Introduction
Microsoft blogged about Bitlocker Management capabilities back in May, 2019. They detailed how that would impact and evolve on the following three platforms.
- Cloud-based BitLocker management using Microsoft Intune
- On-premises BitLocker management using System Center Configuration Manager
- Microsoft BitLocker Administration and Monitoring (MBAM)
And recently they’ve posted an updated blog post here where they go into detail about how BitLocker Management in Microsoft Endpoint Manager has evolved (both in Intune and ConfigMgr). This purpose of this mini series is to help you troubleshoot problems related to the installation, configuration and usage of the new BitLocker Management capabilities in ConfigMgr and will be broken down into the following 3 parts.
- Troubleshooting BitLocker Management in ConfigMgr – Part 1. Server side
- Troubleshooting BitLocker Management in ConfigMgr – Part 2. Client side(this part)
- Troubleshooting BitLocker Management in ConfigMgr – Part 3. Common issues
In the previous part we created a BitLocker Management policy, but we did not deploy it. This was enough to start the flow of how things work on the server side. But let’s focus on the client side for now and in this blog post we will look at a Windows 10 20H2 client. As Windows 10 20H2 is a newly released operating system, we need to use ConfigMgr 2006 to remain supported. Let’s take a look at some client computers both before and after they receive BitLocker Management policy from ConfigMgr.
Before BitLocker Management policy
Before a client receives BitLocker Management policy, it can be in one of 2 states with regards to encryption, namely fully encrypted or fully decrypted. If the computer has not been targeted with BitLocker policy and is for whatever reason decrypted, then the hard disc drives data will be readable at rest (not protected). I’ve prepared 2 virtual machines running Windows 10 20H2 and neither virtual machine has received our previously configured BitLocker Management policy yet, however one vm is encrypted using a different encryption algorithm than the one we created in the previous blog post, this is so that we can see what occurs when it receives that policy.
Both are running Windows 10 version 20H2 with the ConfigMgr client agent version 5.00.9012.1020.
Note: I manually encrypted one of the two virtual machines with XTS-AES 128 using the following:
cmd /c reg.exe add HKLM\SOFTWARE\Policies\Microsoft\FVE /v EncryptionMethod /t REG_DWORD /d 6 /f & manage-bde -on c:
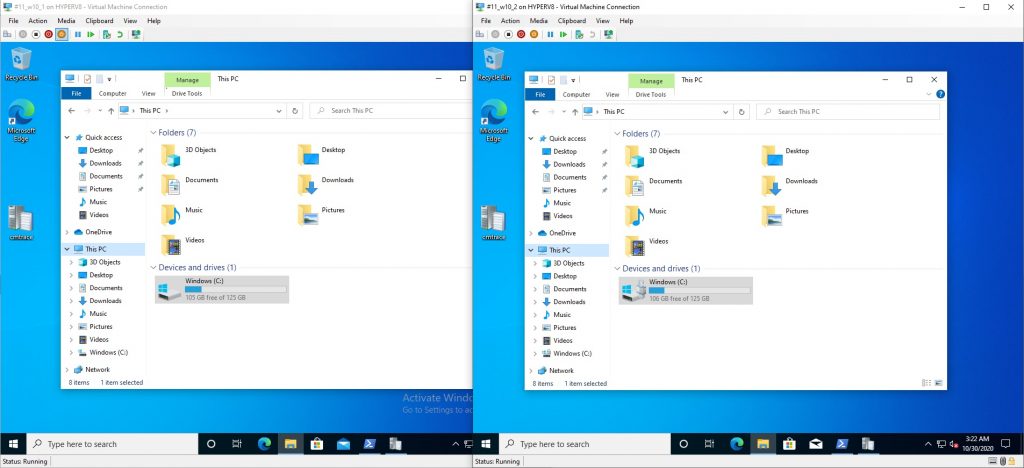
Opening Windows File Explorer on both vm’s show’s that clearly the vm on the right is encrypted, while the vm on the left is not.
