Introduction
These are my notes about a session I’ve attended at Microsoft Ignite 2019, you can review the recording for this session here. I’ve split this blog post up into different parts as there is just so much content to be covered.
- Part 1 – Partnerships
- Part 2 – Deployment Scenarios
- Part 3 – Dedicated Device Management
- Part 4 – Coming soon and what’s new
My goal with blogging this is to make sure I didn’t miss anything and to understand all the new capabilities properly and of course, to help you understand it too.
In the following screenshot, you can see the long term Android deployment scenarios supported by Microsoft Intune.
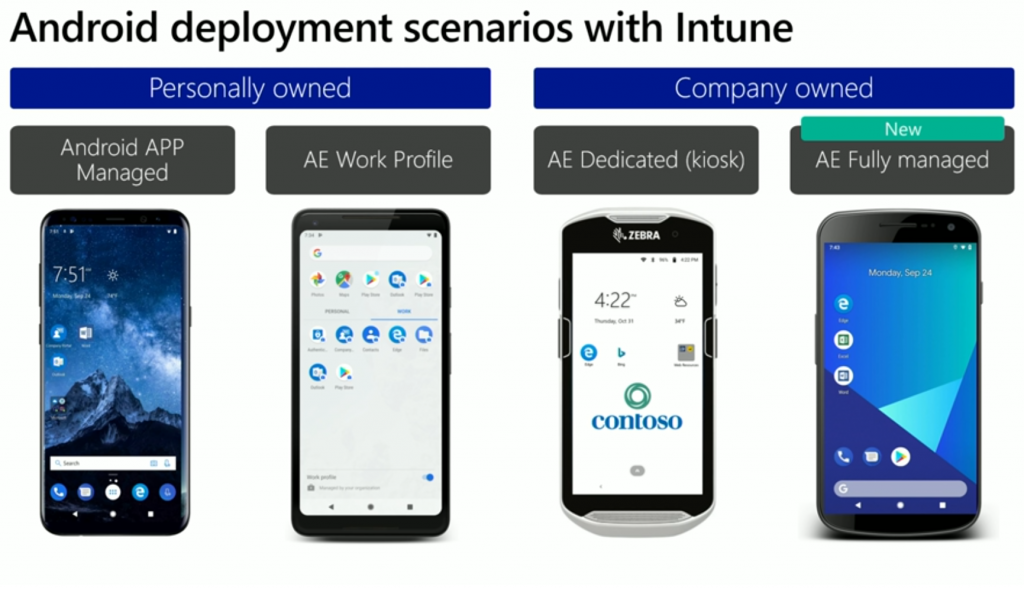 These deployment scenarios can be split up into two main categories:
These deployment scenarios can be split up into two main categories:
- Personally owned devices (BYOD)
- Company owned devices
Microsoft’s goal is to provide support for everything you can do on Android because there is an incredible diversity of use-cases and they want to help you decide which one you fit into and which one is best.
The AE Fully managed scenario which was released in Intune in September 2019 is a great Corporate Owned device scenario for when you want to have productivity oriented devices assigned to a specific user. Microsoft had thousands of devices in the preview of this ability prior to launching, and it was very successful.
The one thing missing in the Android deployment scenarios above is Fully managed with work profile (COPE). COPE stands for Corporate Owned, Personally Enabled, which is interestingly (by Google) depreciated as a term. To get an overview of the different scenarios see this link:
https://developers.google.com/android/work/terminology
This is partly due to a dependency on Google as Google is finishing up their support for this as part of the Google management API. Microsoft is working jointly with them and progressing rapidly through design and engineering and they’ll provide a timeline of this support (for COPE) in the future.
