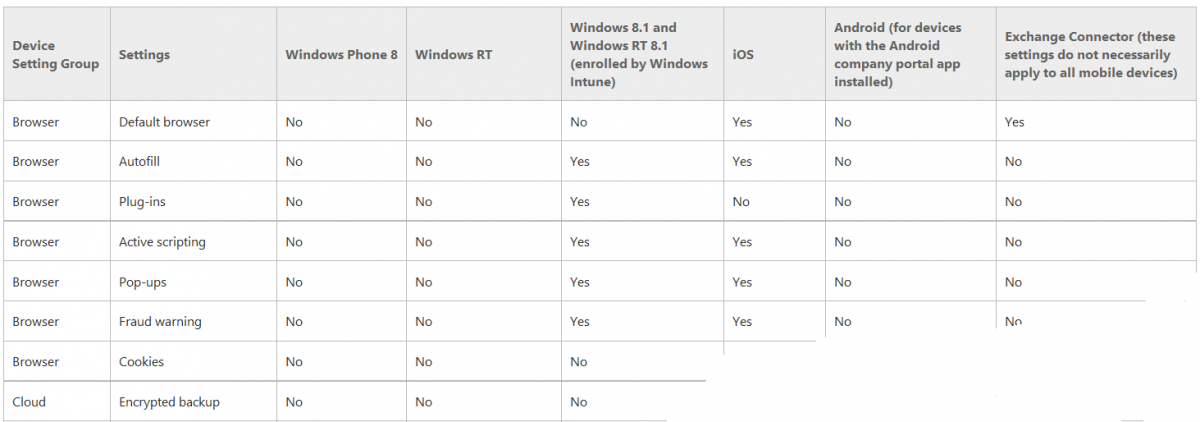
The following page on Technet explains the above settings in more detail and shows which settings are applicable by platform type.
Note: Although the list above is quite extensive and contains several configurable settings per heading, not all default settings groups apply to any one device type, the applicability of a setting is listed during Configuration Item creation.
Step 1. Create a new Mobile Device configuration item
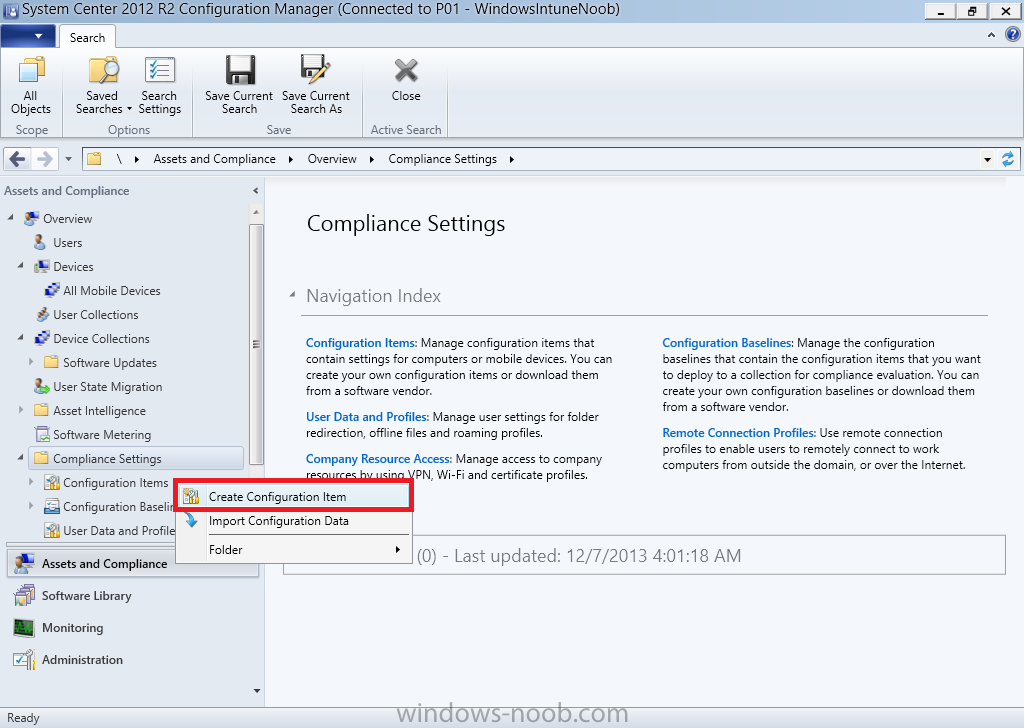
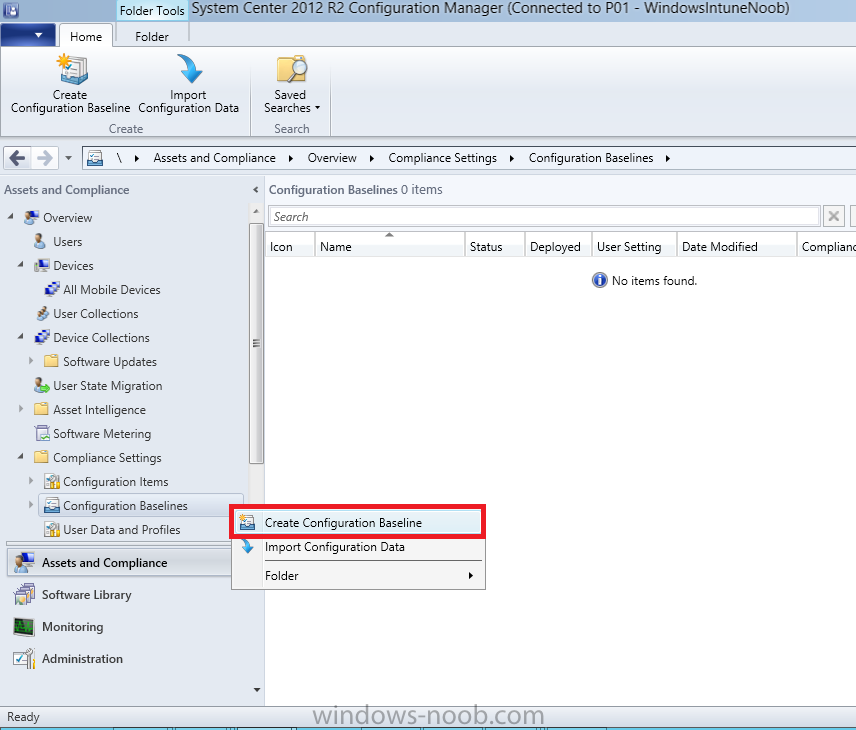
Compliance Settings within Configuration Manager are used to control the settings on your mobile devices. In the Configuration Manager console, click on Assets and Compliance, and expand Compliance Settings. Locate Configuration Items, right click and choose Create Configuration Item.
