Introduction
This is a quick post to highlight a small update to my Install SQL Server 2017.ps1 script used to install SCCM 1902 with SQL Server 2017 on Windows Server 2019 published recently. I’ve added a new section to deal with the TLS 1.2 prerequisite check that creates a warning for the SQL Server 2012 Client agent version that is installed as part of the SQL Server 2017 installation.
By default, after installing SQL Server 2017 even with Cumulative Update 14, the SQL Server client agent is at a version that does not properly support TLS 1.2 for SCCM, so we need to upgrade it. You need a client agent with version 11.4.7001.0 or later to support TLS 1.2.
Note: The SQL client agent update (QFE) is available for manual download here.
To resolve that I wrote the following PowerShell script which is now updated into the original script, it will verify your SQL Server Client agent version, and if it doesn’t match this it will download and upgrade it (or use the previously downloaded file if you provide it).
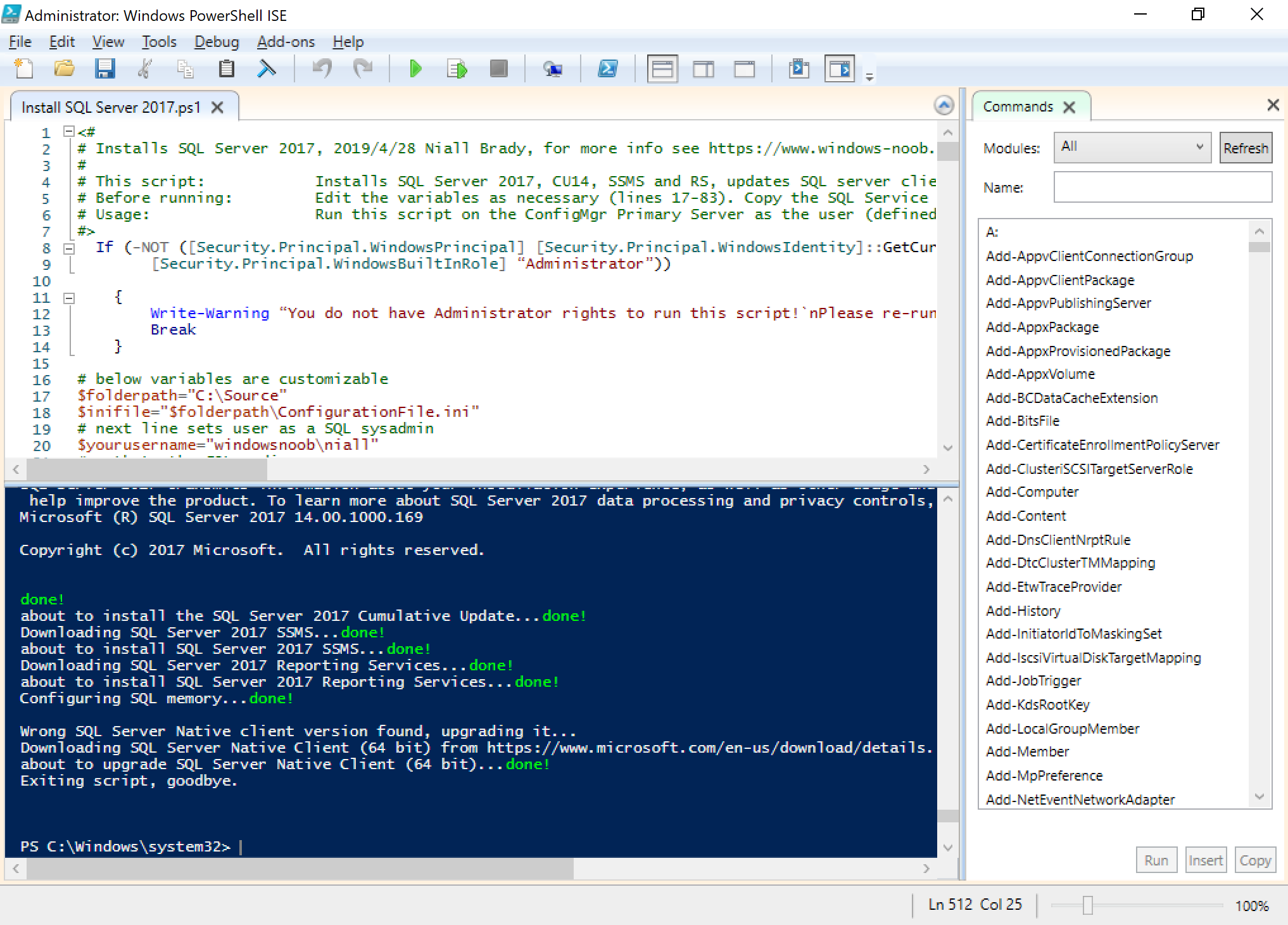
Here you can see the SQL Server installation script has run and updated the SQL Server native client agent version as part of the installation.
