Microsoft recently added a new preview ability to the production version of ConfigMgr 2107.
Aaron tweeted about it here. Below are the prerequisites.
Prerequisites
- Configuration Manager site version 2107 or later
- Apply a Configuration Manager BitLocker management policy to the device.
I tried it out in my lab and here is the result. I tested this on an Azure AD joined device, that was co-managed as described in a previous blog post by myself and Paul here.
I deployed a Windows 10 virtual machine which had the Virtual TPM enabled (hyper-v generation 2 vm) and once the device was in Azure, I added it to my co-managed azure ad devices group.
It got the ConfigMgr client installed (as the client was assigned to that Azure AD group), and the device showed up as in ConfigMgr. Next, I added the device to my BitLocker Management collection in ConfigMgr as you can see here.
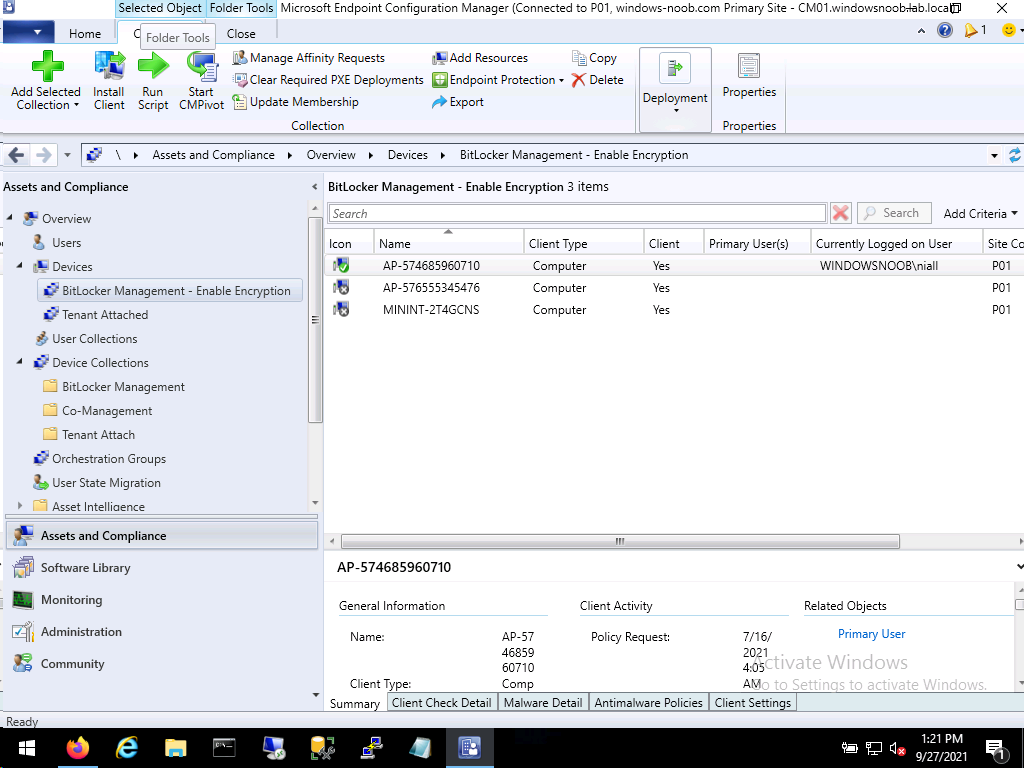 Next, I added the device to my tenant attached collection as we see here.
Next, I added the device to my tenant attached collection as we see here.