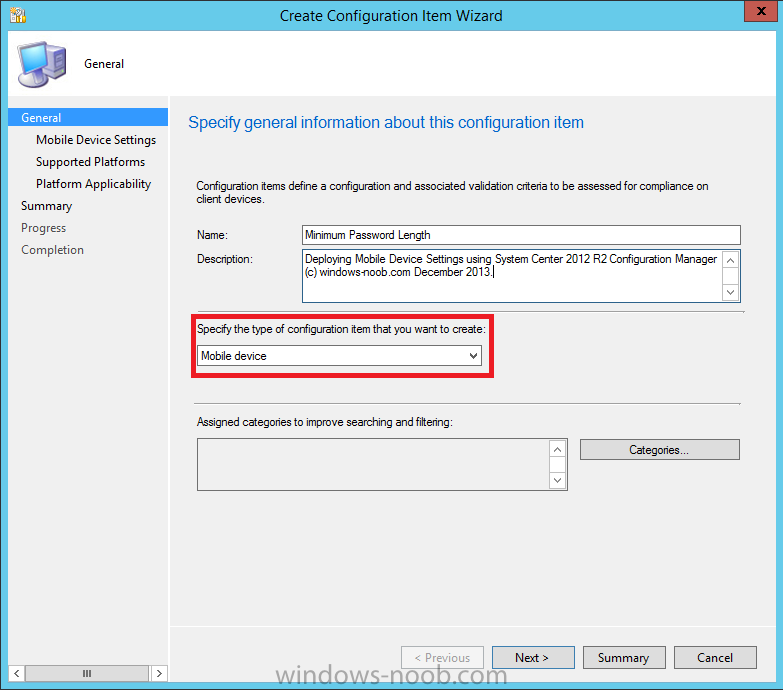
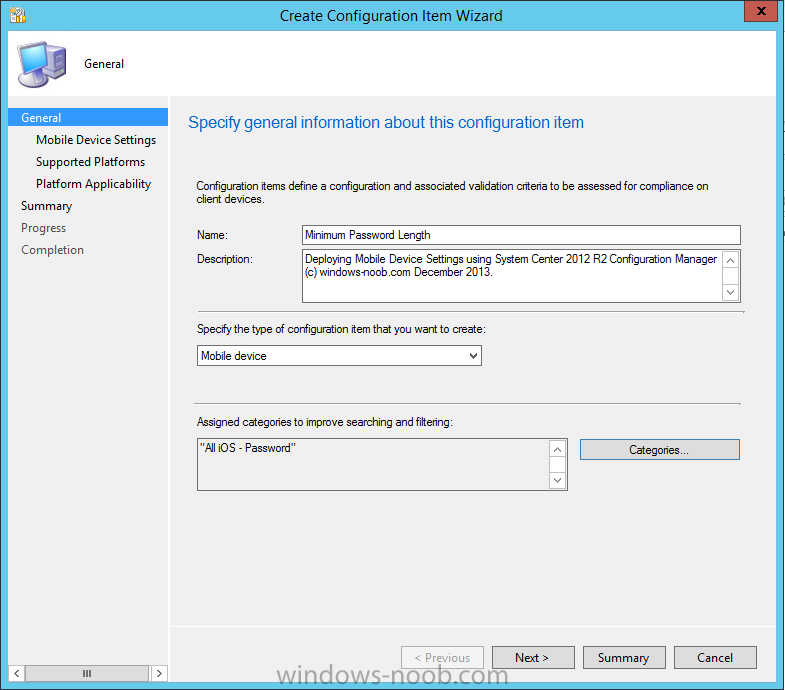
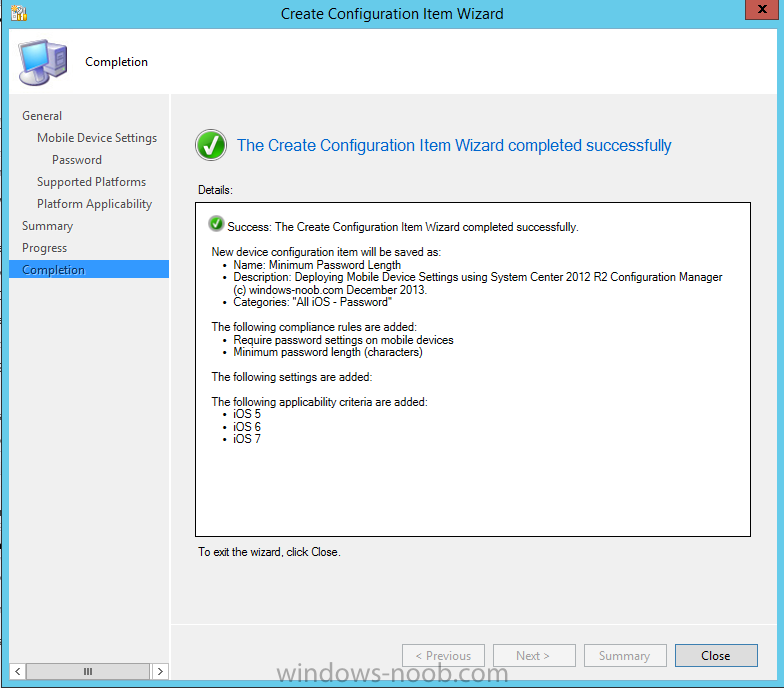
In the wizard that appears, give your configuration Item a suitable name which desribes the functionality of the Configuration Item such as Minimum Password Length, then from the drop down menu select Mobile Device as the type of Configuration Item you are going to create like in the example below
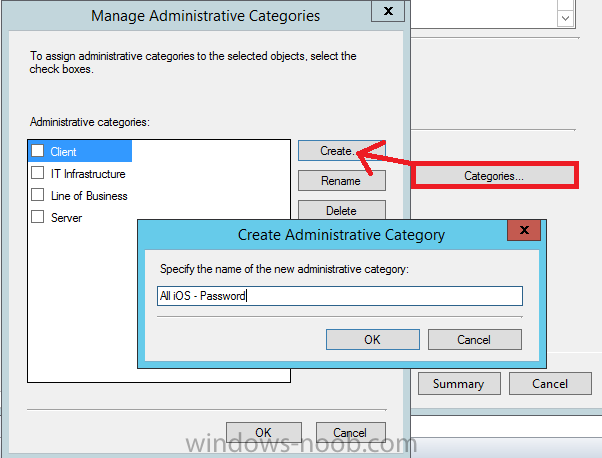
and then click on Categories, then Create to create a new category, enter All iOS – Password. This will make it easier later to filter our configuration items for each platform and heading group.