BYOD
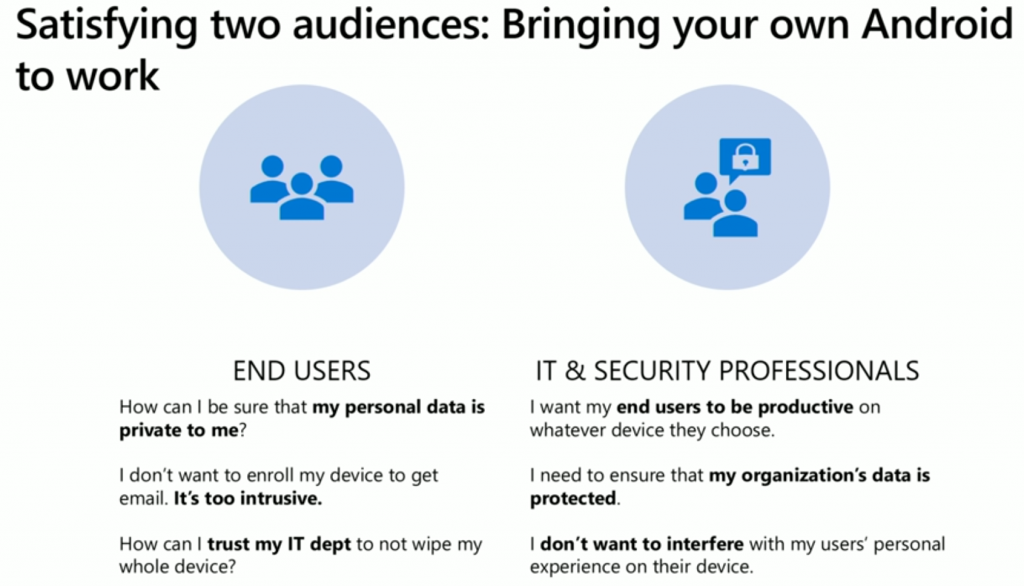
BYOD or Bring your own device (or disaster ;-)) is a challenging scenario as learned by Microsoft from it’s customers. It’s sounds easy, bring your own device, bring anything, but in reality it’s difficult for the IT Professional who is stuck between the end users who are very vocal and passionate about the devices they paid for and then you’ve got the corporate interests the IT Professional is hired to protect.
The below slide gives you some examples of what end users typically complain about, versus what the IT Professional needs to accomplish.
For BYOD there are two options that Microsoft Endpoint Manager provides.
- App Protection Policies without enrollment
- Android Enterprise work profile
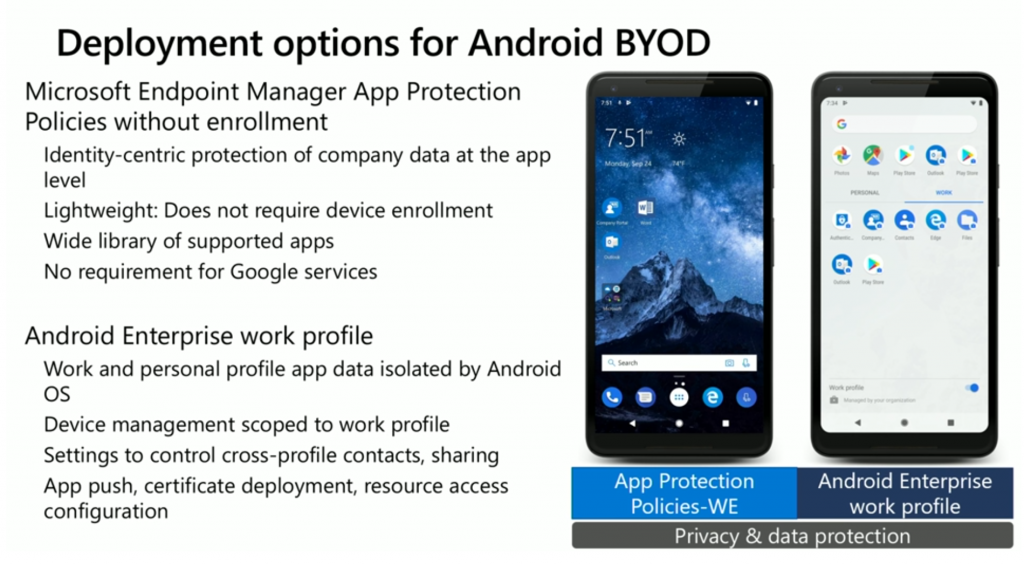 The first option is the data protections that are built into Microsoft applications (for Android) including lots of third party applications also, where the applications themselves are instrumented to understand data-protection policies. It is identity centric meaning that the (for example) email application itself doesn’t react if the user is doing personal stuff (personal email for example) but kicks into action if the user flips over to corporate email, and that’s when the protection kicks in and there are restrictions on the data, however it is light weight as it does not require any device enrollment. There are also tools to onboard applications into this mode, there’s an SDK.
The first option is the data protections that are built into Microsoft applications (for Android) including lots of third party applications also, where the applications themselves are instrumented to understand data-protection policies. It is identity centric meaning that the (for example) email application itself doesn’t react if the user is doing personal stuff (personal email for example) but kicks into action if the user flips over to corporate email, and that’s when the protection kicks in and there are restrictions on the data, however it is light weight as it does not require any device enrollment. There are also tools to onboard applications into this mode, there’s an SDK.