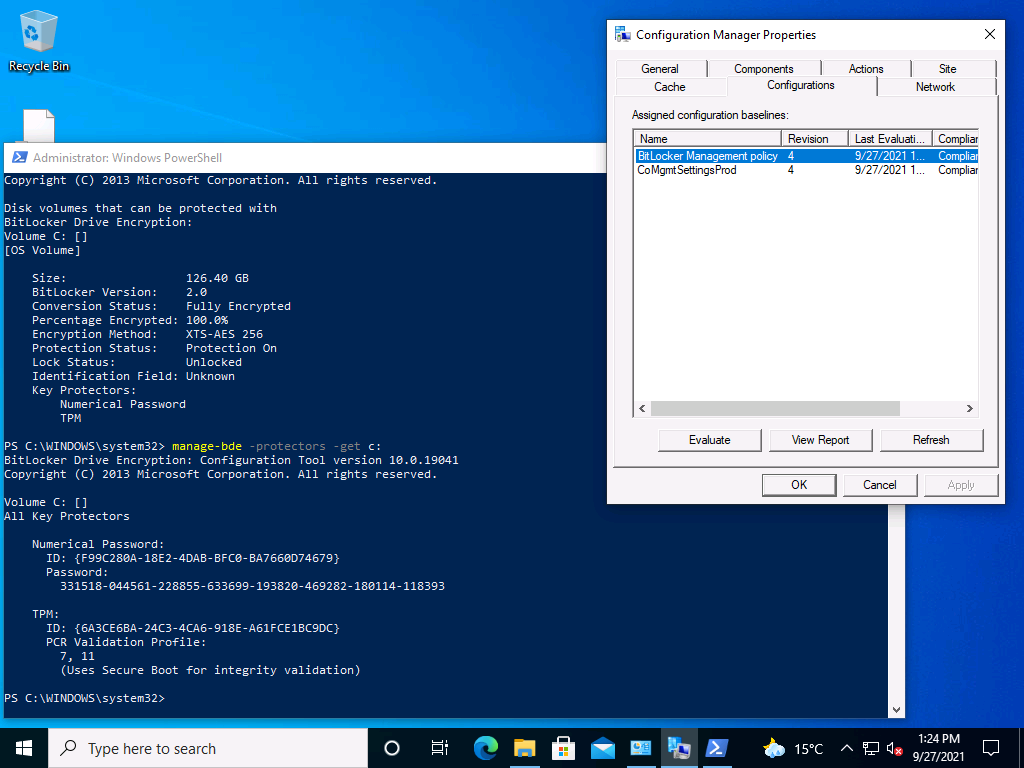
 Once done, I confirmed on the client that it had received the BitLocker management policy and had encrypted. Here we can see the BitLocker policy is compliant and the recovery info is revealed on the client via PowerShell. We did this to verify the results in the Endpoint Management console.
Once done, I confirmed on the client that it had received the BitLocker management policy and had encrypted. Here we can see the BitLocker policy is compliant and the recovery info is revealed on the client via PowerShell. We did this to verify the results in the Endpoint Management console.
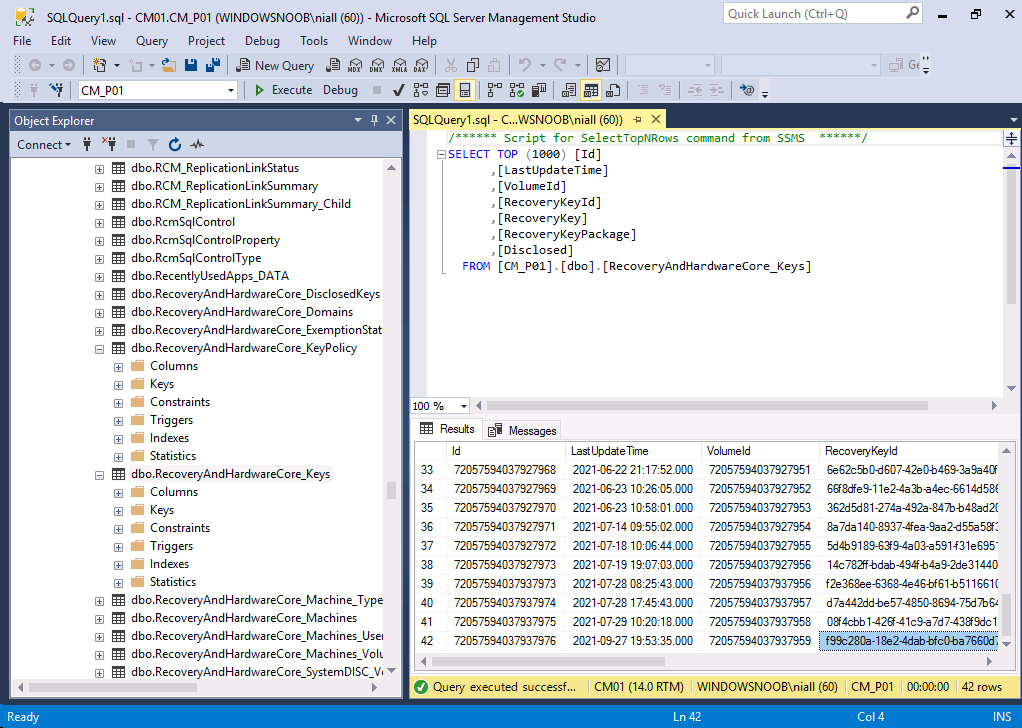
 I also confirmed that the BitLocker information was stored in ConfigMgr’s database, and it was there.