so that it looks look the following example
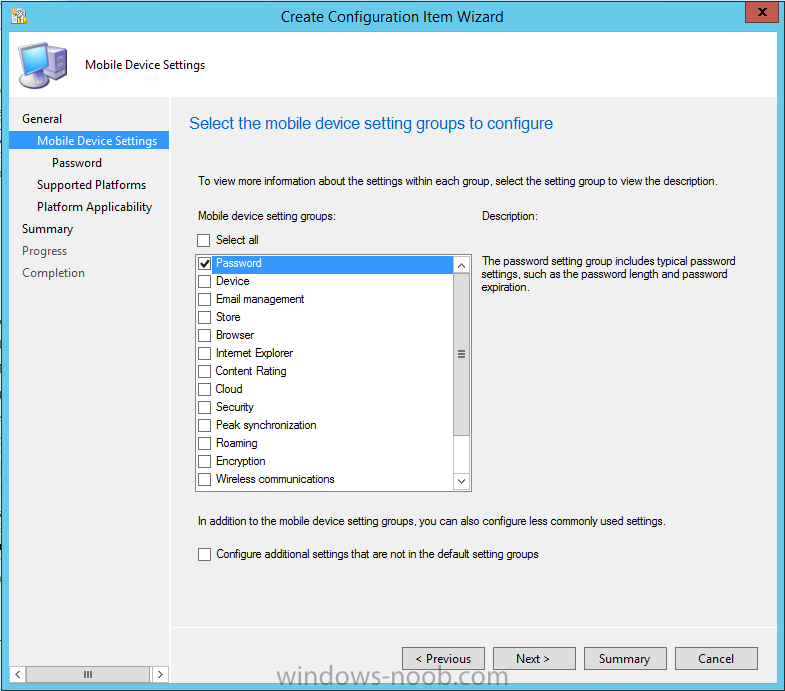
Place a checkmark in the Password default settings group.
click on next and the Password default settings group settings are revealed, we will configure the minimum password length here, set it to a value that works in your organization and change the Require password settings on mobile devices dop down menu to Required and make sure that Remediate noncompliant settings checkbox is checked as shown in the screenshot below.
Tip: Although there are many settings in each default settings group, to make it easier to track compliance for each setting you configure, consider creating one Configuration Item per setting.
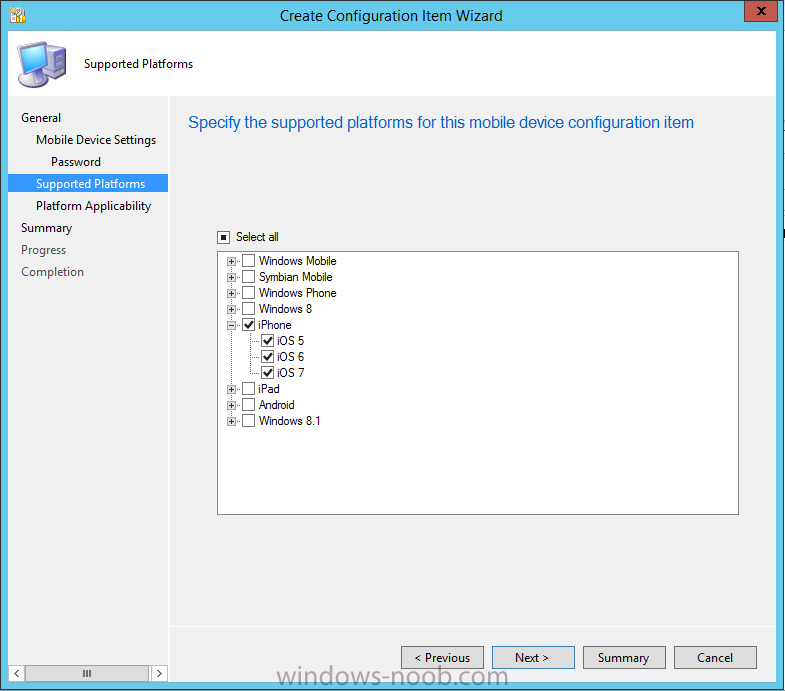
On the Supported Platforms screen you can select the devices you want to support, for example iPhone as shown in the screenshot below, if you choose to select All Systems (default) then the next screen will be populated with those platforms that are not supported by the setting you have chosen.
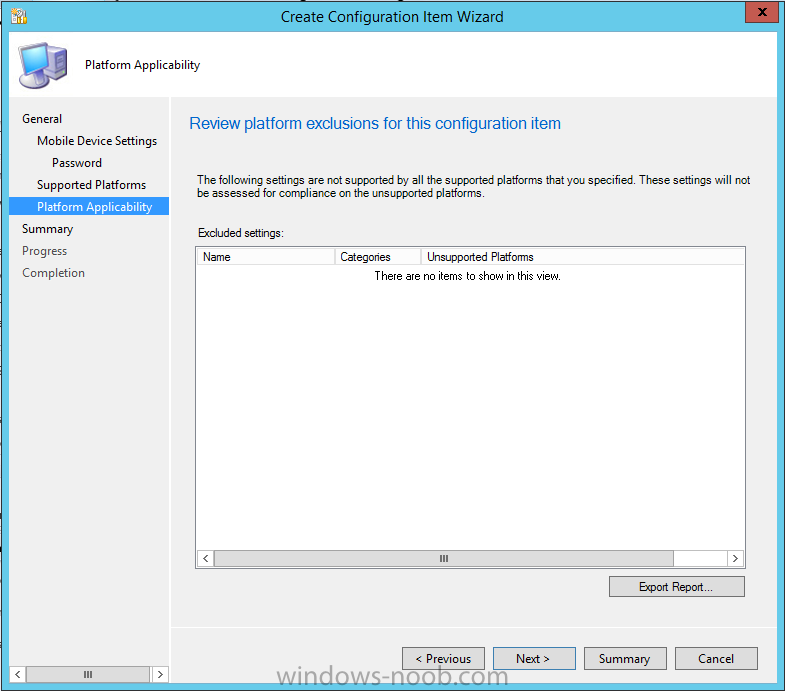
In the Platform Applicability screen any platforms that are NOT supported by the settings you chose will be listed,
complete the wizard
Step 2. Create a Configuration Baseline
Now that we’ve created our Configuration Item, we will add it to a Configuration Baseline. To do that we need to create the baseline. In Configuration Baselines, right click and choose Create Configuration Baseline
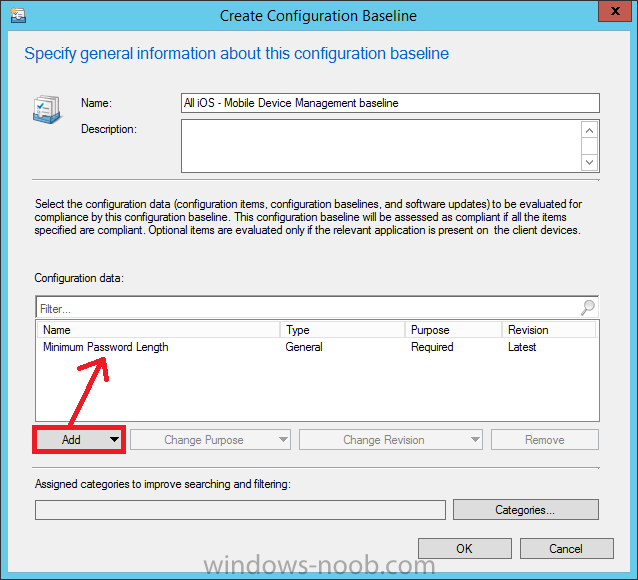
Give it a suitable name like All iOS Mobile Device Management baseline and click on Add, then add our previously created Configuration Item from Step 1.
