Introduction
The Surface Pro 3 is awesome, and you can deploy it easily using System Center 2012 R2 Configuration Manager, but sometimes things don’t go as planned. If you notice that the hard drive is not BitLockered even though you Enabled BitLocker in the task sequence, then you most likely have the issue described below.
Problem
Bitlocker doesn’t encrypt the drive. This is immediately obvious when you browse the C: drive.
 And become’s more obvious when you review the SMSTS.log file with all the errors shown below in red for the Enable BitLocker step.
And become’s more obvious when you review the SMSTS.log file with all the errors shown below in red for the Enable BitLocker step.
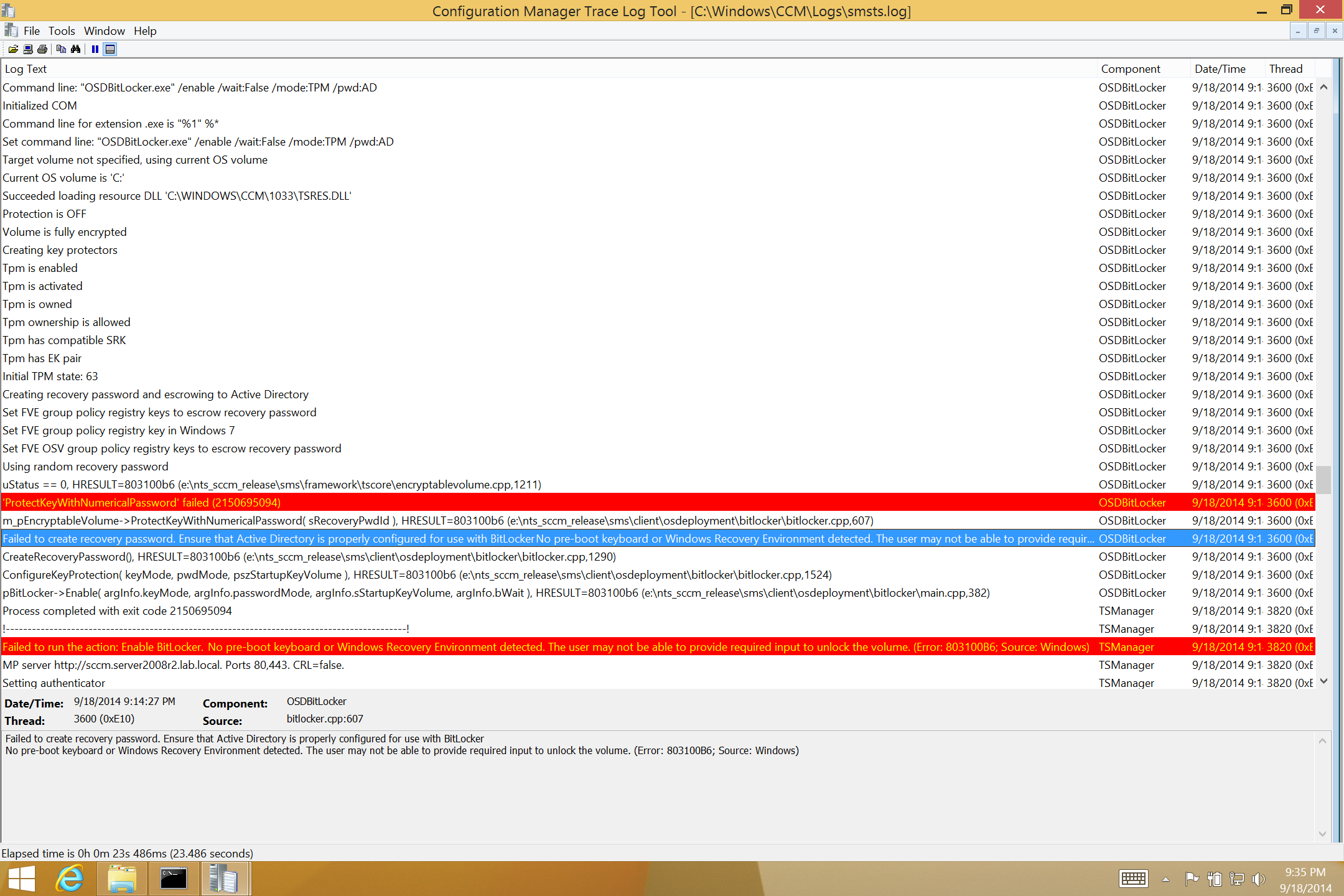 You’ll see errors like below:-
You’ll see errors like below:-
Failed to run the action: Enable BitLocker.