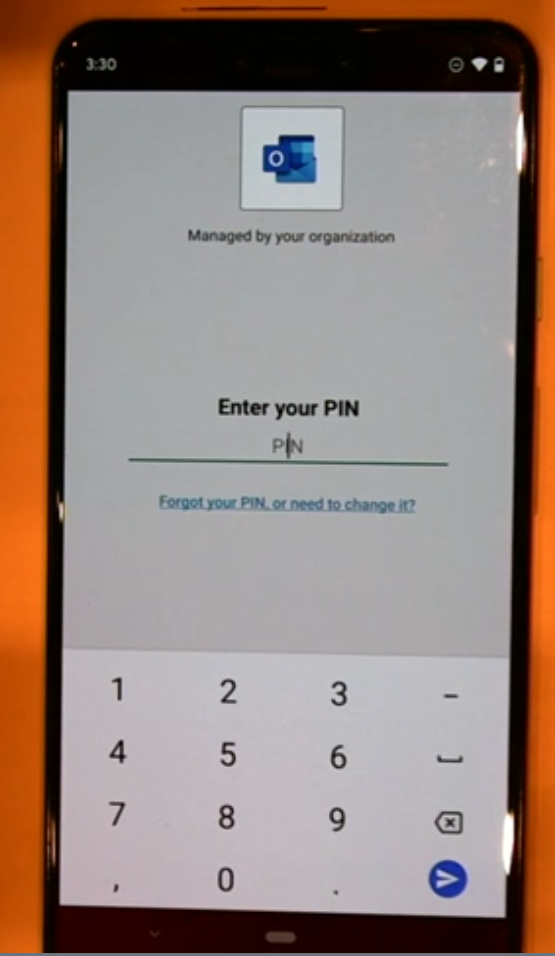
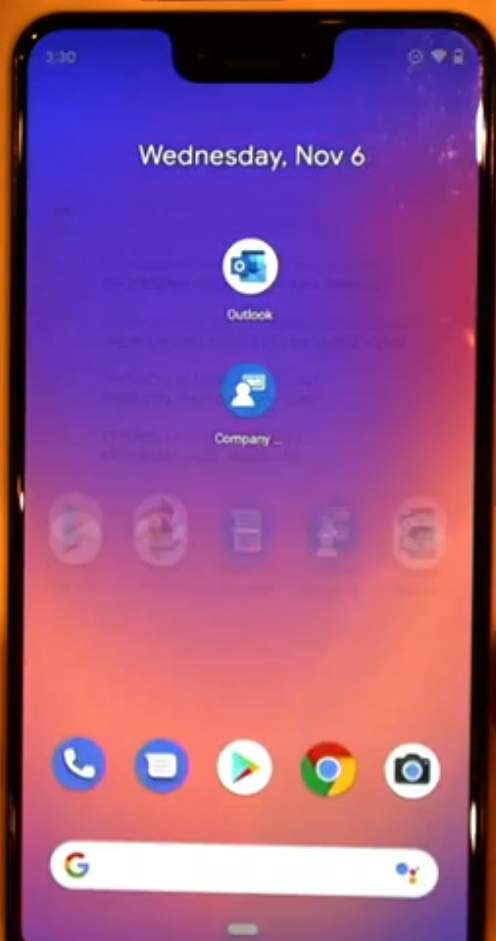
Below is an example of these application protection policies without enrollment, using Outlook connected to a corporate profile on an un-enrolled Android device. You can see Outlook (the application) prompting for a PIN even though the device is not enrolled, that is a protection layer built into the application.
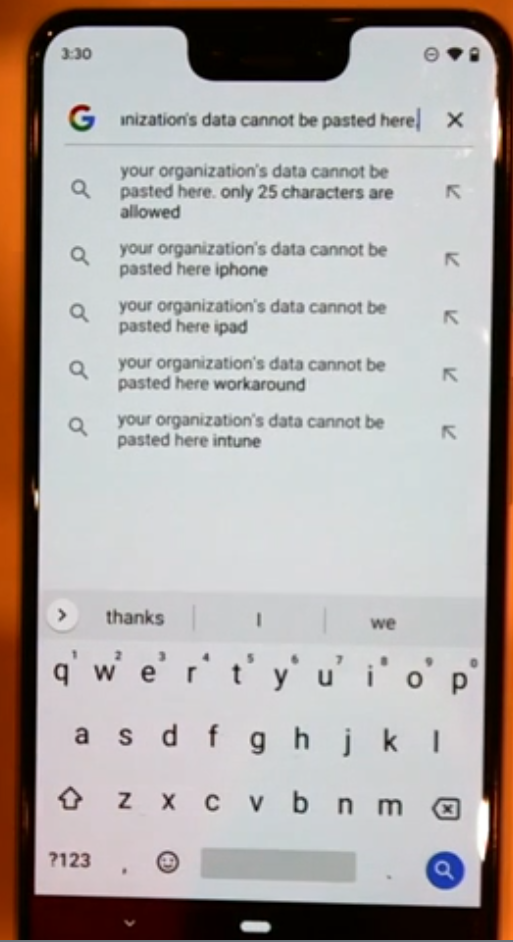
Next, if the user tries to copy data from the Outlook app and paste it outside of the app, the user is denied and gets a message explaining why.