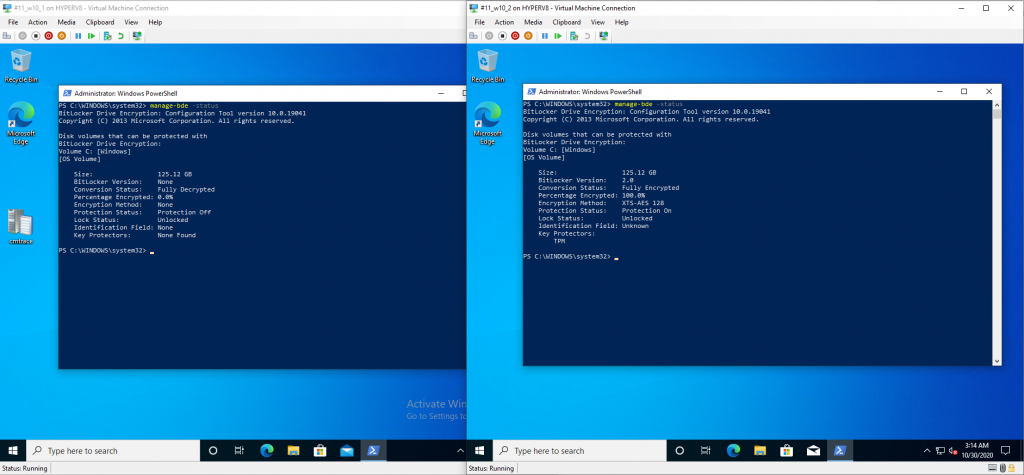
Using manage-bde -status reveals details about the encryption (or decryption) on both vm’s.
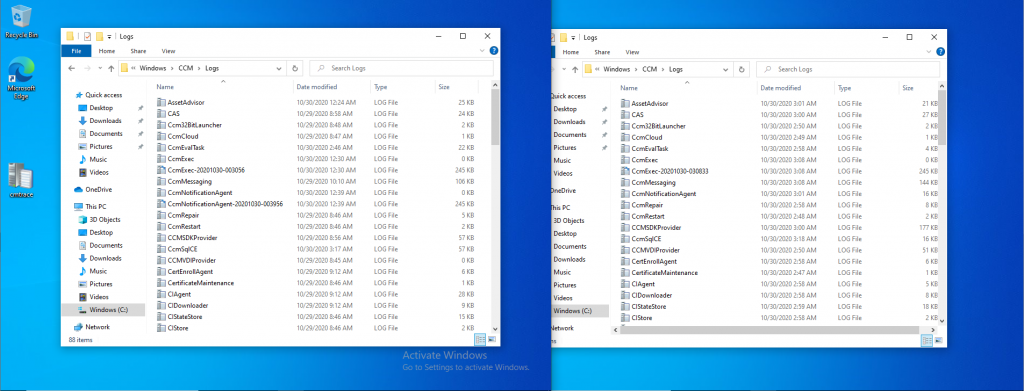
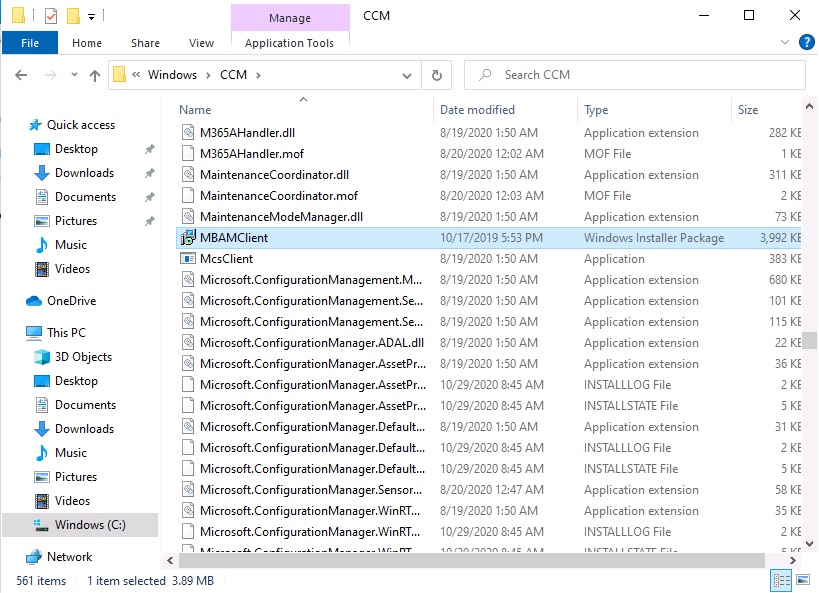
Neither VM contains BitLocker Management policy based logs in C:\Windows\CCM\Logs
and we can see that there is no BitLocker Management related policy shown in the ConfigMgr client agent on either of the two virtual machines
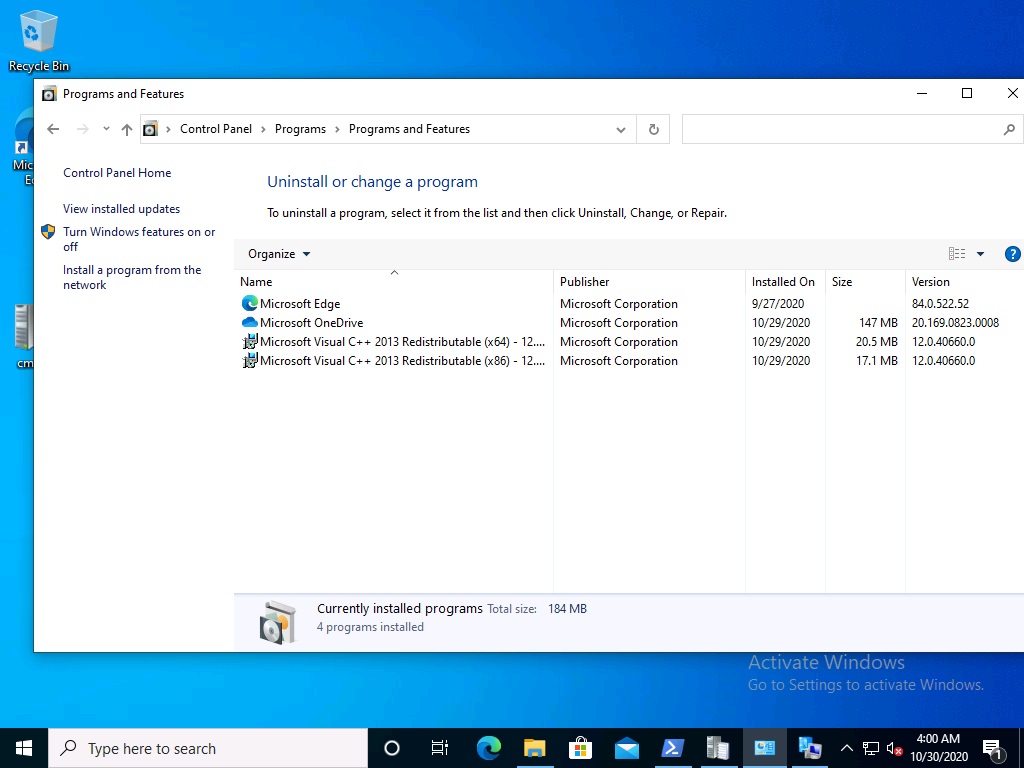
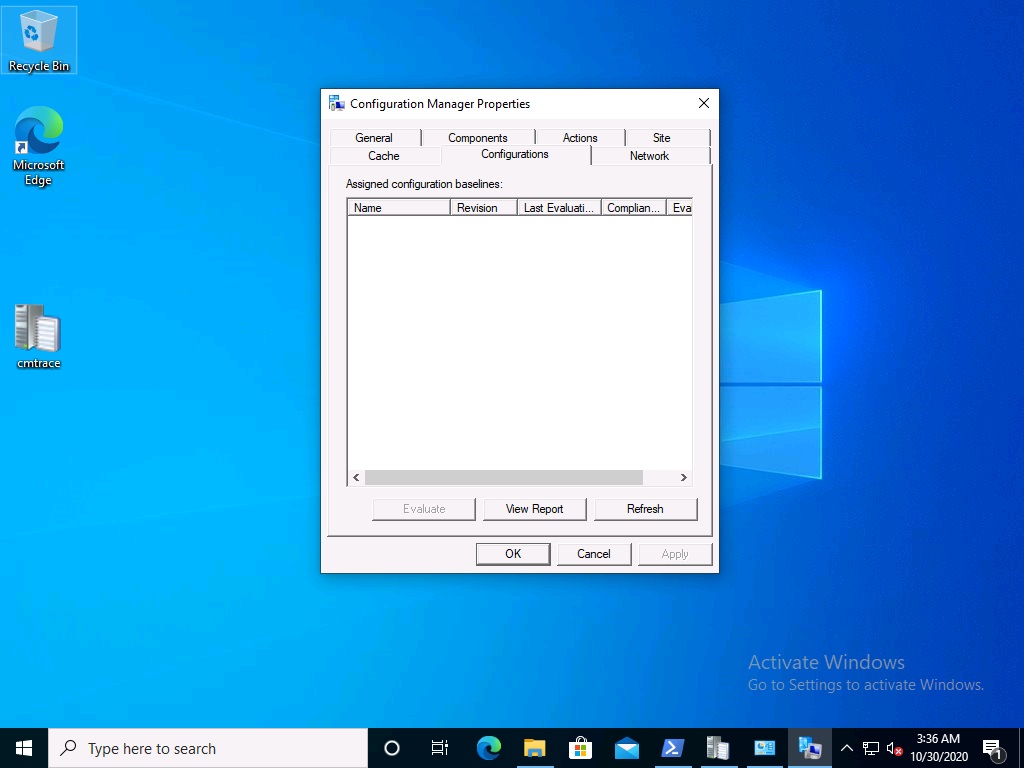 A quick check of programs installed, reveals that the MDOP MBAM client Agent is not installed on either Virtual