In part 1 of this series, you configured your LAB for a 2 tier PKI hierarchy running on Windows Server 2016. You used PowerShell to create some virtual machines, and then installed Windows Server 2016, Windows 10 Enterprise version 1803 and optionally Smoothwall 3.1 before configuring the IP address scheme and Computer Names on the virtual machines. Finally you configured ADDS on DC01 so that you have a working Domain Controller for the rest of this LAB. In part 2 you installed and did the initial configuration on the Standalone Offline Root CA. In part 3 you prepared the HTTP Web Server for CDP and AIA Publication and you created a DNS record for the publicly available web server.
Now you will perform post configuration on the Standalone Offline Root CA to set certificate revocation list (CRL) period registry settings using CertUtil, and then enable object access Auditing and finally, to configure three locations for the Authority Information Access (AIA) and four locations for the Certificate revocation list Distribution Point (CDP), again using CertUtil.
Step 1. Configure CRL period registry settings using CertUtil
Certutil.exe is a command-line program that is installed as part of Active Directory Certificate Services. You can use Certutil.exe to set or get certification authority (CA) configuration information, configure Certificate Services, backup and restore CA components, and verify certificates, key pairs, and certificate chains(1).
In this step, you’ll use CertUtil to set various related registry settings for the Certificate Revocation List periods in the registry on the Standalone Offline Root CA. Logon to the Standalone Offline Root CA as RootCA\Administrator. Right-click on Start, and choose Command Prompt (admin).
I’ll show screenshots of the output of each command separately so that you can compare it to your environment. To start off, you need to define the Active Directory Configuration Partition Distinguished Name, and to do that using certutil enter the following command:
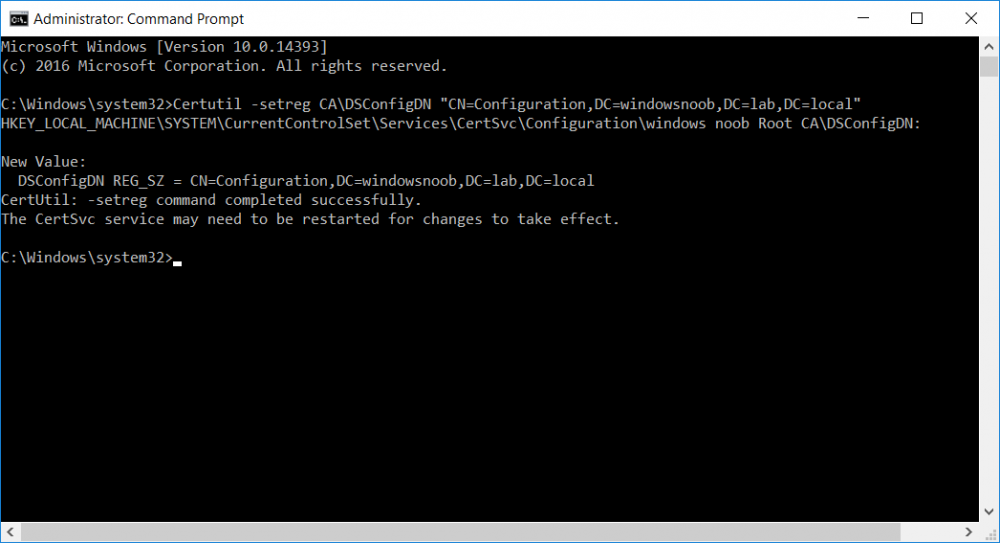
Certutil -setreg CA\DSConfigDN "CN=Configuration,DC=windowsnoob,DC=lab,DC=local"
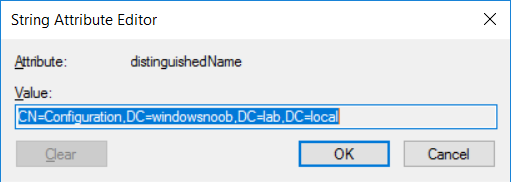
Note: You can determine what the configuration path should be (for your LAB) for the command above by logging on to the Domain Controller (DC01), and by opening Adsi Edit, and click on Action then select Connect to. In the window that appears, change Select a well known naming context to Configuration. In the Adsi Edit pane, right click on CN=Configuration,DC=windowsnoob,DC=lab,DC=local and choose Properties, scroll down and double click on Distinguished Name, copy the Value listed in the String attribute editor.
The results of the certutil -setreg command on the Standalone Offline Root CA are shown below. Be sure that it states CertUtil: -setreg command completed successfully.
Next you will define the Certificate Revocation List (CRL) Period Units, CRL Period and CRL Delta Period Units. To do so run the following commands from an administrative command prompt:
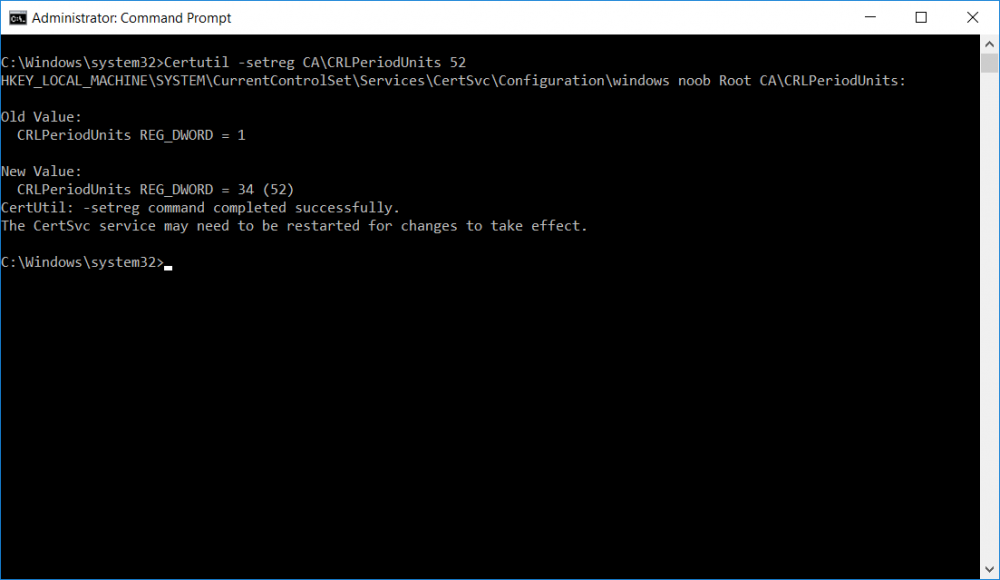
Certutil -setreg CA\CRLPeriodUnits 52
Press Enter. The output of the above command is shown below.
Certutil -setreg CA\CRLPeriod "Weeks"
Press Enter. The output of the above command is shown below.
You can read the rest of this guide @ windows-noob.com here.