Your organization’s data cannot be pasted here.
 If you want this protection on Line Of Business applications as well you can use Managed Google Play.
If you want this protection on Line Of Business applications as well you can use Managed Google Play.
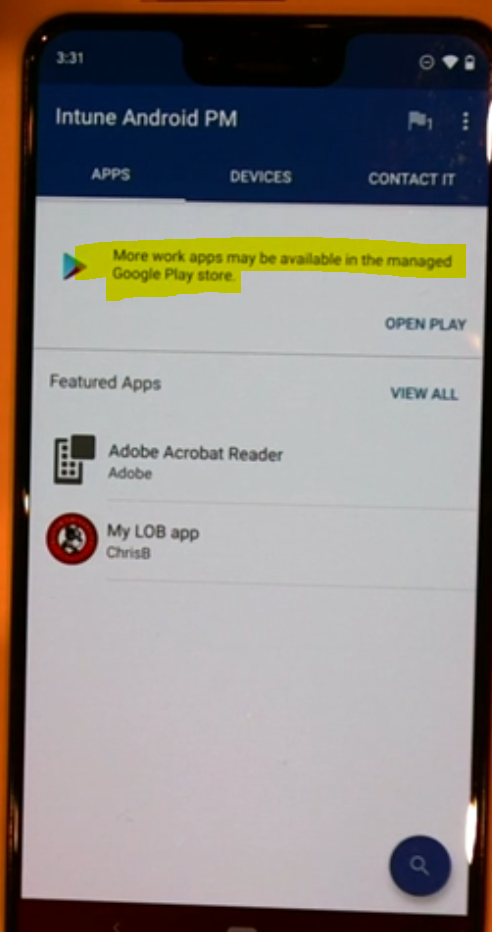
If the user opens up the Company Portal (blue and white icon in the center of the screen).
and if they admin has targeted a managed google play application within the company portal console (deployed as with or without enrollment), and if there are active application protection policies on the device, the user will see a notification that More work apps may be available in the managed google play store.
Clicking on that notification message will open the corporate application catalog, this can contain line of business applications and store applications.
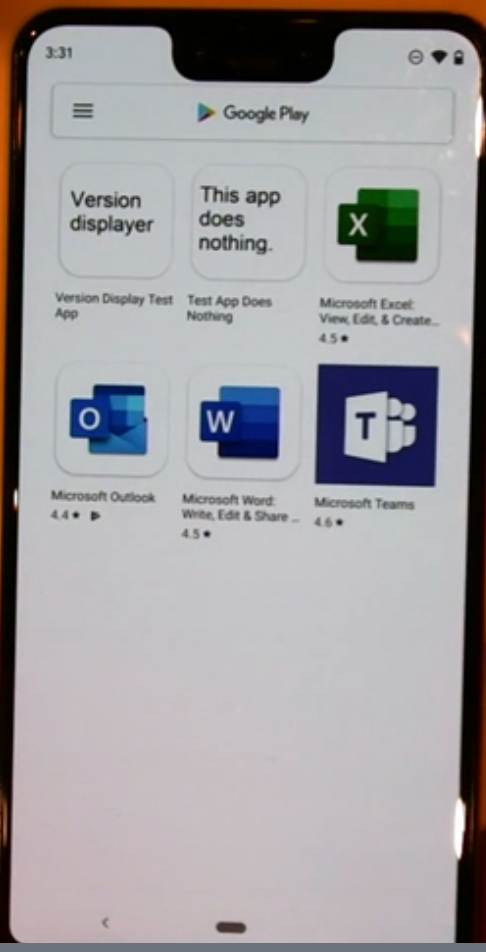 And by clicking on the hamburger icon (three horizontal bars in the top left) the user can flip between the corporate google play and the regular google play.
And by clicking on the hamburger icon (three horizontal bars in the top left) the user can flip between the corporate google play and the regular google play.