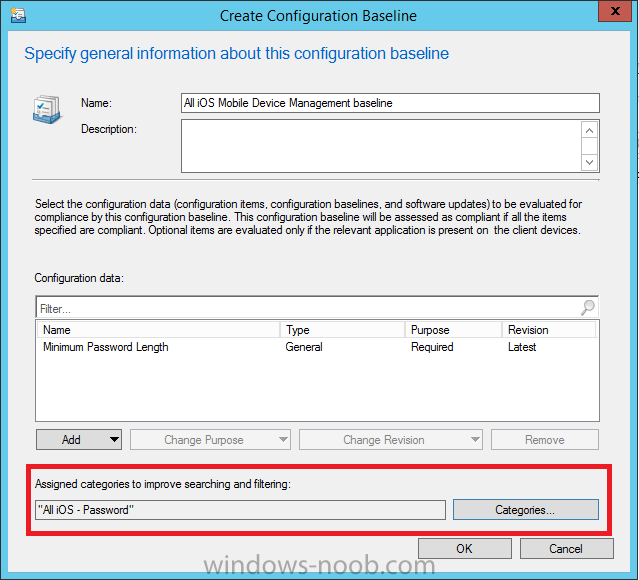
and don’t forget to add any assigned Categories to improve search filtering
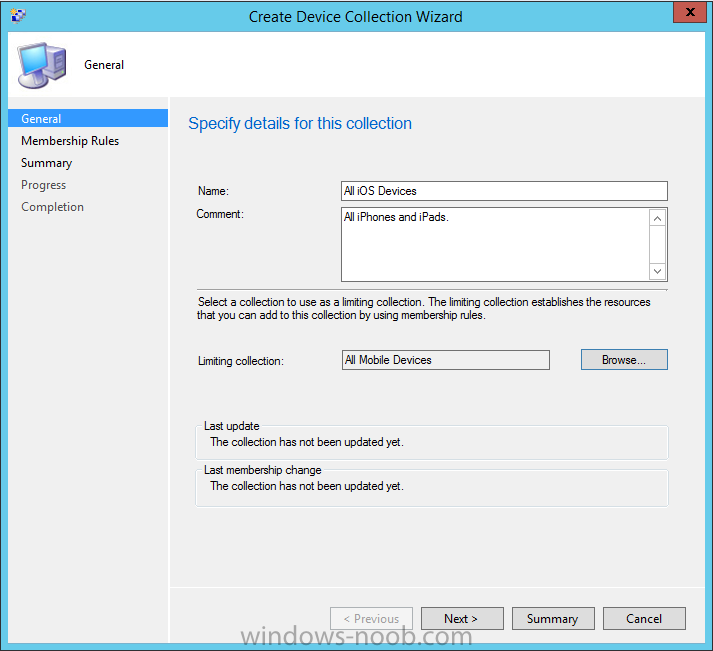
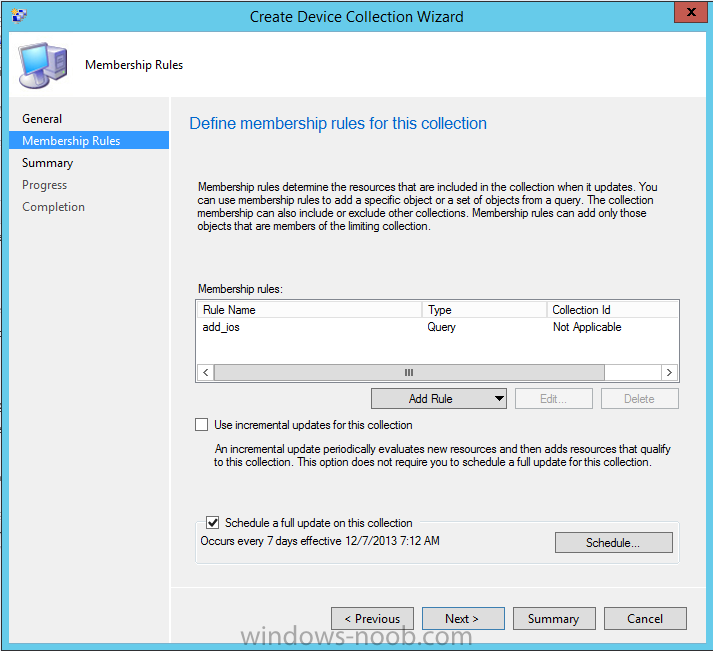
Step 3. Create a new device collection
Create a new device collection called All iOS devices, limit it to All Mobile devices
and setup a membership query to look for Operating Systems like iOS.
select SMS_R_SYSTEM.ResourceID,SMS_R_SYSTEM.ResourceType,SMS_R_SYSTEM.Name,SMS_R_SYSTEM.SMSUniqueIdentifier,SMS_R_SYSTEM.ResourceDomainORWorkgroup,SMS_R_SYSTEM.Clientfrom SMS_R_System where SMS_R_System.OperatingSystemNameandVersion like "iOS%"
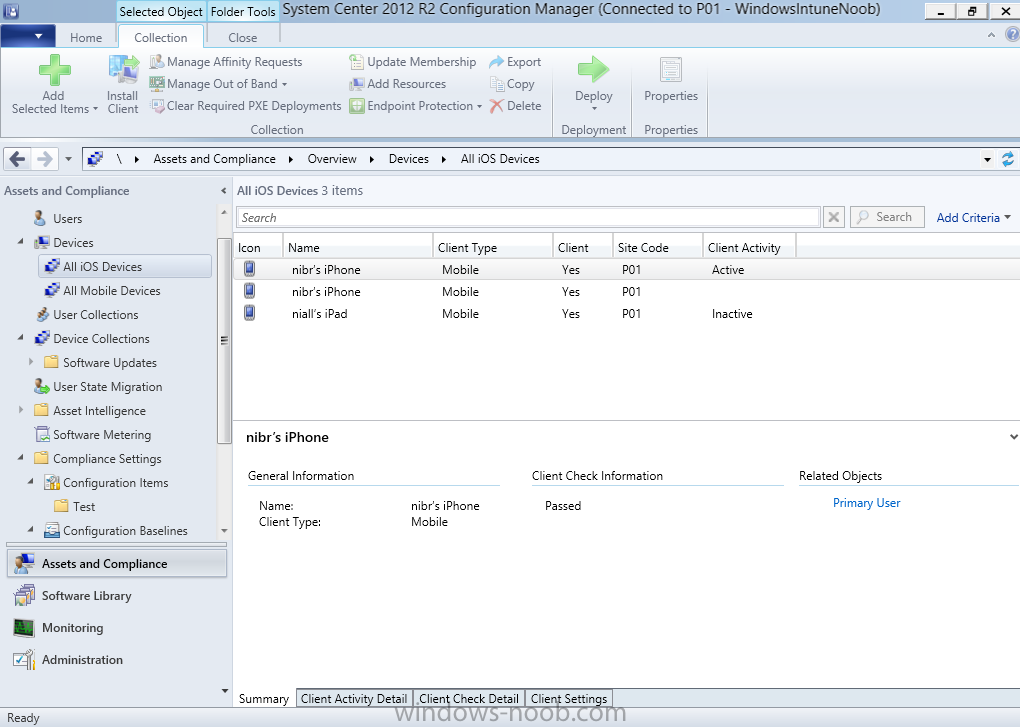
And below is our collection populated with iOS devices after creation
Step 4. Deploy the Configuration Baseline
Now that we have created our configuration item which has compliance rules defined for Password minimum length, and added it to a configuration baseline we are ready to deploy it to a collection.