I also confirmed that the BitLocker information was stored in ConfigMgr’s database, and it was there.
Next, I launched a web browser to https://endpoint.microsoft.com and signed in with an administrative user as described below…
Permissions
The administrative user needs the following permissions:
- On the Collection object that’s scoped to a collection that includes the device:
- Read
- Read BitLocker Recovery Key
- An Intune role assigned to the user
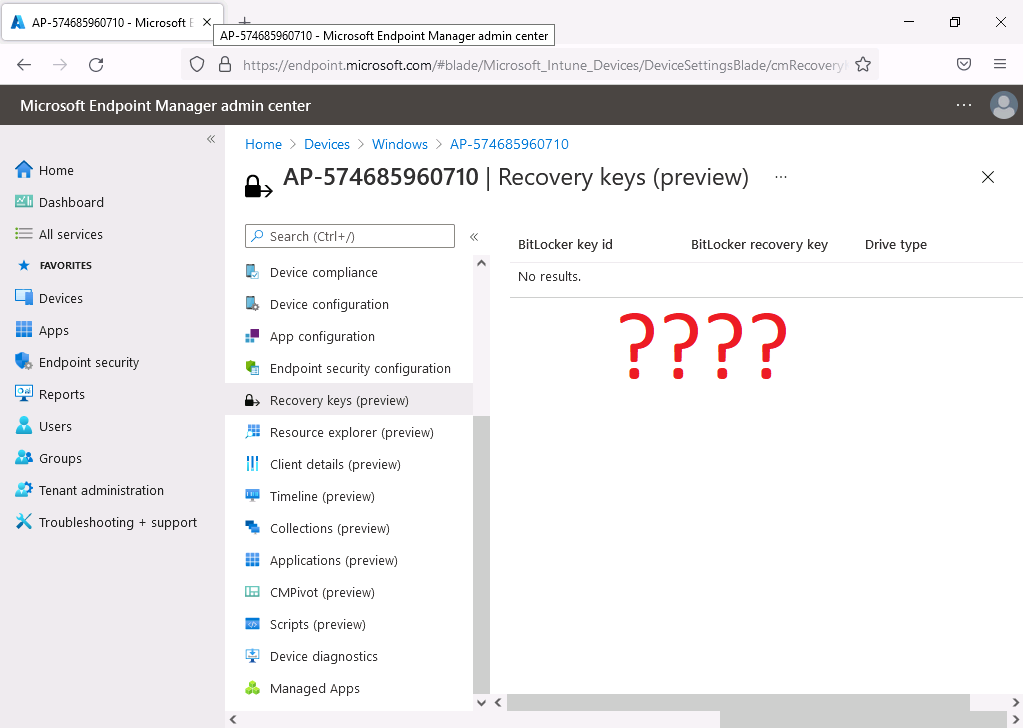
I located my tenant attached device .. clicked on the Recovery keys (preview) but alas, there were no results…
Update
Ok, I worked offline with the Microsoft Product Group (thanks guys) and they identified the issue, long story short, if your tenant attached device is Azure AD joined (like mine was) or hybrid azure ad joined, then the keys would not get uploaded to MEM.