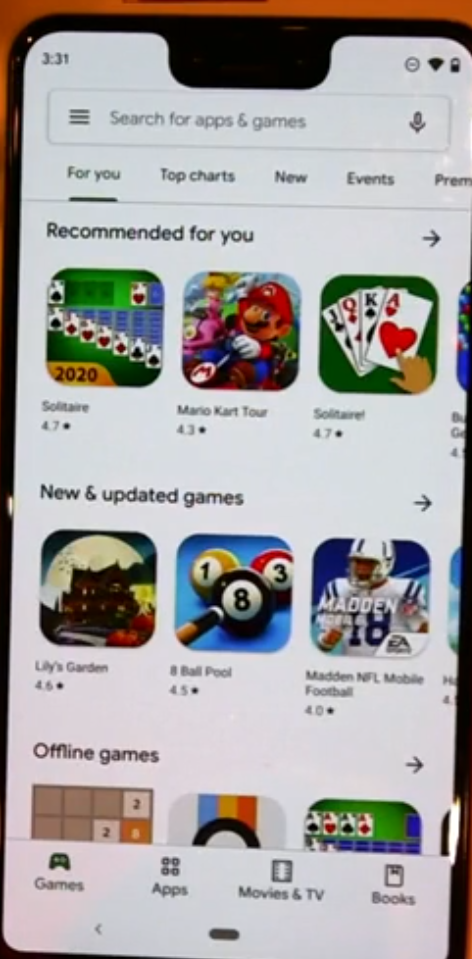 Switching back to the company google play you can install LOB apps which can get downloaded and installed from the managed google play private section which is only available to your particular tenant.
Switching back to the company google play you can install LOB apps which can get downloaded and installed from the managed google play private section which is only available to your particular tenant.
This allows you to distribute Line of business applications to your users without turning on Unknown Sources.
Android Enterprise work profile
This has been in place since Android 5.0 (Lollipop) and is supported by Microsoft Intune, and work and personal separation comes from the Android operating system, when there is a work profile defined.
When you enroll one of these devices into Intune you have a Wipe button in the console that can not nuke the entire device, it can only remove the work profile leaving the users data completely untouched. Most device management stuff is scoped towards the work profile with a few exceptions like device PIN and encryption.
This is perfect for required application deployment or certificate deployments or even resource access configuration. All of this is designed with privacy for the end user, and data protection for the company in mind.
Company owned
Now that you know how to manage personal devices (BYOD), you need to tackle the other half, namely company owned devices.
Company devices just by definition are going to require a lot more management and a lot more stringent controls on what capabilities you want exposed will be enforced on them. Microsoft Intune supports two device types fully, summarized in the bullets below.
- Android Enterprise Dedicated (configured for a specific function, eg: factory floor device, shared among multiple users)
- Android Enterprise Fully Managed (corporate purchased, assigned to single user)
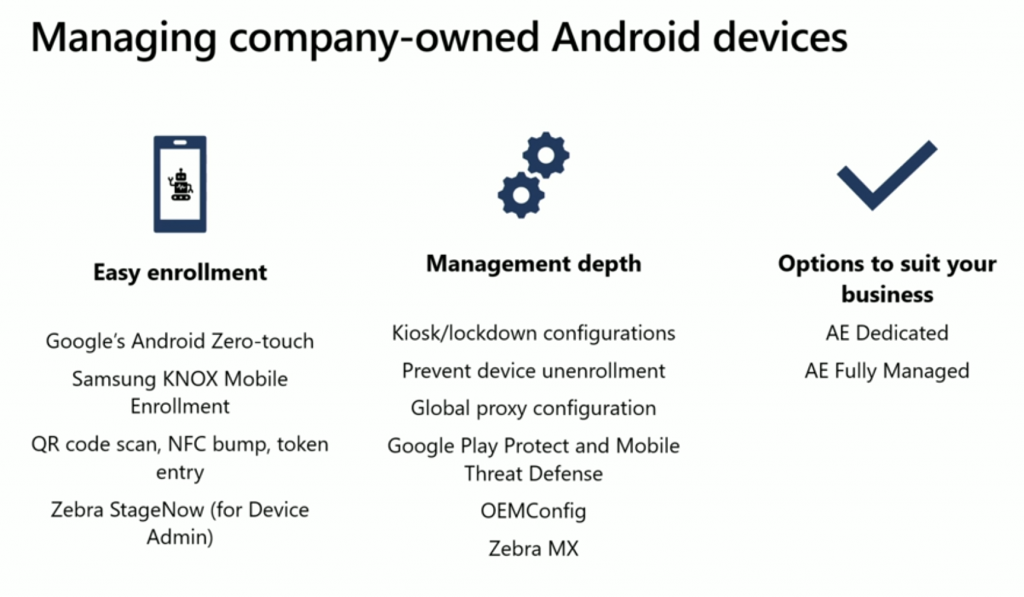 As a corporate device, you get easy enrollment and that depends on the device you choose, be it Google’s Zero Touch or Samsung KNOX mobile enrollment, or QR codes the user can scan, or utilizing Zebra’s StageNow capability. There is no migration from a personal device into a corporate owned device.