Note: You can deploy compliance settings for Mobile Devices to a user or device collection. If you deploy the baseline to a user collection, the compliance settings are applied to all the enrolled devices for those users.
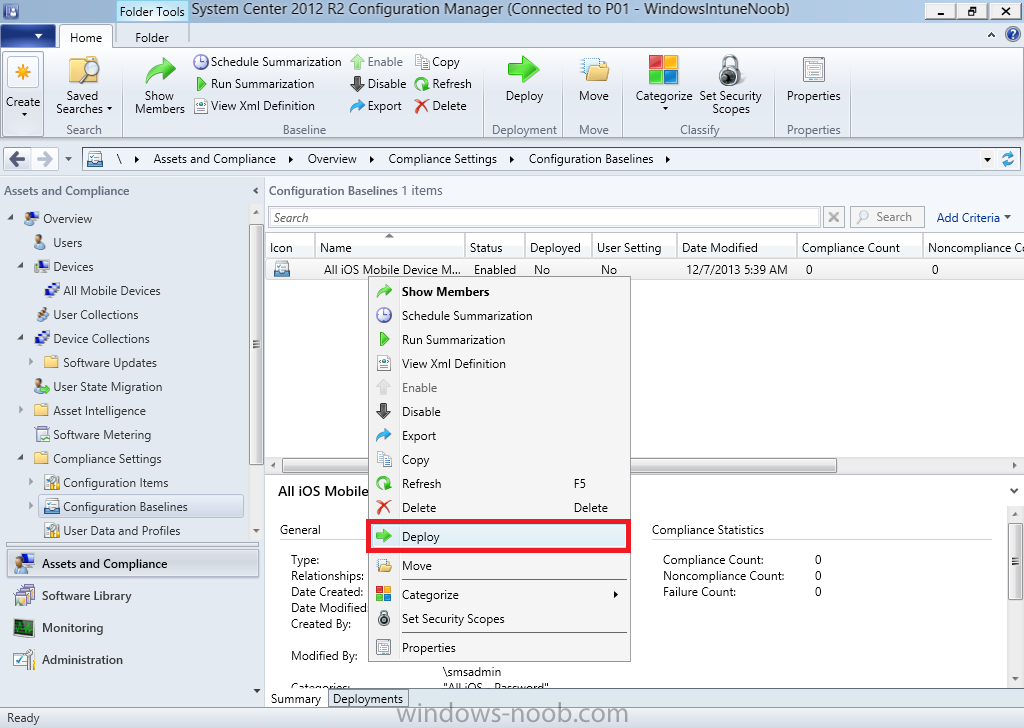
In this example, we will deploy it to our previously created collection called All iOS Devices.
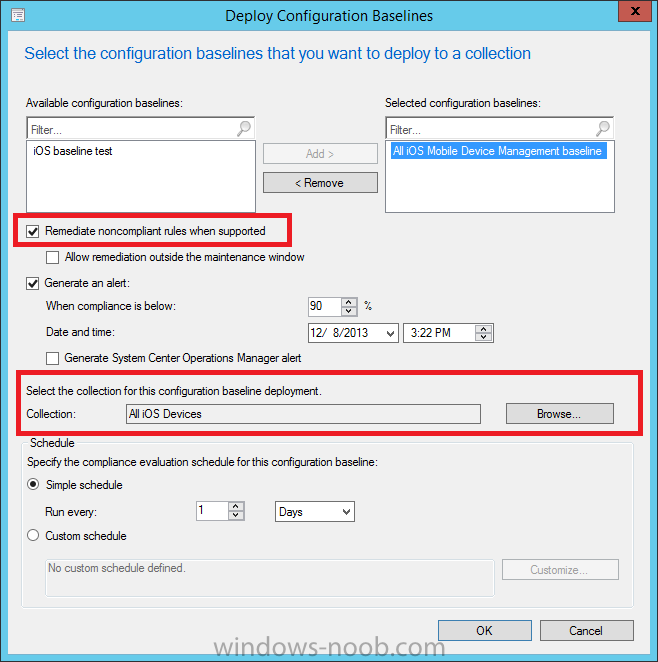
Right click on the All iOS Mobile Device Management baseline configuration baseline created above and choose Deploy.
Place a checkmark in Remediate noncompliant rules when supported and Generate an alert. Next select the browse button beside collection and specify the All iOS Devices collection, select the Schedule to Simple Schedule and set it to run every 1 days.
Step 5. Monitor Compliance using Reports.
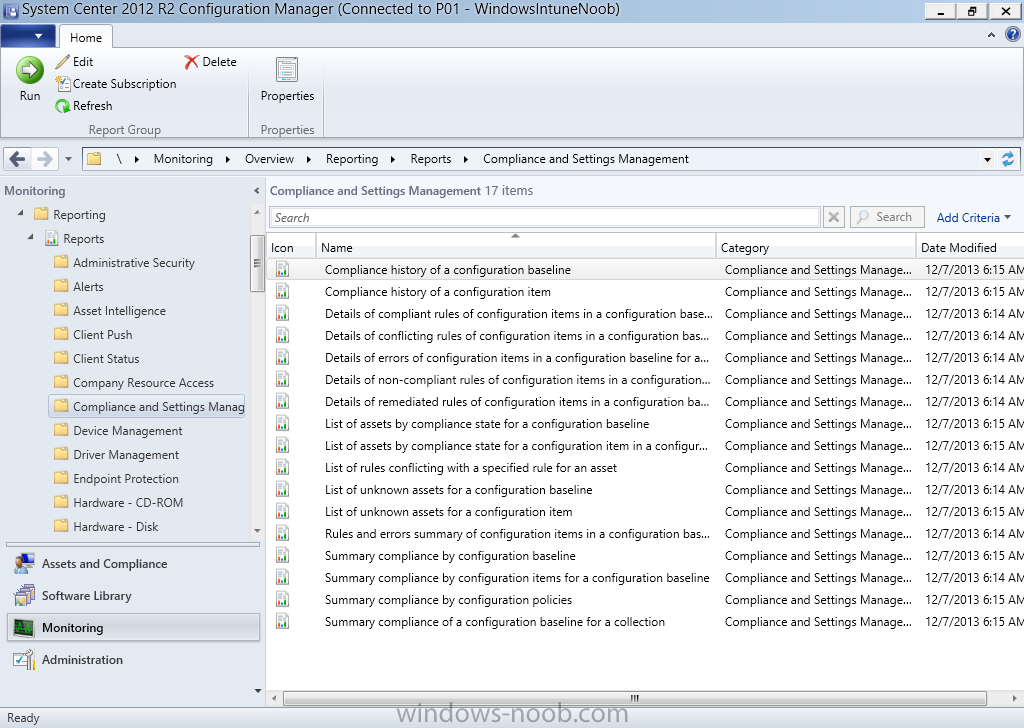
Configuration Manager has several built-in reports including of course reports for Compliance. In the Monitoring node click on Reports, and expand to Compliance Settings Management.