Machine. This agent is responsible for interpreting the BitLocker Mangement policy settings and acting accordingly.
A quick check of programs installed, reveals that the MDOP MBAM client Agent is not installed on either Virtual Machine. This agent is responsible for interpreting the BitLocker Mangement policy settings and acting accordingly.
This MDOP MBAM client agent installation file (MSI) is present in the ConfigMgr client agent files path (C:\Windows\CCM\MBAMCLIENT.MSI) even when the no BitLocker Management policy is deployed to the client.
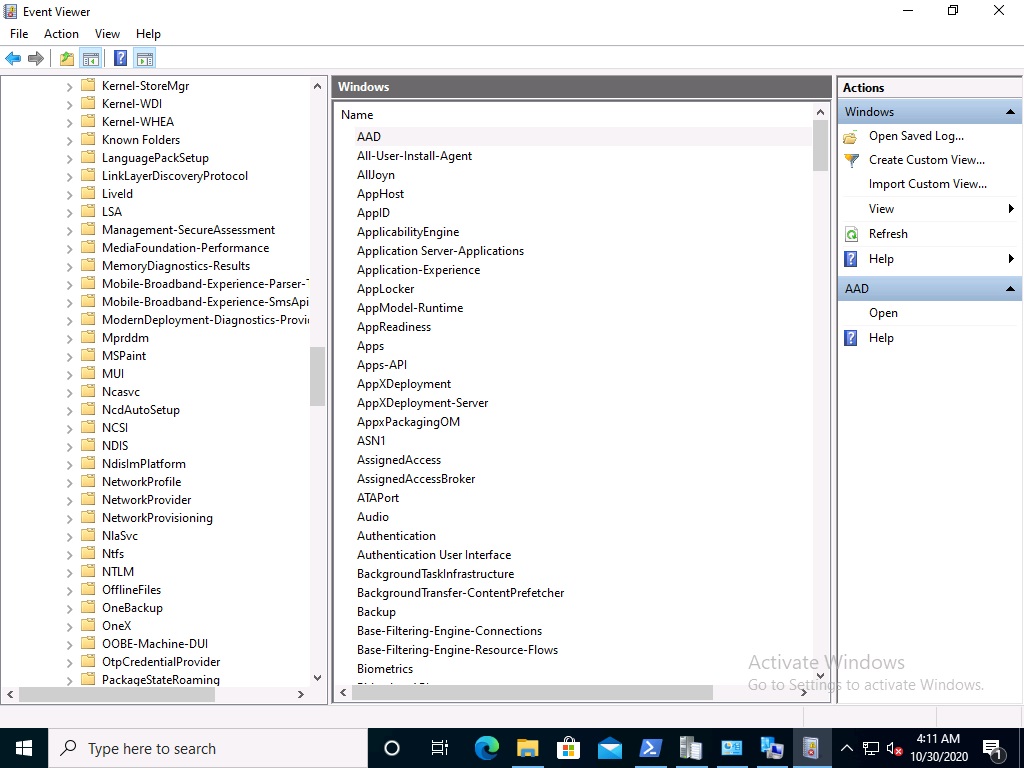