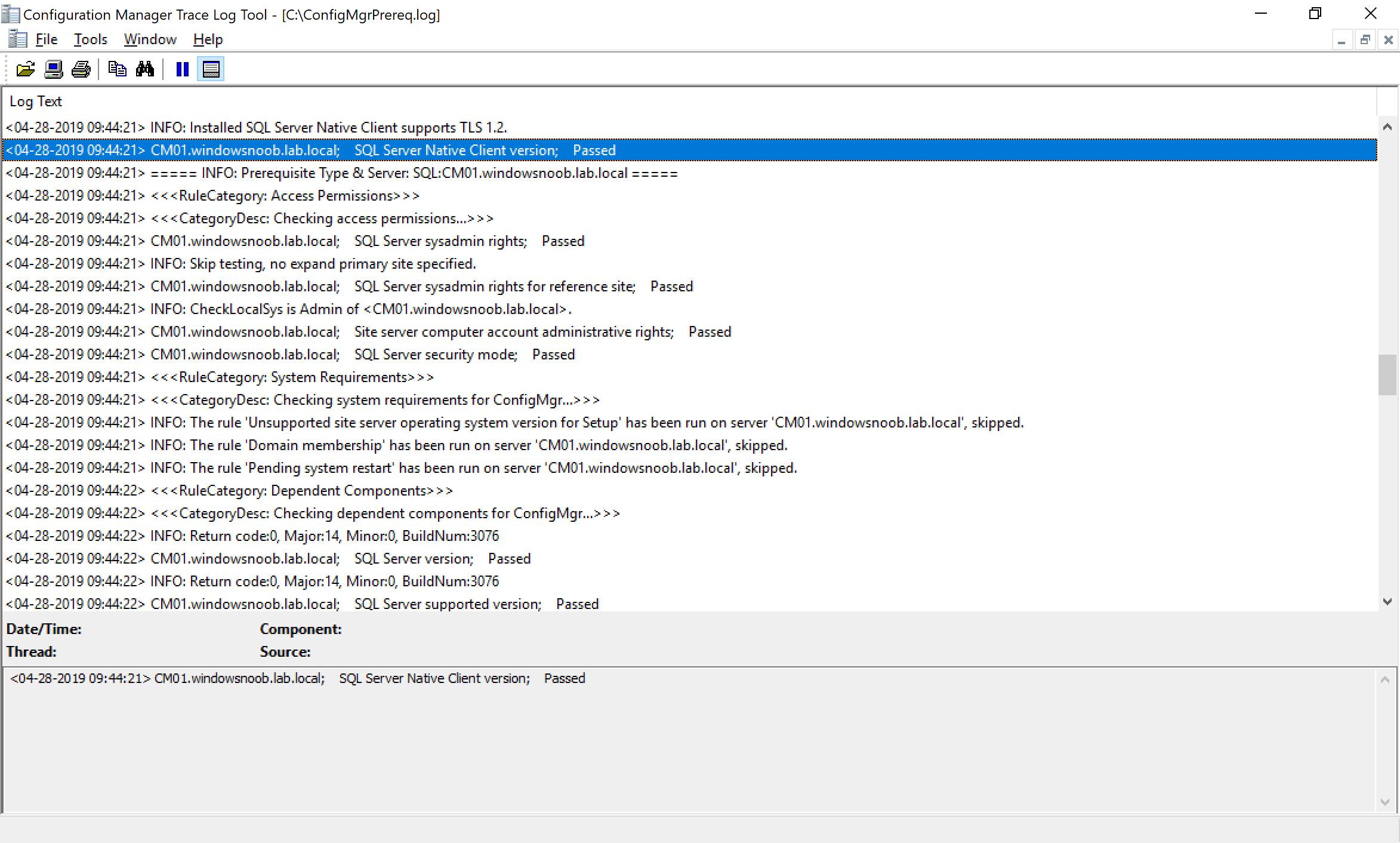
 And that means that the SCCM installer will be happy when checking for that specific prerequisite, as you can see it states “Passed”.