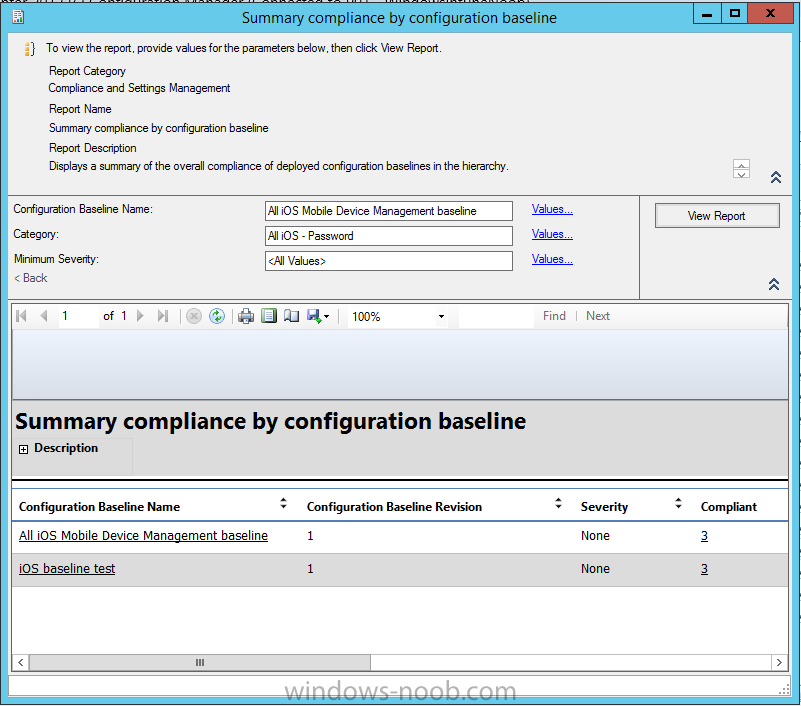
Select the following report, Summary Compliance by a configuration baseline and fill in the values requested
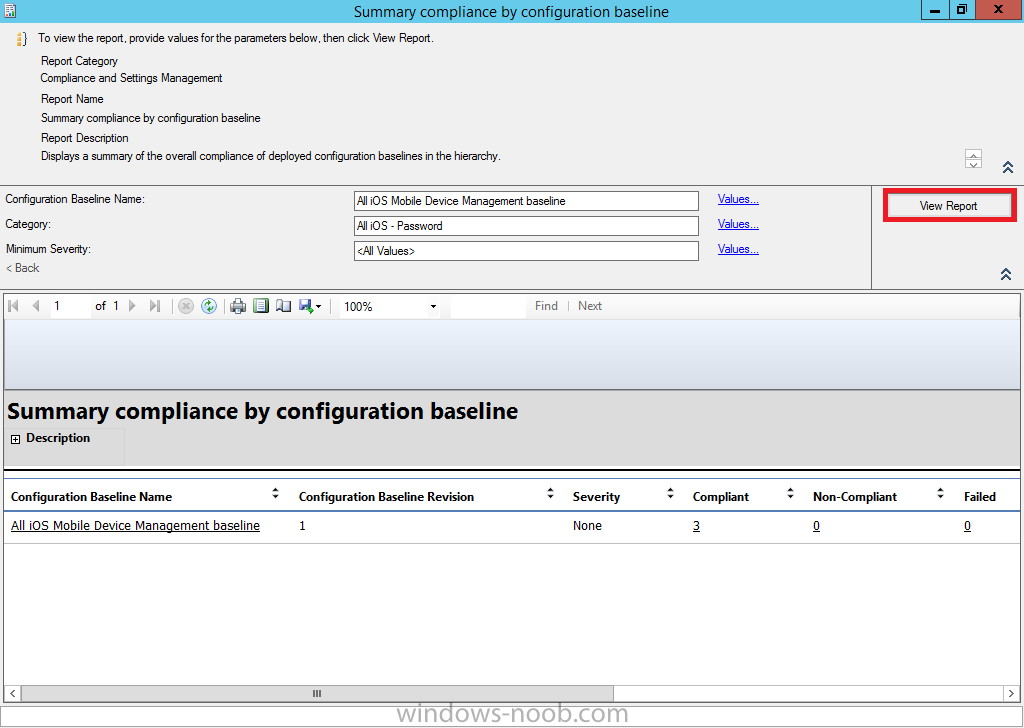
Click on View Report to get details of compliance
and you can drill your way through the compliance reports to see how your Compliance Settings are taking shape !
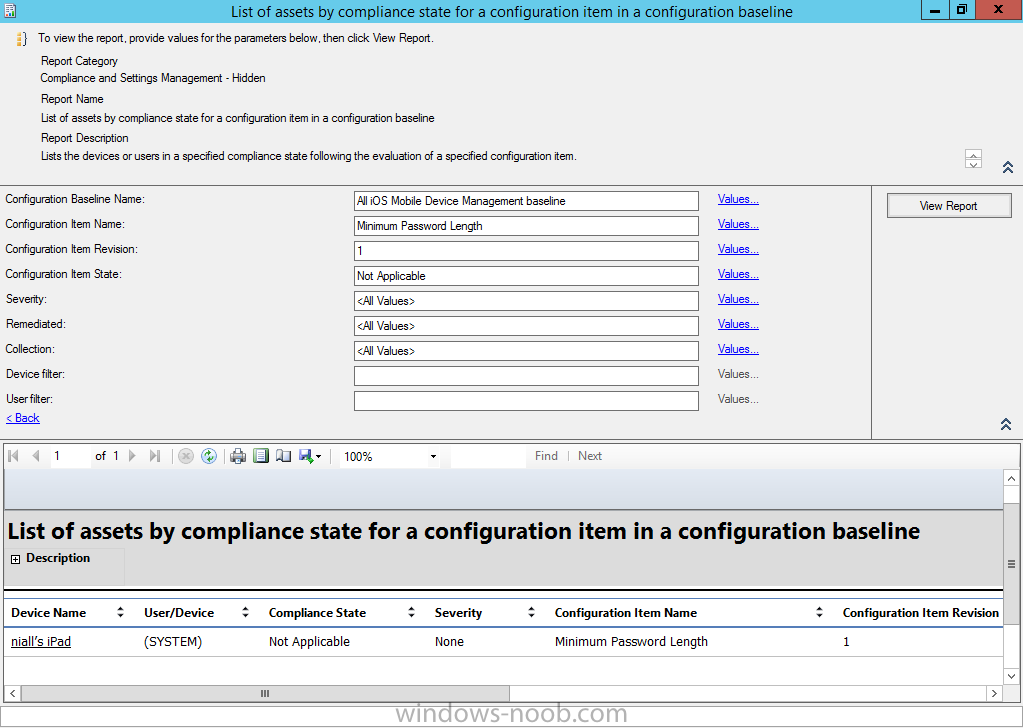
In the screenshot below for example we can see that the compliance state was not applicable as we targeted our configuration item to iPhone IOS only (and excluded iPads).