The Fix
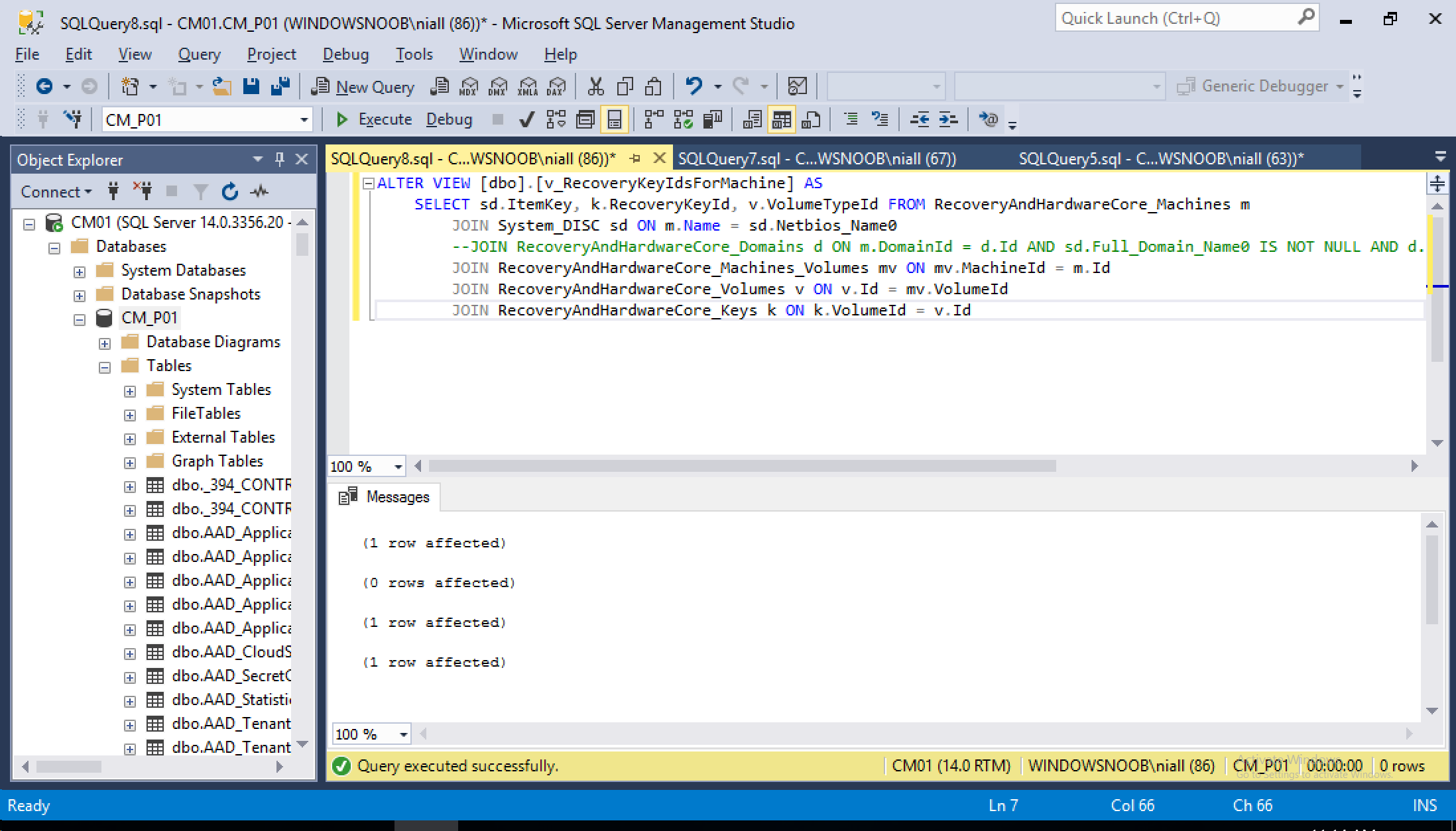
The fix is coming soon via a hotfix, but if you want to resolve this yourself then use the following SQL
ALTER VIEW [dbo].[v_RecoveryKeyIdsForMachine] AS SELECT sd.ItemKey, k.RecoveryKeyId, v.VolumeTypeId FROM RecoveryAndHardwareCore_ Machines m JOIN System_DISC sd ON m.Name = sd.Netbios_Name0 --JOIN RecoveryAndHardwareCore_ Domains d ON m.DomainId = d.Id AND sd.Full_Domain_Name0 IS NOT NULL AND d.DomainName = sd.Full_Domain_Name0 JOIN RecoveryAndHardwareCore_ Machines_Volumes mv ON mv.MachineId = m.Id JOIN RecoveryAndHardwareCore_ Volumes v ON v.Id = mv.VolumeId JOIN RecoveryAndHardwareCore_Keys k ON k.VolumeId = v.Id