As a corporate device, you get easy enrollment and that depends on the device you choose, be it Google’s Zero Touch or Samsung KNOX mobile enrollment, or QR codes the user can scan, or utilizing Zebra’s StageNow capability. There is no migration from a personal device into a corporate owned device.
Once the device is enrolled, how do you configure it to meet your needs and requirements. Intune supports the full spectrum of settings that the platform supports for these devices.
Specialized Features
So in addition to enabling the general settings such as PIN management and USB settings, you can now use Intune to do a lot more for example:
- Lockdown kiosk mode
- Prevent factory reset (to keep it company managed)
- Enforce global proxy configuration
- Device will support Mobile Threat Providers
OEM Features
In addition to these platform settings many devices have settings that are OEM specific that you can configure by enabling OEMConfig. For more details see:
https://docs.microsoft.com/en-us/intune/configuration/android-oem-configuration-overview
A note about Zebra devices
Zebra devices due to their usage are inherently corporate owned. Some of the devices are enterprise capable today but there are many Zebra devices today that are still not enterprise capable and those legacy devices can be brought into Intune via Zebra StageNow as well as distribution of the MX profile which you create via StageNow through Intune to your enrolled devices. This way all your Zebra devices whether they are AE (Android Enterprise) capable or not, are able to be managed by Intune via a single pane of glass.
Android Enterprise Fully Managed
This is intended for a company owned device assigned to a single user. Depending on how you set it up, the user is asked for corporate credentials.
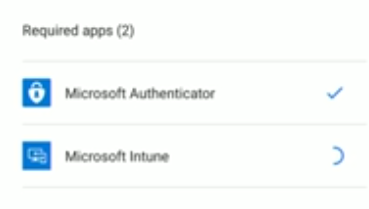
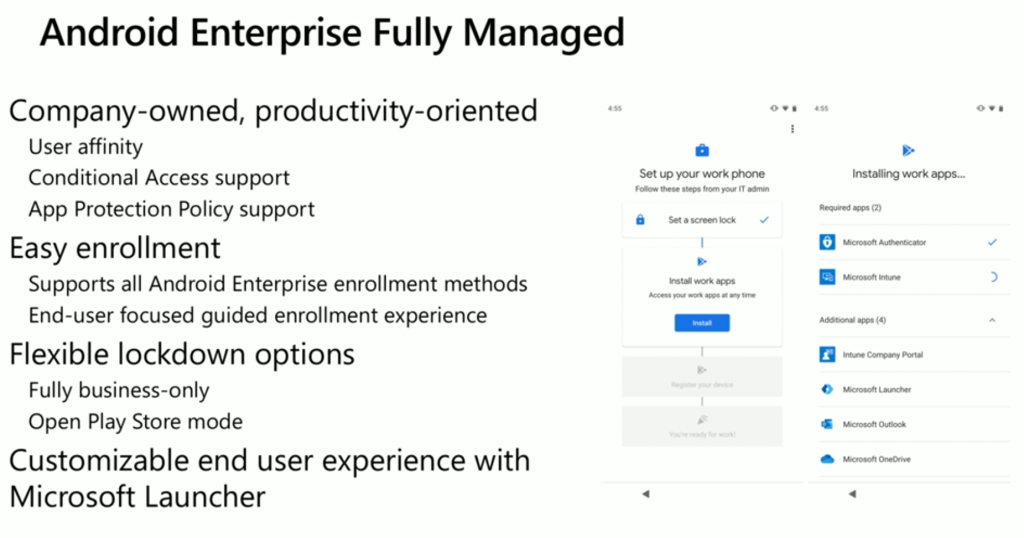 Once those corporate credentials are entered, the user is guided through a workflow. Eg: enter and configure PIN, download apps. The two apps that would be downloaded would be the:
Once those corporate credentials are entered, the user is guided through a workflow. Eg: enter and configure PIN, download apps. The two apps that would be downloaded would be the:
- Microsoft Authenticator app
- Microsoft Intune app
This ensures the user follows the steps necessary to get the device into the correct state for management (enrolled and registered into Intune), the user cannot exit the device provisioning until it’s complete.
Post provisioning, you can leverage Intune’s compliance policies and conditional access to make sure that the device stays in compliance and you can use app protection policies to provide an additional layer of protection for your corporate data.
Company owned (corporate) devices are by default, in business only mode. What this means is you can only access apps that are pre approved by the admin.
Allow the end user to install apps from Google play
You can simply make a change to put the device into open play store role mode. This allows the user to go ahead and add their personal Google play account, and download some consumer apps from the google play store side-by-side.