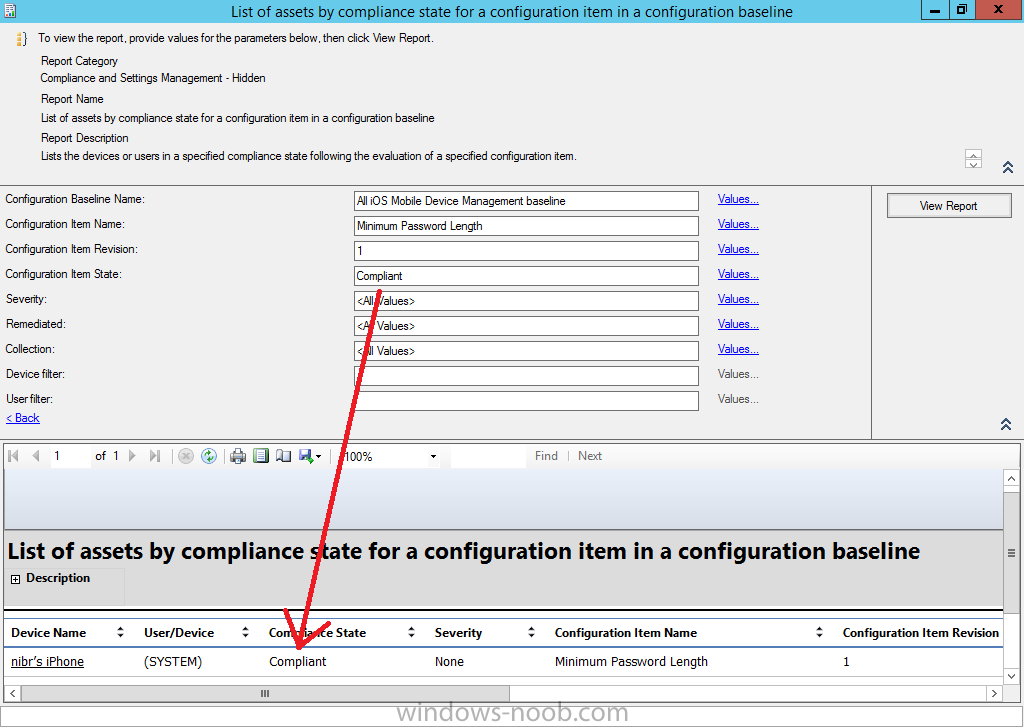
and below we can see a compliant device
Step 6. Verify the settings change on a targeted mobile device
You will of course want to verify the settings change on a mobile device that you have targeted with these compliance settings.
Note: The screenshots below are only related to the change we enforced above (minimum password length) so obviously whatever setting you target to your modern devices will have to be verified accordingly.
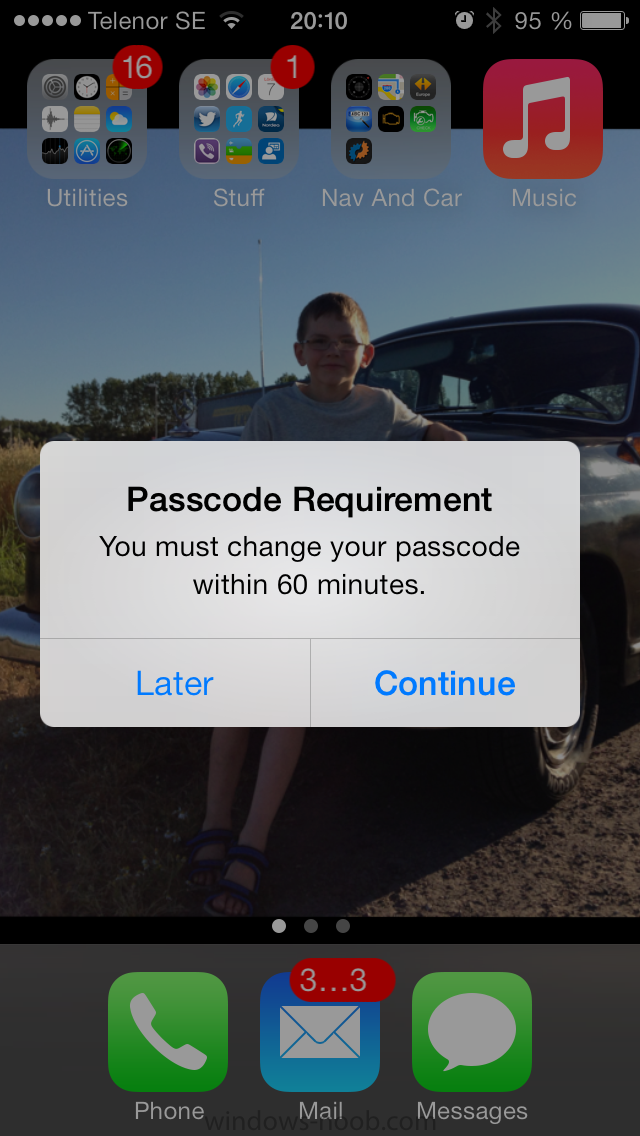
In the first screenshot we can see that the device has received the policy and alerts the user, clicking on continue allows the user to make the change, or the user can delay it (within the deadline of 60 minutes) by clicking later.