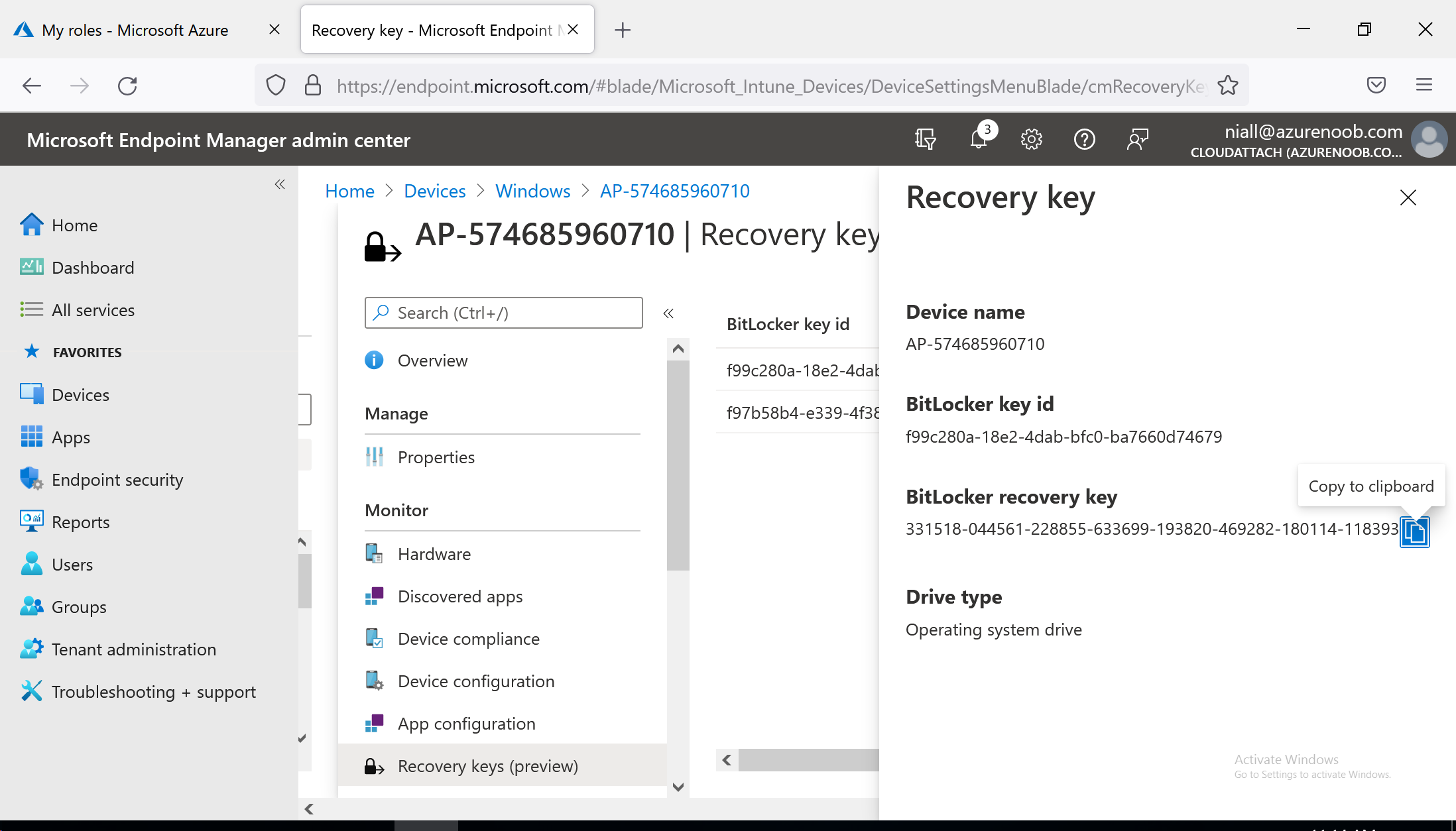
 After running that, I checked the MEM console and the recovery info was present, what a result !
After running that, I checked the MEM console and the recovery info was present, what a result !
Big thanks go to the Aaron and all the rest of the Microsoft Product Group for taking the time to investigate this with me.
Conclusion
Being able to retrieve data from Tenant attached devices using Microsoft Endpoint Manager and without needing to install a Configuration Manager Console is a great ability indeed.
Especially for things like this, BitLocker recovery info when the technician needs to help a user quickly.