Microsoft Launcher for Enterprise
You can use this functionality to standardize your end user experience by pinning apps to the home screen or deploying a branded wallpaper or control search bars.
A look at company owned devices
In the screenshot below you can see a message in the bottom of the Android screen where it states that:
This device is managed by your organization.
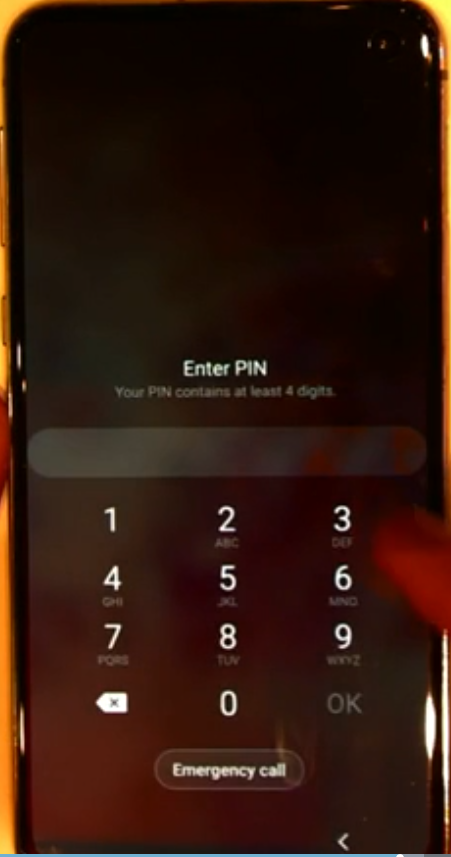
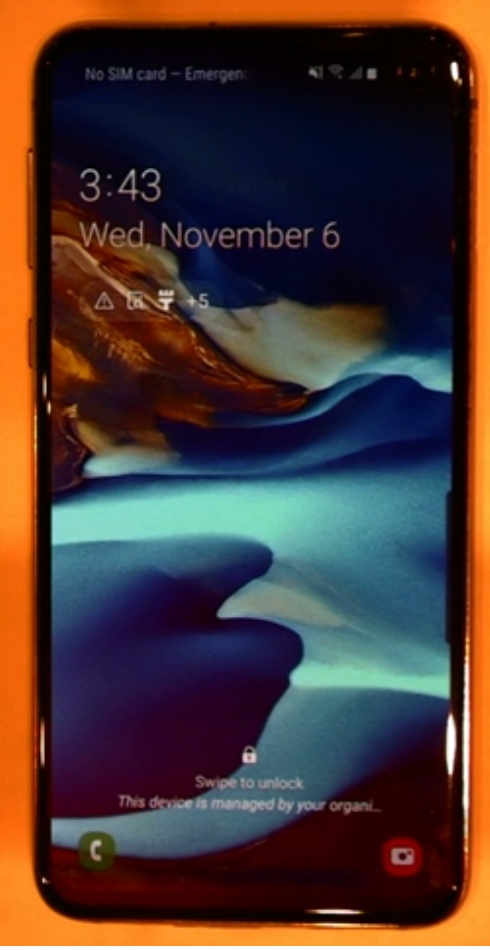 As it’s a Company (corporate) owned device you have decided that a PIN is required to access it.
As it’s a Company (corporate) owned device you have decided that a PIN is required to access it.
 And below you can see the custom wallpaper applied and the two required applications are shown using Microsoft Launcher.
And below you can see the custom wallpaper applied and the two required applications are shown using Microsoft Launcher.
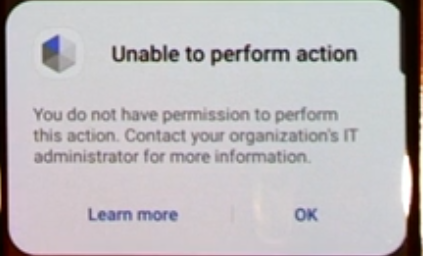
 And if the user attempts to factory reset the device, they are greeted with the following message.
And if the user attempts to factory reset the device, they are greeted with the following message.