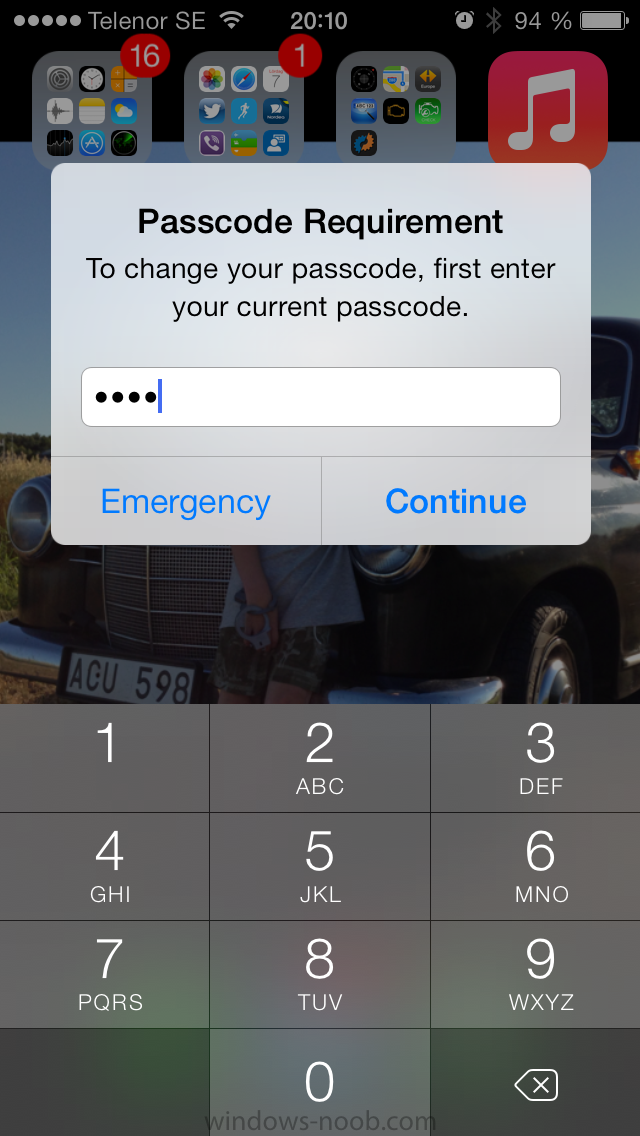
the user is prompted to enter the old password (4 chars in this case)
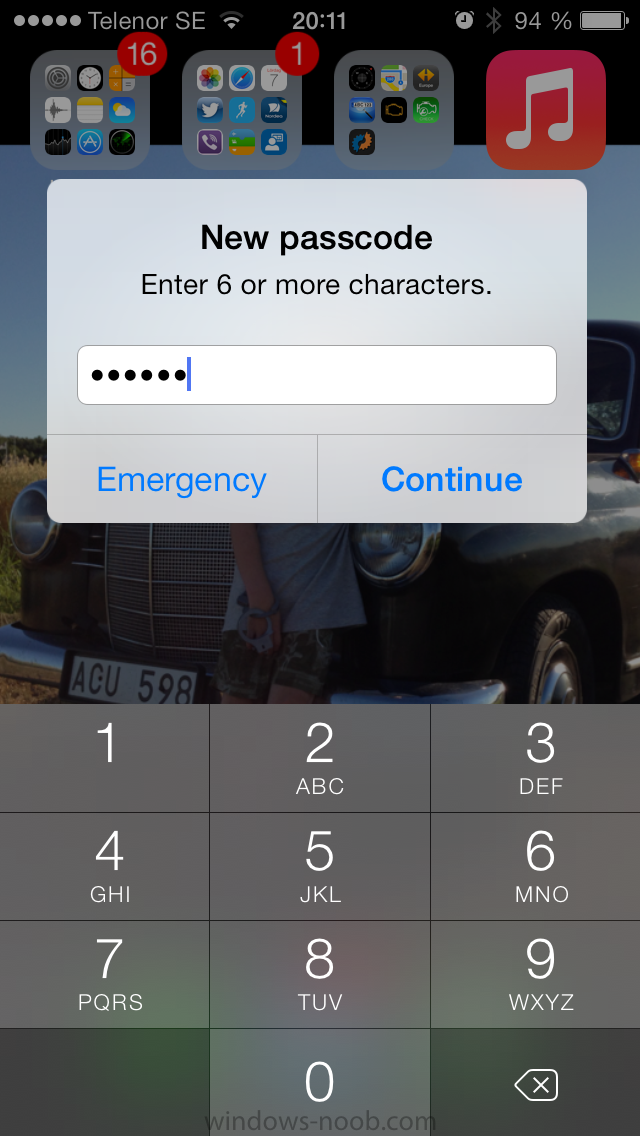
and then the user must enter the new password with 6 characters (from our configured compliance settings)
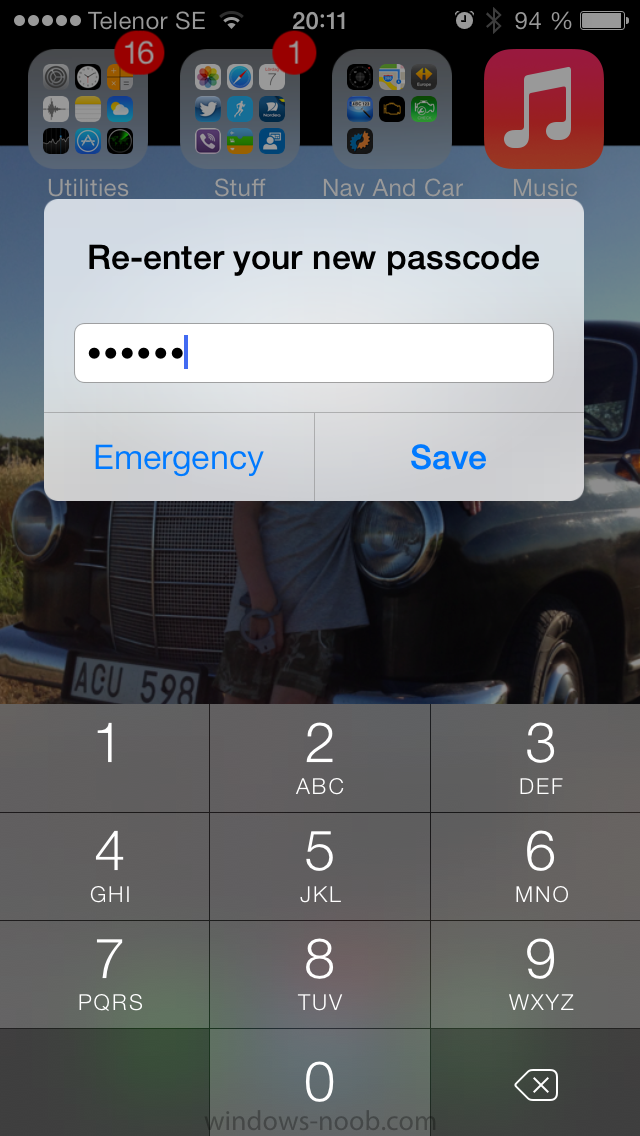
and re-enter it and click on save to confirm
congratulations ! All done.
Recommended Reading
- How to Create Configuration Items for Devices enrolled by Windows Intune and Configuration Manager – http://technet.micro…y/dn376523.aspx
- Adding the Reporting Services Point role – http://www.windows-n…ces-point-role/
- How can I manage modern devices using System Center 2012 R2 Configuration Manager ? – Part 1
- How can I manage modern devices using System Center 2012 R2 Configuration Manager ? – Part 2
- How can I manage modern devices using System Center 2012 R2 Configuration Manager ? – Part 3
Summary
In this part we’ve looked at how we can configure settings on mobile devices using Compliance Settings within Configuration Manager. We then saw how to report on the compliance and finally how to verify those settings were applied on targeted devices. Until next time, adios !