There will be no MBAM related events (or folders) in the Event Viewer at the following path Applications and services logs\Microsoft\Windows\
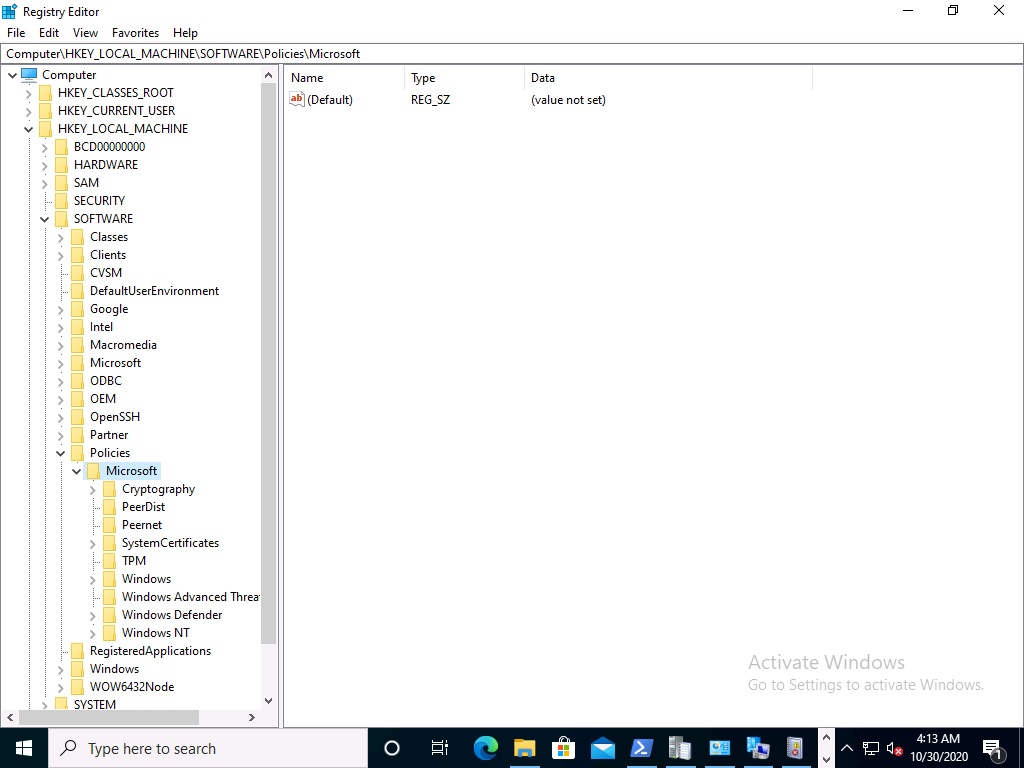
And there will be no FVE\MDOPBitLockerManagement registry entries in Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft
You can read the rest of this blog post here



Hi! I’m late to the party but about to deploy bitlocker through cm. One thing I found was a few in my testing did not encrypt automatically despite the registry settings used to kick it into motion immediately. But I could go ahead and kick the bitlocker encryption process via manage-bde cmd. I noticed on those that the keys did not go up to the cm db. Searched the internet on a way to force cm to write that data after the fact and didn’t find an answer but after digging through the cm registry found one that works. On the pc having issues, use manage-bde -protectors -get c: cmd and get your volume id. Then, go to HKLM\software\microsoft\ccm\blm\escrowed\volumeid. Change the keyescrowed value to 0 and at next checkin, you should see it update the db.
hi,
if your devices are not encrypting automatically then you need to verify your settings and verify they are getting policy,
start with policy, did you verify they are seeing it ?