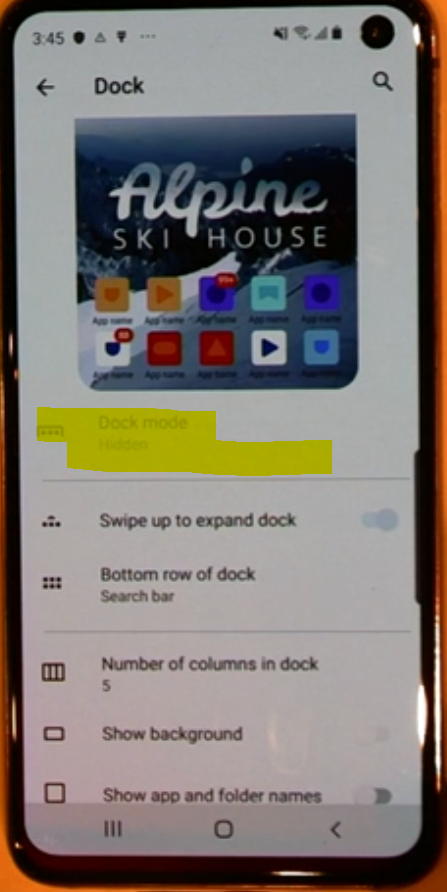
 Also with Microsoft Launcher, you can customize what the end user can and cannot do on their device for example by disabling Dock mode.
Also with Microsoft Launcher, you can customize what the end user can and cannot do on their device for example by disabling Dock mode.
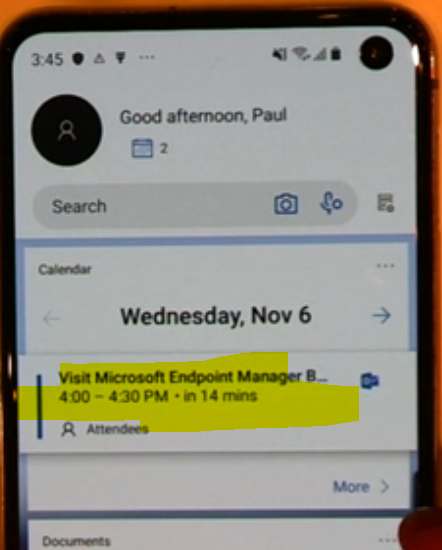
 You can also enable a Feed for your organization with Microsoft Launcher. This allows you to inform your end users about what they need to know about, for example a calendar appointment.
You can also enable a Feed for your organization with Microsoft Launcher. This allows you to inform your end users about what they need to know about, for example a calendar appointment.
 The home screen can be configured by the admin with apps that the user cannot remove, but the user can add say, web links to customize their home screen.
The home screen can be configured by the admin with apps that the user cannot remove, but the user can add say, web links to customize their home screen.
Apps on a company owned device
As this is a company owned device, access to the Google play personal store is not allowed and the end user will only see their Work account listed when they click on the hamburger.
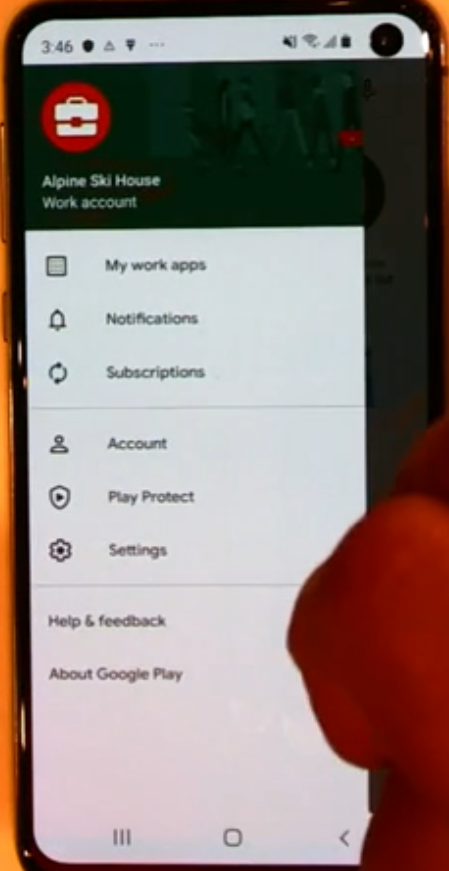 And regarding apps, as this is a company owned device if the user decides to install a company app, then the admin can configure it to only allow the profile of the end user to be installed.
And regarding apps, as this is a company owned device if the user decides to install a company app, then the admin can configure it to only allow the profile of the end user to be installed.
 So the end user can only click on Add Account in this example as you’ve already per-configured everything for them.
So the end user can only click on Add Account in this example as you’ve already per-configured everything for them.


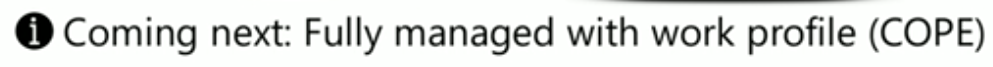

Pingback: Android device management with Microsoft Intune – Part 1. Partnerships | just another windows noob ?
Pingback: Android device management with Microsoft Intune – Part 3. Dedicated device management | just another windows noob ?
Pingback: Android device management with Microsoft Intune – Part 4. Coming soon and what’s new | just another windows noob ?