And that means that the SCCM installer will be happy when checking for that specific prerequisite, as you can see it states “Passed”.
Here’s the code that updates the SQL Server Client Agent, for anyone that is interested, note that if you run this separately you’ll need to reboot the server prior to installing SCCM.
# Update the SQL Server 2012 Native Client (installed with SQL Server 2017) to support TLS 1.2 - added by Niall Brady 2019/4/28
# niall brady, 2019/4/28 https://www.windows-noob.com/forums/topic/16614-how-can-i-install-system-center-configuration-manager-current-branch-version-1902-on-windows-server-2019-with-sql-server-2017-part-1/
#
$folderpath="C:\Source"
# Checking SQL Server Native Client in registry
$Results = Get-ItemProperty "HKLM:\SOFTWARE\Microsoft\Microsoft SQL Server\SQLNCLI11\CurrentVersion"| Select-Object Version
If ($Results.Version -lt "11.4.7001.0")
{write-host "Incorrect SQL Server Native client version found, upgrading it..."
# start the SQL Server Native Client downloader
$filepath="$folderpath\sqlncli.msi"
if (!(Test-Path $filepath)){
write-host "Downloading SQL Server Native Client (64 bit) from https://www.microsoft.com/en-us/download/details.aspx?id=50402 ..." -nonewline
$URL = "https://download.microsoft.com/download/B/E/D/BED73AAC-3C8A-43F5-AF4F-EB4FEA6C8F3A/ENU/x64/sqlncli.msi"
$clnt = New-Object System.Net.WebClient
$clnt.DownloadFile($url,$filepath)
Write-Host "done!" -ForegroundColor Green
}
else
{
write-host "found the SQL Server Native Client (64 bit), no need to download it..."
}
# start the SQL Server Native Client (64 bit) upgrade...
write-host "about to upgrade SQL Server Native Client (64 bit)..." -nonewline
$arguments = "/i `"$filepath`" /quiet IACCEPTSQLNCLILICENSETERMS=YES"
# to do, add logging...
# /L*V C:\Windows\temp\SQLNativeClient11\sqlNativeClientInstall.log
Start-Process msiexec.exe -ArgumentList $arguments -Wait
Write-Host "done!" -ForegroundColor Green
}
else
{write-host "SQL Server Native Client (64 bit) is an ok version for TLS 1.2, no need to update it."}
Recommended reading
- https://blogs.technet.microsoft.com/arnabm/2018/11/28/sql-server-native-client-update-warning-prerequisite-for-configmgr-1810/
- https://support.microsoft.com/en-us/help/3135244/tls-1-2-support-for-microsoft-sql-server
- https://support.microsoft.com/en-us/help/4040243/how-to-enable-tls-1-2-for-configuration-manager
- https://docs.microsoft.com/en-us/sccm/core/servers/deploy/install/list-of-prerequisite-checks#sql-native-client
- https://www.windows-noob.com/forums/topic/16614-how-can-i-install-system-center-configuration-manager-current-branch-version-1902-on-windows-server-2019-with-sql-server-2017-part-1/