No pre-boot keyboard or Windows Recovery Environment detected. The user may not be able to provide required input to unlock the volume. (Error: 803100B6; Source: Windows)Failed to run the action: Enable BitLocker.
No pre-boot keyboard or Windows Recovery Environment detected. The user may not be able to provide required input to unlock the volume. (Error: 803100B6; Source: Windows)
Solution
The Surface Pro 3 is a tablet/hybrid device which can have a keyboard attached (or not). As a result it’s treated differently than say a standard Laptop or Desktop when it comes to BitLocker (due to the fact that a keyboard may or may not be attached, and it might be needed for TPM/Pin authentication).
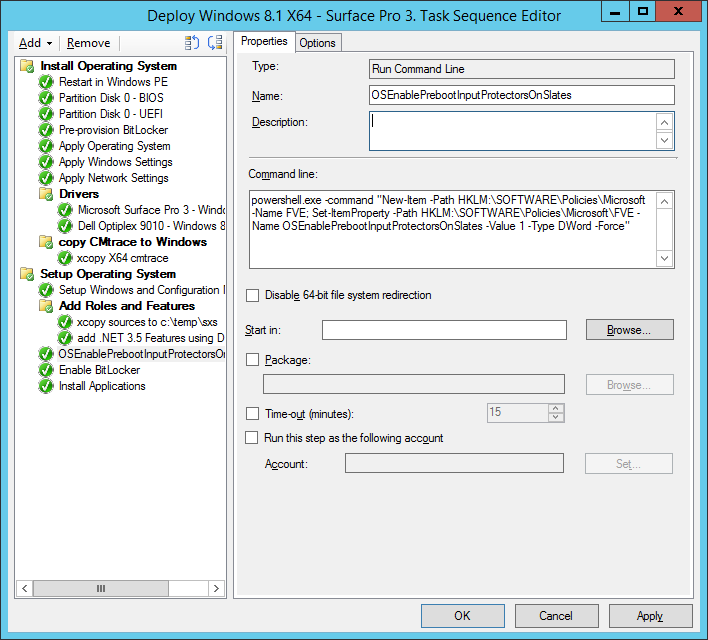
To resolve the above, simple add a registry key, you can do it the old fashioned way by adding a Run Command Line step in the task sequence BEFORE the Enable Bitlocker step to set the reg keys.
The registry key is located under HKLM\SOFTWARE\Policies\Microsoft\FVE\OSEnablePrebootInputProtectorsOnSlates and should have a value of 1
Or you can do like the PowerShell dudes do and do it in PowerShell, using the following line
powershell.exe -command "New-Item -Path HKLM:\SOFTWARE\Policies\Microsoft -Name FVE; Set-ItemProperty -Path HKLM:\SOFTWARE\Policies\Microsoft\FVE -Name OSEnablePrebootInputProtectorsOnSlates -Value 1 -Type DWord -Force"
like so
once the above is in place your deployment will Enable BitLocker properly and your C: drive will look the way you’d expect.
The following links should help you with Deploying Windows 8.1 X64 on the Surface Pro 3
- CM12 in a Lab – Where do I find the MAC address of my Surface Pro 3 Ethernet Adapter in order to use UEFI network boot ?
- CM12 in a Lab – How can I deploy Windows 8.1 x64 to the Microsoft Surface Pro 3 using System Center 2012 R2 Configuration Manager ?
- CM12 in a Lab – Why does my Surface Pro 3 take a very long time to UEFI Network Boot using System Center 2012 R2 Configuration Manager ?
- CM12 in a Lab – How can I sync the BIOS date in WinPE to avoid PXE boot failure with System Center 2012 R2 Configuration Manager ?
- http://netecm.netree.ch/blog/Lists/Posts/Post.aspx?ID=80#.VBtGeRbaVdg
until next time, cheers !
niall.



Pingback: how can I add support for Pen Pairing during OOBE on a Surface Pro 3 using System Center 2012 R2 Configuration Manager | just another windows noob ?
Pingback: New Surface Pro 3 drivers are available for November 2014 | just another windows noob ?
Pingback: Can you PXE boot a Surface Pro 3 without a Microsoft USB nic ? yup and here’s how | just another windows noob ?
Pingback: A list of Surface Pro 3 resources for both MDT 2013 and System Center 2012 R2 Configuration Manager | just another windows noob ?
Awesome. This just worked for My HP Revolve 810 G1’s I have in production